Guide
A Comprehensive Guide to Operational Technology (OT) Cybersecurity
As data collection and analysis become more important, and as IT and OT converge to enable “big data” initiatives, it has become necessary to reassess cybersecurity best practices for protecting OT.
Table of Contents
Maintaining control of all physical assets to ensure their safe operation at all times is the primary objective of OT cybersecurity and overrides all other concerns. If a facility cannot be run safely, then it will not be run at all.”
What is Operational Technology (OT) Cybersecurity?
Operational technology (OT) cybersecurity references the software, hardware, practices, personnel, and services deployed to protect operational technology infrastructure, people, and data. As data collection and analysis become more important, and as IT and OT converge to enable “big data” initiatives, it has become necessary to reassess cybersecurity best practices for protecting OT.
OT History and Definitions
The need for industrial controls arose with the first Industrial Revolution of the 1700s. Converting steam into usable energy was difficult and dangerous; it took decades to perfect a governor that could control the speed of steam engine output to truly tame this new power source. Each subsequent industrial revolution (we are currently into the fourth) has driven, or was driven by, further developments in controls on physical systems.
The Last Modern Era: Third Industrial Revolution
A major advance in industrial controls was the ability to automate multiple steps in a manufacturing process. To enable this type of operation, engineers developed electrically operated on/off switches, called relays, which could be combined to perform logical operations. This type of control logic appeared on manufacturing lines as early as 1900.
Relays work great, but to modify the logic you had to rip out the hardware stack and re-wire it with a new relay configuration. Even if you only had to do this once a year, say when moving to a new product model on a production line, it was costly and time-consuming.
Programmable Logic Controllers (PLCs)
The programmable logic controller (PLC), first designed in 1971, was created as a replacement for traditional relay stacks. PLCs applied electronics to production automation for the first time, thereby launching the third Industrial Revolution. The invention of the PLC made creating and modifying control logic much easier, and it quickly became the foundation for simple but powerful control loop systems, which consist of a sensor, controller (e.g., PLC), and actuator.
Control Systems
From these simple process loops, very complex behavior can be modeled and controlled with nested and/or cascading architectures. Logic can be built to control continuous manufacturing processes, such as those found in a refinery or chemical plant, and batch manufacturing processes, such as is found on an assembly line. Control systems also found their way into distributed applications such as electrical power grids, railways, and pipelines.
Supervisory Control and Data Acquisition (SCADA) Systems and Distributed Control Systems (DCS)
Often in distribution system applications, data acquisition is as important as control. Historically, Supervisory Control and Data Acquisition (SCADA) systems have been used to integrate data acquisition systems (sensors) with data transmission systems and data presentation solutions that support Human-Machine Interface (HMI) software, creating centralized visibility into an entire system, such as an electric grid.
Distributed Control Systems (DCS) provide a similar set of functionalities as SCADA but on the scale of a factory, and typically with less complexity, or at least diversity, in networking and communications channels.
Industrial Control Systems (ICS) and Operational Technology (OT)
All of the technologies we have discussed have historically been rolled up under the heading of industrial control systems (ICS). However, use of the term operational technology (OT), in contradistinction to IT, has become popular in recent years. The analyst firm Gartner defines OT as:
“Hardware and software that detects or causes a change through the direct monitoring and/or control of physical devices, processes and events in asset-centric enterprises, particularly in production and operations.”
This definition makes it clear that the distinction between OT and ICS is not so much in the core functionality of OT but more in the recognition of an evolving definition of “asset-centric” enterprises, with OT now finding application far beyond the traditional “industrial” industries where ICS has found a home for the last 50 years.
Internet of Things (IoT) and Industrial Internet of Things (IIoT)
Another relatively new term, and one that overlaps considerably with OT, is Internet of Things (IoT). Like OT, IoT utilizes devices such as actuators and sensors. But IoT architectures are fairly streamlined compared with OT. Typically, an IoT system would consist of endpoint devices connected to an edge gateway, which in turn would connect to cloud services. IoT technologies are often deployed in commercial or even consumer environments, but when applied to industrial applications, they are referred to as the Industrial Internet of Things (IIoT).
Examples of IoT devices include:
- Electricity/Gas/Water Smart Meters
- Smart Home
- Building Automation
- Vehicle Head Unit
- Security & Fire Alarms
- Inventory Management
- CCTV
- Healthcare Monitoring
- Assisted Living Monitoring
IoT leverages several new technologies that have significantly reduced the difficulty and cost of deploying monitoring and control systems, particularly in highly geographically distributed environments. These technologies include real-time analytics, commodity sensors, sophisticated embedded systems, cloud storage and computing, and 5G networks. The sophistication of analytics, the ubiquity of bandwidth—wired and wireless—and the low price of data storage and compact multi-purpose sensors have all converged to make it much cheaper and easier to collect, analyze and act, on massive amounts of data about the world around us.
Cyber-Physical Systems (CPS)
Another term that is worth remembering is Cyber-Physical System (CPS). Gartner defines CPS as a collection of systems that interact with the physical world through cyber environments. The term is intended to encompass a broader set of applications than traditional OT. Examples include autonomous automobile systems, automatic pilot avionics, and smart grids. Again, all of these terms overlap to some degree and their distinctions in practice can often be found in how they are architected or to whom they are being sold.
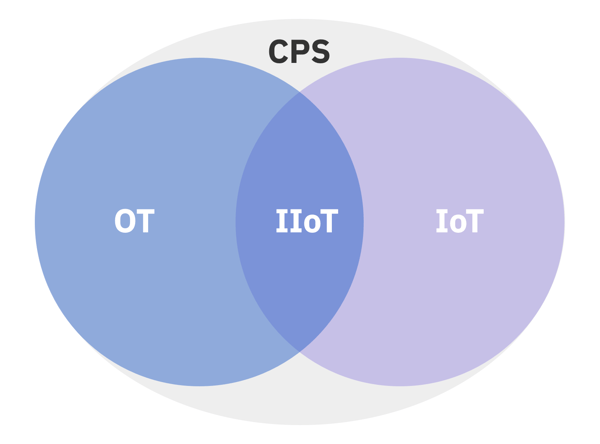
Figure 1: The Relationship Between CPS, OT, IoT, and IIoT
The Fourth Industrial Revolution
All of these technologies and trends are driving a fourth Industrial Revolution, which is often referred to as Industry 4.0. The European Union (EU) has been particularly active in investments to enable this advance. The EU views Industry 4.0 as a true “paradigm shift” that will drive sustained competitive advantage.
These technology trends are converging on OT and driving a rethinking of strategies. In fact, a November 2019 Gartner survey of OT operators found that 59% believed IoT adoption is likely to augment or replace most or all of their OT monitoring and control systems within 36 months. In light of this, an overview of the current vendor landscape for IoT products and services is warranted.
Global Goldrush into IoT
Every major technology company in the world is either a consumer of IoT, a provider of IoT, or both. Because most of these products and services are being sold well beyond the traditional “industrial” customer base, they are typically marketed as IoT solutions rather than IIoT solutions.
All of the major cloud and edge computing providers have introduced solutions specifically tailored to IoT. These include Amazon Web Services (AWS), Google, Microsoft, and IBM.
- AWS IoT
- Google Cloud IoT
- IBM Watson IoT Platform
- Microsoft Azure IoT Hub
There are currently hundreds of vendors providing some type of IoT product or service. Many are providing traditional middleware functionality to connect sensors to analysis and control applications. (This includes the cloud providers listed above.)
This middleware communicates down through an IoT gateway to manage IoT devices. Typical functionality supported within the platform includes data collection, device management, configuration management, messaging, and software management. These middleware platforms also push device data up to reporting, visualization, analytics, and alerting applications.
Some additional IoT platforms to be aware of include:
- Alibaba Cloud IoT
- AT&T M2X
- Bosch IoT Suite
- Cisco Kinetic
- Deutsche Telekom Cloud of Things (CoT)
- GE Digital Predix Platform
- Huawei OceanConnect
- Oracle IoT Cloud
- SAP Leonardo IoT
- Schneider Electric EcoStruxure
- Siemens MindSphere
- Software AG Cumolocity IoT
- Verizon ThingSpace
Vendors are jumping into the IoT space from the traditional IT equipment space as well as from the carrier infrastructure space and include market leaders such as Dell, Ericsson, Fujitsu, Hitachi, HP Enterprise, Intel, Qualcomm, and Samsung.
Building a Business Case for OT Cybersecurity
The business case today for continuing to modernize OT is the same it has been for more than 200 years: getting things done faster, more safely and efficiently, and at a lower cost. The benefits of OT investments cannot be overstated. Historically, OT has been one of the great contributors to improving quality of life by enabling the economical and safe delivery of clean water, energy, and wastewater treatment, as well as the production of many of life’s manufactured staples. It is therefore not surprising that OT functionality is finding a wider audience beyond its traditional industrial base. The benefits of monitoring and controlling our physical environment are increasingly attractive to commercial enterprises, governments, and even consumers. But the cybersecurity concerns associated with OT have never been higher as the ability to isolate OT systems becomes increasingly difficult.
Cybersecurity Concerns with IT and OT Integration
The broad adoption of sophisticated enterprise software, particularly big data analytics, has prompted organizations to further integrate traditional IT systems and traditional OT infrastructure. Connecting industrial systems to an IT network allows a more detailed view of individual equipment and creates a comprehensive view of the entire industrial ecosystem, simplifying management and operation. This enables constant monitoring of the performance and condition of equipment and systems, which improves uptime. These benefits are compelling and explain the explosion of interest in IT/OT integration.
The Need for OT Cybersecurity has Grown Significantly
“Complete isolation has become all but impossible today, however, and to mitigate new risks to OT, organizations will need to deploy a combination of traditional IT cybersecurity products and services with tailored, OT-specific cybersecurity solutions.”
But with these benefits come greater complexity, increased risks, and an expanded attack surface. The situation is similar to when organizations first embraced IT 30 years ago and then quickly realized that a host of cybersecurity concerns needed to be understood and addressed.
Traditional OT systems bring with them a long list of cybersecurity concerns, including equipment with decades-long life cycles, an inability to patch systems due to stability concerns, and a lack of basic cybersecurity features such as user authentication or encryption. In the idealized past, where such systems were “air-gapped” to ensure perfect isolation from the rest of the world, these concerns were assumed to carry acceptable risk. Complete isolation has become all but impossible today, however, and to mitigate new risks to OT, organizations will need to deploy a combination of traditional IT cybersecurity products and services with tailored, OT-specific cybersecurity solutions.
Business Rationale for OT Cybersecurity
The business case for adopting OT cybersecurity controls should apply the same risk management calculation that was used to adopt OT. The threat of cyberattack is an important additional component to consider when evaluating the risk associated with disruption to operations. Although less of a concern for traditional OT users, protecting data confidentiality is also a consideration. Later in this report, we will drill into the differing historical priorities and goals of IT cybersecurity and OT cybersecurity practitioners.
The International Society of Automation (ISA) standard Security for Industrial Automation and Control Systems: Establishing an Industrial Automation and Control Systems Security Program (ISA-62443-2-1) provides useful guidance for developing a business rationale for OT cybersecurity investments. It recommends a focus on four key areas:
-
Key Area One
Consequences
What are the possible negative business consequences of a cyber attack?
-
Key Area Two
Threats
What is the actual threat environment for your organization?
-
Key Area Three
Recovery
What is the estimated cost to recover from a cyber attack?
-
Key Area Four
Investment
What is the cost for OT cybersecurity products or services?
The negative business consequences of a cybersecurity attack are numerous. Business consequences to consider include public health and safety, business continuity, disaster recovery, regulatory compliance, public confidence, and the environment. It is easier to assign hard numeric costs for some (e.g., outages, equipment damage) than others (e.g., damage to reputation, customer dissatisfaction), but all costs should be estimated.
“While some organizations have to take the possibility of nation-state attacks seriously, most should focus more on the possibility of attacks by disgruntled employees and/or ex-employees.”
The threat environment that an organization faces depends on a range of factors, some of which are hard to predict or could change rapidly for geopolitical or other reasons that are outside the control of the organization. It is impossible to protect against all potential threats, so prioritization of threats is required before determining security control needs.
While some organizations have to take the possibility of nation-state attacks seriously, most should focus more on the possibility of attacks by disgruntled employees and/or ex-employees. Some organizations have OT in production environments that introduce unique technical vulnerabilities, which would introduce specific threats. Prioritizing threats based on the likelihood of exploitation helps to build a case for managers with respect to which threats have the largest potential impact on the business.
The costs of any potential attacks should also be estimated. In making a business case, it will be more impactful if actual dollar amounts can be associated with each potential attack. Obviously, no decent business case would suggest spending more money on defending against an attack than the attack would be estimated to cost.
Knowing the most likely attack scenarios for a given organizational infrastructure provides a solid starting point for building a security reference architecture that can hopefully protect against such attacks. Knowing the potential costs of those attacks helps to build the business case for purchasing and deploying the right security controls.

How to Jump-Start the Cyber Insurance Market to Drive Better OT Security
Read the ArticleWhat is the Purdue Enterprise Reference Architecture?
The Purdue Enterprise Reference Architecture was created in the mid-1990s and quickly found broad industry acceptance as a means to understand the required hierarchical structure of OT systems. It is incorporated into the ANSI/ISA-95 standard, which maps the interconnections and interdependencies of the high-level components of a typical industrial control system (ICS).
Purdue Model Levels
By first providing an overview of the original zones and levels in the model, we can see how some modern IT technologies are making it much more difficult to enforce the model’s tenets. The current Purdue architecture models OT and IT into six functional levels that run from Level 0 to Level 5 and span three zones.
|
Level 0 |
This is the physical equipment that actually does the work and is known as the equipment under control. This consists of valves, pumps, sensors, actuators, compressors, etc. |
|
Level 1 |
These are the control devices such as programmable logic controllers that monitor and control Level 0 equipment and safety instrumented systems. |
|
Level 2 |
Control logic for analyzing and acting on Level 1 data. Systems include human-machine interface (HMI); supervisory and data acquisition (SCADA) software. |
|
Level 3 |
This level includes systems that support plant-wide control and monitoring functions. Level 3 systems also aggregate lower level data that needs to be pushed up to higher level business systems. |
|
Level 4 |
Business logistics systems can include database servers, application servers, and file servers. |
|
Level 5 |
Broader set of enterprise IT systems, including connections to the public internet. |
Purdue Model Zones
The levels are typically split into three logical zones, with Levels 4 and Level 5 comprising the enterprise zone, which is separated from the manufacturing zone (comprising Levels 0 through Level 3) by a demilitarized zone (DMZ). This simple model provides a straightforward way to consider which systems need to communicate with each other. It was not originally created as a cybersecurity architecture, but as the business needs for more data sharing between enterprise zone systems and manufacturing zone systems has grown over the years, it has been embraced by security practitioners to help build safer networks.
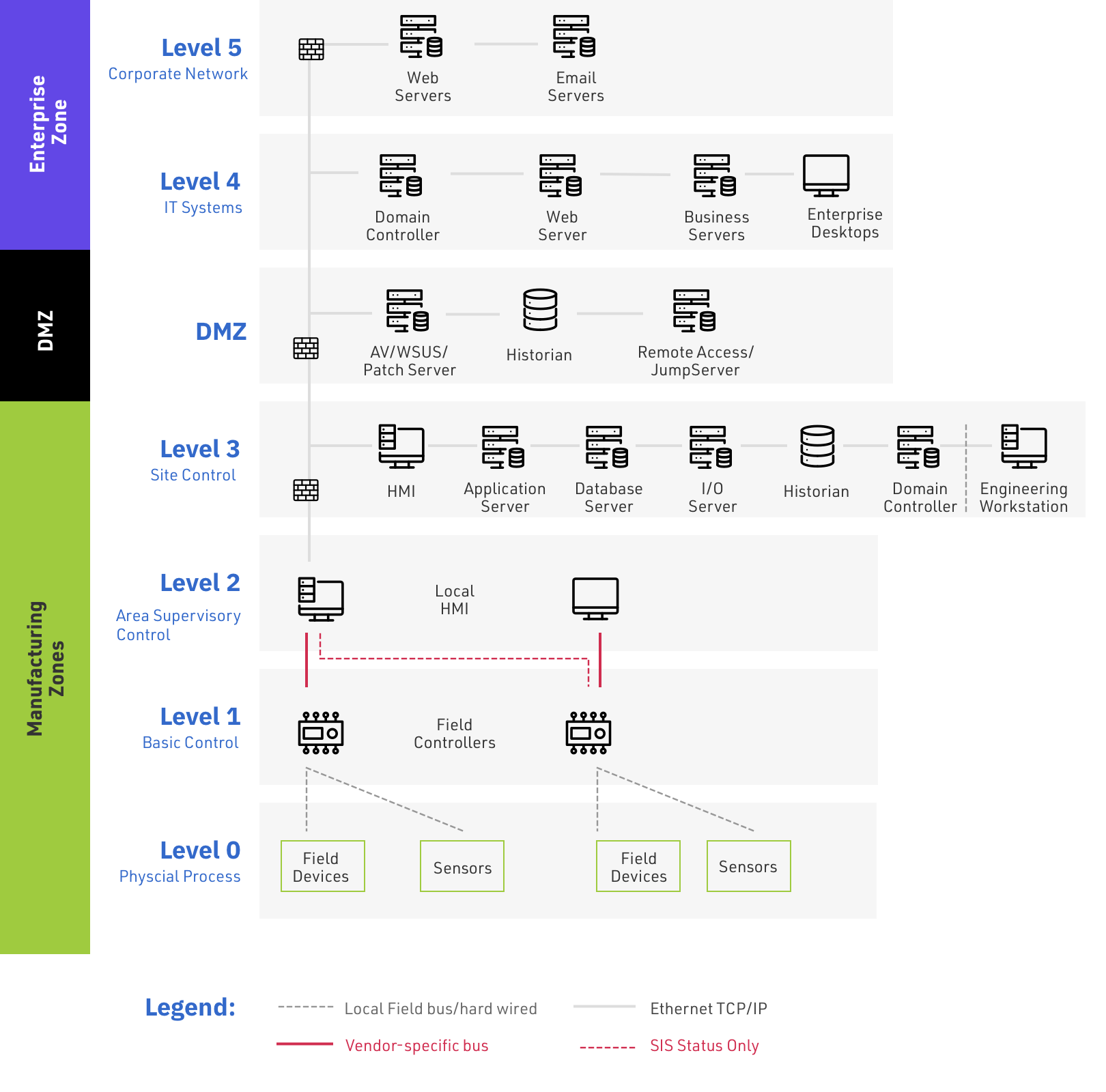
Figure 2: Six Purdue Enterprise Reference Architecture Zones for OT
Concerns with the Purdue Enterprise Reference Architecture
It has been clear for some time that the adoption of several new technologies has punched some literal, and figurative, holes into the Purdue model for ICS cyber security. A chief goal of the model is to throttle or prevent data traffic between levels. Typically, data from each layer must pass through a firewall/DMZ not just between enterprise and manufacturing zones but also before it reaches the next layer up or down. A single point of ingress/egress between layers is not a bug but rather a feature in systems with such high safety, reliability, and regulatory requirements.
IoT architectures can seriously challenge the Purdue model by allowing devices to communicate through an IoT gateway or even directly with cloud services. Either way, traditional Purdue levels can be bypassed. At a minimum, the use of cloud services adds a level to the Purdue model above the traditional enterprise zone. For IoT users, data clearly no longer lives entirely within the enterprise, and the Purdue model can be considered outdated in these environments.
Another emerging technology that can stress the Purdue model is the use of edge computing devices to enable computing and storage operations at the edge of traditional networks. See, for example, the Amazon Web Services Snow Family of edge devices.

Is the Purdue Model Relevant in a World of Industrial Internet of Things (IIoT) and Cloud Services?
Read the ArticleModifying the Purdue Model
In more traditional OT environments, there are efforts to modify the Purdue model to support modern IoT devices and cloud services. The European Union Agency for Cybersecurity (ENISA), for example, has proposed a revised version of the Purdue model that introduces a Level 3-based Industrial IoT (IIoT) platform, which communicates directly with Level 1 IIoT devices. (See Good Practices for Security of the Internet of Things in the context of Smart Manufacturing, November 2018.) Another example of modifying the Purdue model is shown in Figure 3, where the IIoT Zone analyzes and manages all data from the manufacturing and control processes of Level 1 devices and also manages communication of manufacturing data into the enterprise zone or to cloud/internet services.
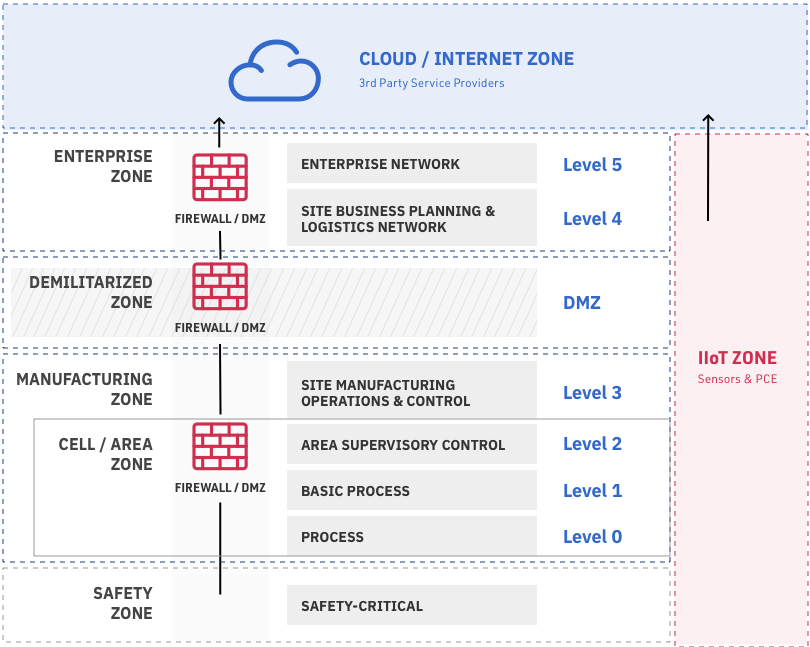
Figure 3: Modifying the Purdue Reference Model with IIoT and Cloud
Non-Industrial Users of the Purdue Model
Not all IoT users feel the need to rigidly adhere to the Purdue model. This is because many of these users typically have far fewer safety, reliability, and regulatory concerns than traditional critical infrastructure providers. While those risks may well be lower, recent history has shown that no one is immune to cybersecurity attacks, and systems should always be secured with cyber risks in mind.
What is the Difference Between IT and OT Security? – Comparing Risk Assessment and Goals
IT and OT cybersecurity differ in fundamental ways, not only because IT and OT systems often require different security controls, but also because IT and OT security practitioners have different goals for “securing” their assets and different definitions of what “secure” means. This is hardly surprising given that IT is chiefly concerned with digital assets and OT is chiefly concerned with physical assets.
Comparing the IT CIA Model with the OT CAIC Model of Priorities
The standard for IT cybersecurity is the well-known confidentiality, integrity, and availability (CIA) triad. Enterprise data is considered proprietary intellectual property that is often the crown jewels of an organization’s business advantage. Keeping digital assets safely under lock and key has therefore been the primary objective of IT cybersecurity strategies. This is followed by the need to ensure the integrity of digital assets. Organizations must not only keep their data out of competitors’ hands, but they must also ensure that data is not corrupted in any way, intentionally or otherwise. Finally, that data needs to be available internally to appropriate employees and partners, and potentially customers.
“Maintaining control of all physical assets to ensure their safe operation at all times is the primary objective of OT cybersecurity and overrides all other concerns.”
The standard for OT cybersecurity, however, requires a broader and a re-ordered set of priorities, namely control, availability, integrity, and confidentiality, or CAIC. Maintaining control of all physical assets to ensure their safe operation at all times is the primary objective of OT cybersecurity and overrides all other concerns. If a facility cannot be run safely, then it will not be run at all. The next most important goal for OT cybersecurity is availability. OT is present in all critical infrastructure facilities, and critical infrastructure typically needs to be available 24/7/365. Integrity is also important, particularly to the degree it ensures safety and availability. Confidentiality of OT data is far less of a concern than it is for IT data.
In addition to having different priorities and goals as they relate to cybersecurity, the technology used in physical systems is often very different from the technology used in information systems. These differences can significantly affect not only the cybersecurity posture of the systems but also the means available to secure them. OT systems often include legacy equipment that is built to have 30-year operational life cycles. This equipment may well have been designed for an era when the entirety of OT was safely air-gapped from the rest of the world.
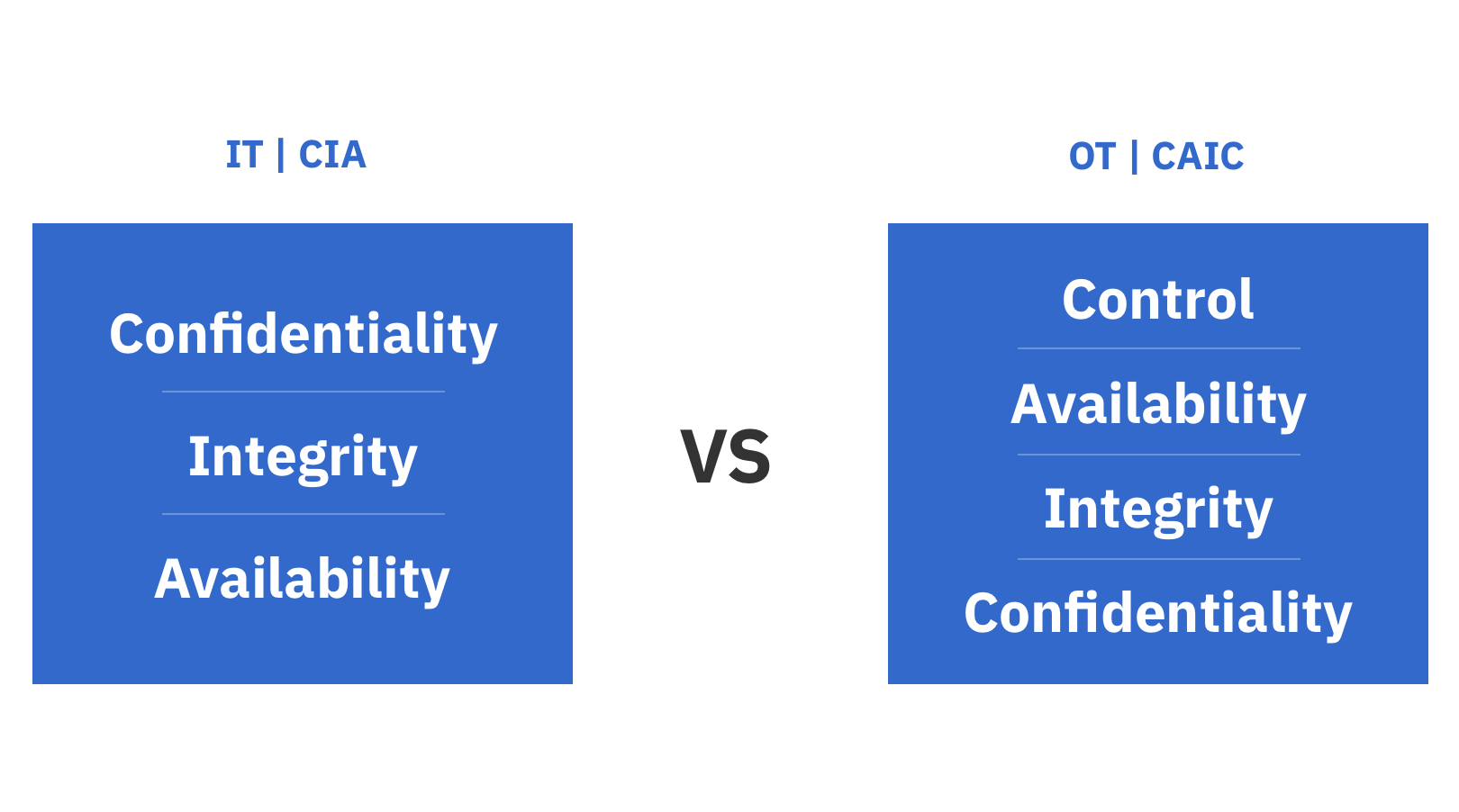 Figure 4: Comparing the IT CIA Model to the OT CAIC Model of Priorities
Figure 4: Comparing the IT CIA Model to the OT CAIC Model of Priorities
The Mythical OT Air Gap
As IT and OT have increasingly been mingled, and as a true air gap has disappeared in all but the most locked down of facilities, OT cybersecurity has had to mature quickly. Interestingly, an air gap is also an extreme example of an old IT cybersecurity practice: setting up a firewall on the network perimeter in order to create a hard shell of protection. However, even if we assume the perimeter protections are bulletproof, this strategy has flaws. For example, many attacks can circumvent a firewall by entering the network through a disk or flash drive already connected to the LAN. And a strategy that focuses only on the perimeter leaves no way to detect or block malicious traffic that is inside the network. The strategy lacks redundancy and depth. Even in the perfect world of an air-gapped perimeter, this can leave systems vulnerable, which will discuss in more detail later in this report.
OT Specific Cybersecurity Controls
Complicating available strategies is the fact that many traditional IT cybersecurity tools cannot be used in OT environments. For example, even the simple act of scanning OT devices for vulnerabilities can trigger significant process disruptions. Similarly, security patch updates in production environments can be problematic because backup systems for patch testing are often unavailable. This is particularly concerning because equipment with known vulnerabilities can be operational for decades. Nevertheless, given the concerns about system disruption, there is an understandable hesitancy among operational teams to allow changes to their OT environments.
And as we have seen, along with these traditional OT cybersecurity challenges, operational teams must now also manage the additional risk of integrating new technologies such as Industrial IoT devices, cloud services, mobile industrial devices, and next-generation wireless networking.
Thinking Like an OT Hacker
A helpful exercise for thinking about both IT and OT cybersecurity is to create a map of the steps an attacker would or could take to compromise an OT system. Both Lockheed Martin and MITRE have created such frameworks. Lockheed Martin calls its framework the Cyber Kill Chain, and MITRE calls its framework ATT&CK. The Lockheed Martin framework is a bit simpler, and we will introduce it here. We will take a more detailed look at the MITRE framework in a later section.
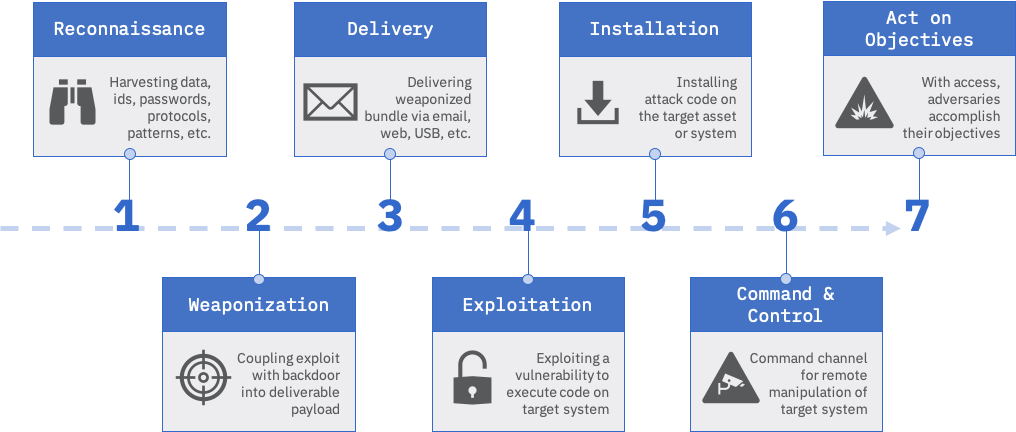
Figure 5: The Lockheed Martin Cyber Kill Chain Framework
Keep in mind that not every attack requires every step in the Cyber Kill Chain, and there may well be some iteration in steps as an attack plays out over time. The general phases of an attack as described in the Lockheed Martin framework are:
- Reconnaissance: Research, identification, and selection of targets and attempts to identify vulnerabilities in the target network
- Weaponization: Creation of remote access malware designed to exploit system based on identified vulnerabilities
- Delivery: Transmission of weapon to target, through email attachment, USB, etc.
- Exploitation: Malware weapon’s code triggered so as to exploit identified vulnerability
- Installation: Malware installs a remote access Trojan or backdoor that is usable by intruder
- Command and Control: Malware typically needs to set up a command-and-control channel through which it can communicate with intruders
- Actions on Objective: Intruder is now in position to take action, such as exfiltrate, destroy, or corrupt data
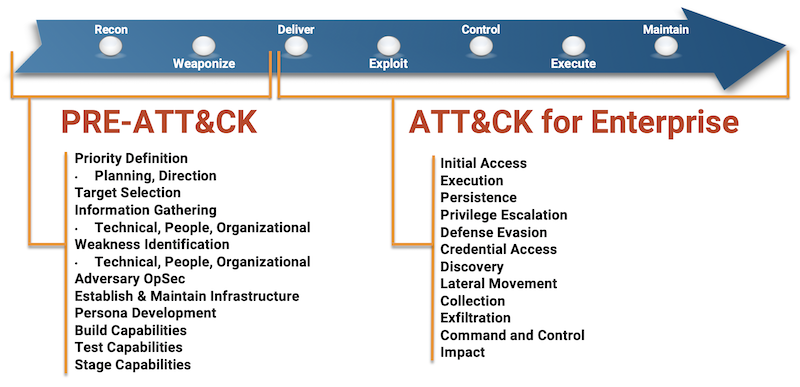 Figure 6: The MITRE ATT&CK Framework
Figure 6: The MITRE ATT&CK Framework
Image Source
Taking Responsibility for OT Cybersecurity
The inherent difficulties in OT cybersecurity, which are compounded by the continuing infiltration of IT into OT systems, have significantly complicated how organizations are meeting the challenge of securing OT. A recent McKinsey report noted:
“Many heavy industrials we surveyed could not identify a party responsible for OT cybersecurity. The chief information-security officer (CISO) may set policy and develop security standards but often has no responsibility for implementing OT cybersecurity in the operations, or for auditing adherence to it. At the same time, many operational units have no clear cybersecurity counterpart responsible for deploying, operating, and maintaining OT cybersecurity controls at the plant level. Therefore, they often neglect OT cybersecurity.”
McKinsey argues strongly for the creation of a Chief Security Officer who is accountable for both IT and OT cybersecurity. This person would consider IT and OT cybersecurity investments as part of broader risk management strategy decisions. According to Gartner, one trend that is already underway is to roll up OT cybersecurity under IT cybersecurity teams. By 2021, Gartner predicts that 70% of OT cybersecurity will be managed directly by CIO, CISO, or CSO departments, up from 35% in 2019.
Who are the Main OT Cybersecurity Threat Actors?
Threats to OT systems can come from a host of threat actors. These actors are typically classified by their motivations or their connection to the organizations they attack. For example, a hacktivist might be motivated by the belief that a manufacturer has unacceptable environmental practices, while an employee might be motivated by a desire for revenge stemming from perceived mistreatment by his employer. Terrorists or nation-states might be motivated by a desire to create chaos or to otherwise achieve a political objective. “Script kiddies” are typically just looking for notoriety and easy pickings.
The Problem with a Determined OT Attacker
Historically, OT systems have been beyond the reach (both literally and figuratively) of all but the most persistent attackers. We have seen, however, that with enough time and effort, even the most well-protected sites can be vulnerable to attack. We have seen that for most organizations the ability to maintain a true air gap for vulnerable equipment is increasingly difficult. But it is also important to recognize that even when air gaps are achieved, they are no guarantee of security against a determined attacker—as demonstrated by documented attacks. A hard, protective shell around assets is clearly a best practice, whether through physical isolation or with firewalls and DMZs, but as we will see later in this report when we discuss defense in depth, organizations cannot build a hard protective shell but leave a soft, chewy core that has no additional protections.
In addition to intentional threats from hostile governments, terrorist groups, disgruntled employees, and malicious intruders, organizations also face unintentional threats, such as those caused by system complexity or accidents, and natural threats, such as floods and earthquakes.
A History of OT / ICS Cyber Incidents
In late 2018, the Office of Scientific and Technical Information within the U. S. Department of Energy (DOE) released a report titled History of Industrial Control System Cyber Incidents. The report provided an overview of publicly confirmed attacks on ICS systems up until December 2018. Attacks began to proliferate around 2010 with the Stuxnet attack, which the report describes as the world’s first publicly known digital weapon.
But the report also provides a tongue-in-cheek example of the world’s first cyberattack with a “hack” in 1903 of the then-new Marconi Wireless system. The incident sounds surprisingly modern in many ways. Guglielmo Marconi was publicly demonstrating his new long-distance wireless communication system by transmitting more than 300 miles from Poldhu in Cornwall to London. Marconi described his system of sending Morse code as secure, but before the official demonstration started, someone else began to send Morse code messages to the London location that mocked and insulted Marconi. A few days later, it was discovered that the “hacker” had been a music hall magician who wanted to prove the system was not secure. The more things change, the more they stay the same.
Documented OT Cyberattacks
“From the cyber-events the world has experienced thus far, we have discovered the technical capabilities of threat actors have evolved significantly, and that their willingness to cause physical damage is startling. . . . For critical infrastructure, developing the ability to detect and recover from a cyber-attack is the most important lesson to be learned, because protecting all systems from any attacker is not possible.”
The modern era of attacks on OT really starts with Stuxnet in 2010. There may well have been earlier successful attacks either of similar sophistication or that caused significant damage to physical infrastructure, but they have not been made public or otherwise discovered.
Other notable attacks include:
- Night Dragon (2009/2010)
- Duqu/Flame/Gauss (2011)
- Gas Pipeline Cyber-Intrusion Campaign (2011)
- Shamoon – Saudi Aramco and RasGas (2012)
- Target Stores (2013)
- New York Dam (2013)
- Havex (2013)
- German Steel Mill (2014)
- BlackEnergy (2014)
- Dragonfly/ Energetic Bear (2014)
- Ukraine Power Grid (2015)
- Kemuri Water Company (2016)
- Return of Shamoon (2016)
- Second Attack on the Ukrainian Power Grid (2016)
- CRASHOVERRIDE (2016)
- APT33 (2017)
- NotPetya (2017)
- Dragonfly/Energetic Bear Returns (2017)
- TRITON/Trisis/HatMan (2017)
- Cryptocurrency Mining Malware on European Water Utility (2018)
- Malware Impacting Windows-based OT Assets (2019)
We do not have the room here to explore the details of these attacks, but the reader is encouraged to read the previously-mentioned DOE report. We will quote from the authors conclusions:
“From the cyber-events the world has experienced thus far, we have discovered the technical capabilities of threat actors have evolved significantly, and that their willingness to cause physical damage is startling...For critical infrastructure, developing the ability to detect and recover from a cyber-attack is the most important lesson to be learned, because protecting all systems from any attacker is not possible.”
Classifying OT Cyberattacks
Given the various motivations and skill levels of attackers, it is not surprising that the sophistication and severity of attacks on OT/ICS systems can vary significantly. Damage to OT systems can also be a result of collateral damage to other assets under attack. When investigating attacks, either from the historical record or from within your own systems, it is helpful to build a timeline that maps attack events against the Lockheed Martin Cyber Kill Chain framework we discussed earlier. Often, you will find that the early stages of attacks were performed well ahead of the eventual detection of an attack.
Short of embarking on that level of attack analysis, categorizing attacks based on a few high-level metrics is also helpful. The research team at FireEye has developed a useful categorization scheme, which it terms the OT Cyber Security Incident Ontology (OT-CSIO).
The methodology classifies attacks based on a few metrics:
- Target: ICS is targeted, or ICS coincidentally impacted
- Sophistication: Low/Medium/High
- Impact: Data compromised/data stolen/operations degraded/operations disrupted/systems destroyed
- Impacted Equipment: Purdue Layer(s) of equipment that was affected
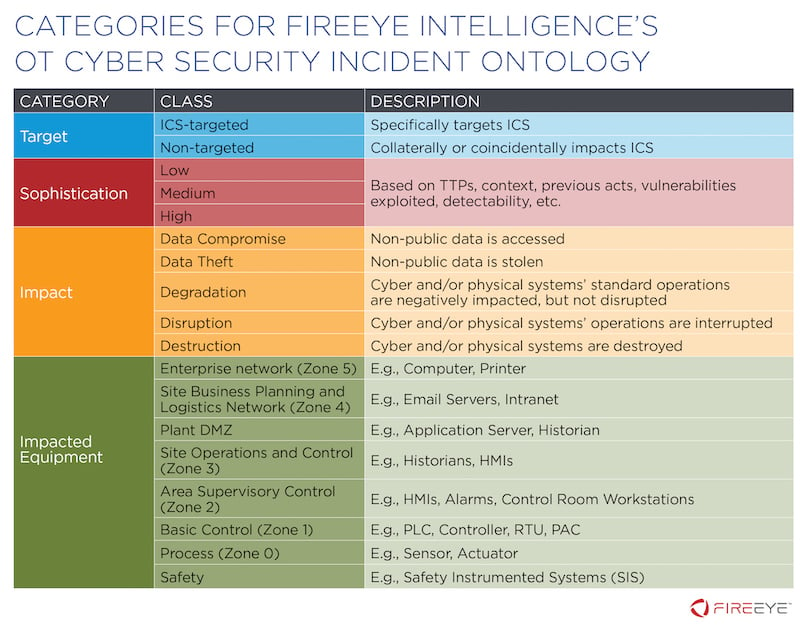
Figure 7: The FireEye Operational Technology Cyber Security Incident Ontology
Image Source
Attacks on IoT systems can be analyzed in a similar manner. Keep in mind that attacks on IoT devices bring the added concern that they might be compromised as part of distributed denial-of-service (DDoS) attacks on other infrastructure. In other words, while they have been directly targeted, it is a means to another end.
OT Cyberattacks Follow the Opportunity
Going forward, it is safe to assume that cybersecurity concerns will grow at least as fast as the market grows—and these markets are growing extremely fast. According to market research firm Statistica, the global IoT market will reach $1.6 trillion by 2025. The IIoT market is estimated to reach $110 billion in 2020, according to Morgan Stanley. This is a larger market than the traditional OT market, which is expected to reach $40 billion by 2022, according to market research firm Markets and Markets. By comparison, the global IT market is expected to reach $4.3 trillion in 2020, according to IDC.
What is Defense in Depth for OT Cybersecurity?
Defense in depth is the strategy of protecting assets through the use of multiple cybersecurity measures. With respect to OT cybersecurity, defense in depth will typically encompass a range of tools, technologies, and techniques that are applied at all hierarchical and physical infrastructure levels.
As we have seen, strong perimeter protections are necessary but not in themselves sufficient for effective OT cybersecurity. A layered approach, or defense in depth, is considered best practice for both IT and OT cybersecurity. There are numerous defense-in-depth frameworks available for OT cybersecurity, and in the United States, the National Institute of Standards and Technology (NIST) has taken a lead in defining security requirements for critical infrastructure providers.
OT Cybersecurity Objectives
Before we discuss the general cybersecurity controls recommended for OT, it helps to have an understanding of the major cybersecurity objectives. NIST recommends the following for ICS implementations (NIST SP-800-82):
- Restricting logical access to the ICS network and network activity
- Restricting physical access to the ICS network and devices
- Protecting individual ICS components from exploitation
- Restricting unauthorized modification of data
- Detecting cybersecurity events and incidents
- Maintaining functionality during adverse conditions
- Restoring the system after an incident
This list should make it clear that to be effective, OT cybersecurity needs to be a component of a broader risk management program that includes traditional physical security and disaster recovery. At the same time, it is important to tailor actual controls specifically to OT systems. NIST recommends a life cycle approach to OT cybersecurity that inserts cybersecurity considerations into planning decisions from design to decommissioning.
Hierarchy of Protection Strategies for OT Cybersecurity
Defense in depth, therefore, should include design choices when considering new OT systems. Cybersecurity should be approached like any other risk management process. Take, for example, the hierarchy of controls for reducing the risk of physical injury in a plant. The ideal solution eliminates the risk by removing the hazard or replacing it. In this example, that could involve completely changing a manufacturing process so that a dangerous piece of machinery is no longer needed. Short of that, the hazardous piece of equipment could be replaced with safer equipment. If neither of these options are available, then adding an engineering control to isolate people from the hazard is the next best option. If that is not possible, then an administrative control that changes the way people work around the machine would be required. And finally, if that were not possible, personal protective equipment (PPE) could be issued for employees to protect them against a known hazard. Applying bolt-on cybersecurity products to mediate a known vulnerability in OT systems is the equivalent of issuing PPE to your employees. It is a last resort.
Eliminate the Need for OT Cybersecurity Controls Where Possible
There are a host of reasons for why organizations find themselves with no option but to bolt on cybersecurity controls. And this is why it is important to begin addressing concerns much further upstream in the design process so that the need for security controls becomes less common. What are some examples? At an architectural level, NIST recommends (NIST SP 800-82):
- Ensuring that critical components are redundant and are on redundant networks
- Designing critical systems for graceful degradation to prevent catastrophic cascading events
- Implementing a network topology for the ICS that has multiple layers, with the most critical communications occurring in the most secure and reliable layer
- Providing logical separation between the corporate and ICS networks
- Employing a DMZ network architecture
- Employing reliable and secure network protocols and services where feasible
At the engineering and administrative levels, NIST recommends:
- Restricting physical access to the ICS network and devices
- Using separate authentication mechanisms and credentials for users of the ICS network and the corporate network
- Disabling unused ports and services on ICS devices after testing to assure this will not impact ICS operation
- Restricting ICS user privileges to only those that are required to perform each person’s job
- Applying security techniques such as encryption and/or cryptographic hashes to ICS data storage and communications where determined appropriate
- Expeditiously deploying security patches after testing all patches under field conditions on a test system
- Tracking and monitoring audit trails on critical areas of the ICS
And finally, as a sort of OT cybersecurity PPE, NIST recommends a host of security controls such as intrusion detection software, antivirus software, and file integrity checking software. The universe of security controls that can be applied to OT is large and diverse. NIST has recommendations for the use of dozens of classes of controls (NIST SP 800-53). These include:
- Access Control
- Identification and Authentication
- Incident Response
- Media Protection
- Risk Assessment
- Security Assessment and Authorization
- System and Communications Protection
- System and Information Integrity
Gartner OT Cybersecurity Control Classifications
Different organizations classify and prioritize cybersecurity controls in different ways. For example, Gartner tracks the following high-level OT security categories:
- OT Network Monitoring and Visibility
- OT Network Segmentation
- OT Secure Remote Access
- OT Endpoint Security
- OT Security Services
The depth of controls, of course, is a result of the breadth of potential attacks, which include man-in-the-middle attacks, privilege escalations, spoofing attacks, vulnerabilities in protocols, and attacks on endpoints, databases, and gateway devices. There is clear overlap in the types of attacks targeting IT and OT systems, and several important cybersecurity controls for IT can also be deployed in protecting OT.

Industrial Cybersecurity: Efficiently Secure Critical Infrastructure Systems
Read the ArticleRecommended OT Cyber Protections
Gartner recommends leveraging some IT cybersecurity controls at both the network and endpoint layers, in addition to deploying cybersecurity controls developed specifically for OT requirements. Traditional cybersecurity controls recommended by Gartner for use to protect OT include VPN/firewalls, intrusion detection systems (IDS)/intrusion prevention systems (IPS), network access control (NAC), and deception/obfuscation tools.
OT cybersecurity products include asset discovery, vulnerability management, unidirectional gateways, and application and device control. It should also be noted that some traditional IT security products can be deployed in OT systems if used in limited ways. For example, devices such as the IPS might only ever be operated in passive IDS mode.
The need for a matrix of general-purpose IT security controls mixed with OT-specific controls is a major driver in the consolidation of IT security and OT security teams and the associated trend of having the CISO control the budget and strategy for both mandates.
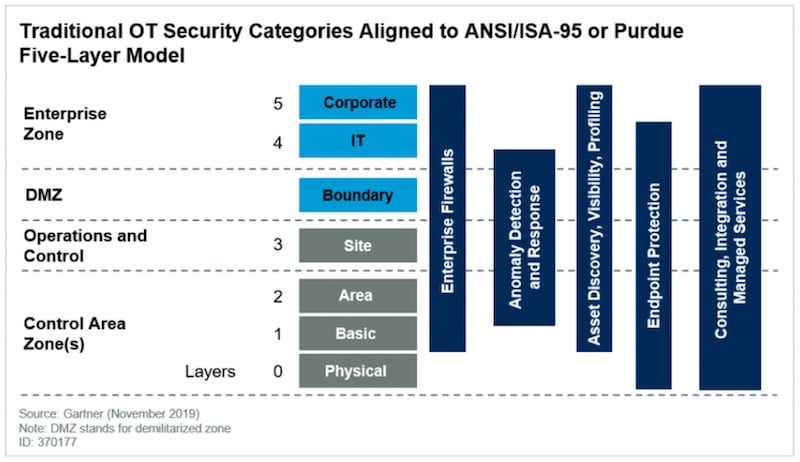
Figure 8: Defense in Depth for OT Cybersecurity
What are the Leading OT Cybersecurity Regulations and Frameworks?
In the United States, where there are no industry-wide federal regulations for OT cybersecurity, the NIST recommendations for OT cybersecurity are broadly acknowledged as important and useful because they were created to protect the most demanding critical infrastructure environments. They are not, however, the only important guidelines, and many other jurisdictions, including UK, EU, China, Japan, and Australia, have their own regulations and/or recommended frameworks.
Post-911 Response
Efforts to secure critical infrastructure in the U.S. took on a new urgency after September 11, 2001. Homeland Security Presidential Directive 7 was issued in 2003 and led to the development of the National Infrastructure Protection Plan, which was first released in 2006. Efforts to improve the security of critical infrastructure have been supported across several administrations, and in February 2013, Executive Order (EO) 13636 was issued on Improving Critical Infrastructure Cybersecurity. The EO was issued with Presidential Policy Directive-21 (PPD-21): Critical Infrastructure Security and Resilience. The NIST Cybersecurity Framework that was released in February 2014 was a response to EO 13636.
U.S. Critical Infrastructure Sectors
The Cybersecurity and Infrastructure Security Agency Act of 2018 created a new federal agency to lead U.S. Government efforts to protect critical infrastructure from cybersecurity and other threats. The Cybersecurity and Infrastructure Security Agency (CISA) is particularly concerned with protecting the 16 sectors of the economy that the U.S. Government designates as critical infrastructure: Chemicals Sector, Commercial Facilities Sector, Communications Sector, Critical Manufacturing Sector, Dams Sector, Defense Industrial Base Sector, Emergency Services Sector, Food and Agriculture Sector, Government Facilities Sector, Healthcare and Public Health Sector, Information Technology Sector, Nuclear Reactors Sector, Materials and Waste Sector, Transportation Systems Sector, Waste and Wastewater Systems Sector. CISA is still a young agency, but it is already offering industry guidance on topics such as Cybersecurity Best Practices for Industrial Control Systems.
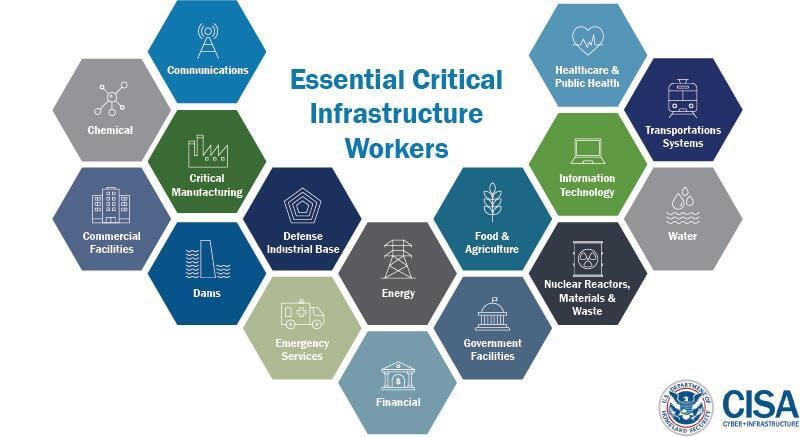
Figure 9: Cybersecurity & Infrastructure Security Agency (CISA) Critical Infrastructure Sectors
Image Source
No Comprehensive Federal Regulation in U. S.
There is surprising little federal regulation in the U.S. for cybersecurity. No comprehensive legislation exists, and industry-specific laws are, for the most part, focused on data privacy. Privacy-focused laws include the Health Insurance Portability and Accountability Act (HIPAA), which protects sensitive patient information, and the Gramm-Leach-Bliley Act, which applies to financial services companies.
Vertical-Specific OT Cybersecurity Frameworks
Several critical infrastructure sectors have frameworks that are tailored to their requirements. For example, the not-for-profit corporation North American Electric Reliability Corporation enforces the Critical Infrastructure Protection (CIP) standards (NERC CIP) for North American electricity infrastructure. In 2009, the U.S. Nuclear Regulatory Commission (NRC) revised its security requirements for nuclear power plants. In response, the industry developed the Cyber Security Plan for Nuclear Power Reactors (NEI 08-09), which the NRC approved in 2010. And the American Water Works Association (AWWA) has created a Cybersecurity Guidance and Assessment Tool.
NIST has also begun creating profiles that provide industry-specific implementation details for its Cybersecurity Framework and has currently released profiles for process-based and discrete-based manufacturing.
International Frameworks
Outside the United States, the details differ but the goals and strategies are similar. The European Union enacted its NIS Directive on the security of network and information systems (Directive (EU) 2016/1148) in 2016, which included critical infrastructure components. The European Union Agency for Cybersecurity (ENISA) published a December 2017 report, Mapping of OES Security Requirements to Specific Sectors, that provides sector-by-sector guidance. In May 2020, the EU adopted a new cybersecurity strategy, which among other things, calls for a review of the NIS Directive and a proposal for additional measures on the protection of critical infrastructure.
The Australian Government has also taken a comprehensive approach to critical infrastructure protection. In 2018, the Security of Critical Infrastructure Act 2018 became law. The Australian Government’s Critical Infrastructure Centre (CIC) has created a CIC Compliance Strategy document that outlines both the obligations of critical infrastructure owners/operators as well as the key elements of the CIC’s recommendations for compliance with Australian law.
Cross-Industry Cybersecurity Frameworks
The International Society of Automation (ISA) has created a broadly applicable Industrial Automation and Control Systems (IACS) security framework. ISA-99, the standards development committee, includes and collaborates with industrial cybersecurity experts internationally, and their original work (ANSI/ISA-99) and ongoing development are being used by the International Electrotechnical Commission (IEC) to produce the ISA/IEC-62443 standard series.
The Industrial Internet Consortium has developed The Industrial Internet Security Framework (IISF), which is a cross-industry-focused cybersecurity framework for IIoT. The understanding that the widespread adoption of IoT technology is considerably increasing risk is driving a global effort for cybersecurity strategies that address these concerns.
The Cloud Security Alliance (CSA) has also developed a cross-industry IoT Security Controls Framework, and the IoT Security Foundation has created its own IoT Security Compliance Framework.
NIST has created a testbed for IoT and cyber-physical systems and has published numerous guidance documents on topics including cyber-physical systems/IoT for smart cities and cybersecurity for smart grid systems and smart manufacturing systems.
The Global System for Mobile Communications Association (GSMA) is a global association of mobile network operators that has also created IoT security guidelines for its members and partners. These include: IoT Security Guidelines for Network Operators, IoT Security Guidelines for Endpoint Ecosystem, and IoT Security Guidelines for Service Ecosystem.
Critical Cybersecurity Controls
As a starting point, readers should consider examining the Center for Internet Security’s Critical Security Controls. The CIS Controls were first developed in 2008 to assist organizations in prioritizing their security efforts. The 20 Controls are designed to provide a starting point for security investments and have been mapped to several of the OT and IoT frameworks discussed in this report. CIS has also developed companion guides for implementing the controls in both ICS and IoT environments. The CIS Controls ICS Companion Guide was published in 2018, and the CIS Controls Internet of Things Companion Guide was published in 2019.
What are OT Cybersecurity Best Practices Recommendations?
The good news for OT cybersecurity practitioners is that there is a significant and sustained global effort to figure out how to better protect deployed OT. These endeavors are being performed by both public and private entities and informed by successful defenses against real-world attacks. A consensus is forming around best practices and critical controls that provide OT cybersecurity teams with a strong foundation for hardening systems.
In the United States, 85 – 90% of the federal designated critical infrastructure is privately owned and operated. It is up to these private actors to keep their infrastructure operational. As we have seen, OT cybersecurity is an important consideration when assessing risk in operations. Historically, critical infrastructure providers have been leaders in implementing holistic risk management frameworks, such as ISO 31000:2018, and OT cybersecurity should be a mandatory component in all OT risk calculations.
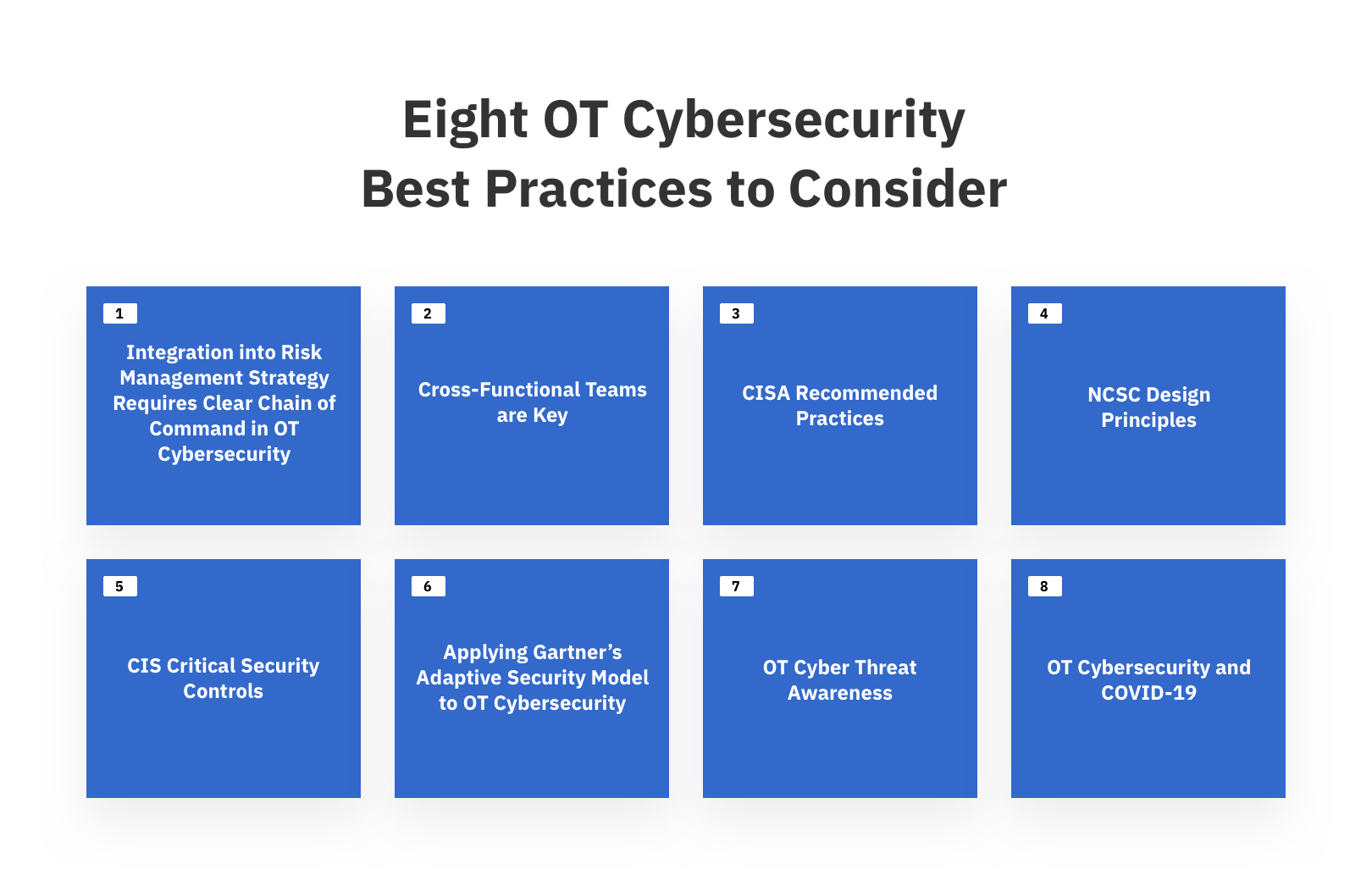 Figure 10: Cybersecurity OT - Eight Best Practices to Consider
Figure 10: Cybersecurity OT - Eight Best Practices to Consider
1. Integration into Risk Management Strategy Requires Clear Chain of Command in OT Cybersecurity
Implementation of an OT security strategy that is fully-funded and that works with, not against, broader safety and reliability efforts requires a clear chain of command with defined authority and responsibility. A Chief Security Officer (CSO) should have responsibility for both IT security and OT security and should report directly to the Chief Operations Officer (COO); this will help to protect security budgets and operational authority. The goal is to have OT security competently represented in the C-suite of every organization and to create recognition that OT security is a topic that increasingly warrants board-level discussion.
“70% of OT organizations report that they intend to make the CISO responsible for OT cybersecurity within the next year—currently at just 9%.”
In general, the industry seems to be moving in this direction. 70% of OT organizations report that they intend to make the CISO responsible for OT cybersecurity within the next year—currently at just 9% according to the SANS 2019 State of OT/ICS Cybersecurity Survey.
2. Cross-Functional Teams are Key
NIST recommends building a cross-functional OT cybersecurity team that, at a minimum, consists of a control engineer, a control system operator, a network and system security expert, a member of the management staff, a member of the physical security department, and a member from the organization’s IT staff. Understanding potential impacts on systems due to OT cybersecurity related activity is absolutely critical and will benefit from the input of operational staff.
3. CISA Recommended Practices
Earlier, we introduced the CISA Recommended Cybersecurity Practices and CIS Critical Security Controls. Both are good starting points for organizations seeking to achieve a security baseline. CISA recommends ten high-level best practices:
- Check, prioritize, test, and implement ICS security patches
- Back-up system data and configurations
- Identify, minimize, and secure all network connections to ICS
- Continually monitor and assess the security of ICS, networks, and interconnections
- Disable unnecessary services, ports, and protocols
- Enable available security features and implement robust configuration management practices
- Leverage both application whitelisting and antivirus software
- Provide ICS cybersecurity training for all operators and administrators
- Maintain and test an incident response plan
- Implement a risk-based, defense-in-depth approach to securing ICS hosts and networks
4. NCSC Design Principles
For organizations that are taking a ground-up approach, CISA suggests the UK National Cyber Security Centre’s (NCSC) Design Principles and Operational Technology. The following is an outline of the NCSC design principles:
- Establish the context before designing a system: In other words, determine the elements in the system so that defensive measures will have no blind spots.
- Build “attack trees” or Cyber Kill Chain models of how systems would need to be attacked
- Group systems into zones to better understand the impact of theoretical compromise. The Purdue model is suggested.
- Map and understand vulnerabilities at zone boundaries
- Agree on network design and documentation
- Make compromise difficult: Attackers can only target devices and systems they can reach.
- Any data coming from a lower trust zone is potentially dangerous
- Enforce a one-way flow of data
- Reduce the attack surface
- Implement crucial security controls in stages to gain confidence. For example, initially running an IPS in detection mode only.
- Make disruption difficult: Design a system that is resilient against denial-of-service attacks and usage spikes.
- Make compromise detection easier: Design systems so that suspicious activity is easy to spot
- Log collection
- Malware detection
- Mask detection techniques to hide them from attackers
- Keep authorized communications simple to make unauthorized communications easier to detect
- Understand all required use cases for access to control systems and decrease attack surface
- Reduce impact of compromise: Make lateral movement in a network as difficult as possible.
- Remove unnecessary functionality from systems at boundaries
- Design, architect, and configure administrative systems, such as Active Directory, to reduce attack surface
- Enforce separation of duties
- Treat all design documentation as confidential
- Plan for a smooth recovery
5. CIS Critical Security Controls
The generic set of CIS 20 Controls provide a good baseline for cybersecurity and can be tailored to ICS and IoT environments. The controls are grouped into Basic, Foundational, and Organizational categories and are as follows:
- CIS Control #1: Inventory and Control of Hardware Assets
- CIS Control #2: Inventory and Control of Software Assets
- CIS Control #3: Continuous Vulnerability Assessment and Remediation
- CIS Control #4: Controlled Use of Administrative Privileges
- CIS Control #5: Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers
- CIS Control #6: Maintenance, Monitoring, and Analysis of Audit Logs
- CIS Control #7: Email and Web Browser Protections
- CIS Control #8: Malware Defenses
- CIS Control #9: Limitation and Control of Network Ports, Protocols, and Services
- CIS Control #10: Data Recovery Capability
- CIS Control #11: Secure Configuration for Network Devices
- CIS Control #12: Boundary Defense
- CIS Control #13: Data Protection
- CIS Control #14: Controlled Access
- CIS Control #15: Wireless Access Control
- CIS Control #16: Account Monitoring and Control
- CIS Control #17: Security Skills Assessment & Training
- CIS Control #18: Application Software Security
- CIS Control #19: Incident Response and Management
- CIS Control #20: Penetration Tests and Red Team Exercises
Readers are referred to the Implementation Guides for ICS or IoT for information on applying CIS recommendations to ICS or IoT environments.
6. Applying Gartner’s Adaptive Security Model to OT Cybersecurity
It is often said that cybersecurity is a process. It should also be continuous and adaptive, and Gartner has created an Adaptive Security Architecture (ASA) that embraces this idea. While traditional IT cybersecurity focused chiefly on threat detection and prevention, the ASA model adds prediction and response to create a continuous cycle. The model’s four stages can be defined as:
Predict – assess risks and anticipate attacks, implement baseline security hygiene.
Prevent – harden and isolate systems where possible.
Respond – investigate incidents, determine root cause, patch vulnerabilities.
Detect – prioritize risks, detect and contain incidents.
This approach is useful and should be considered along with the idea of an attack life cycle, introduced earlier and popularized in the models from MITRE (ATT&CK) and Lockheed Martin (Cyber Kill Chain). By more fully understanding earlier indicators of attack, prediction becomes easier, which better informs strategy and eases the burden of other steps in the cycle.
7. OT Cyber Threat Awareness
Finally, another important best practice for recognizing threats early on is to participate in cyber threat awareness programs, such as the U.S. Department of Homeland Security’s ICS-CERT and the Industrial Control System Information Sharing and Analysis Center ICS-ISAC. Understanding current threats that target ICS/OT systems is particularly helpful in prioritizing efforts.
8. OT Cybersecurity and COVID-19
The COVID-19 pandemic has caused a significant and perhaps long-lasting shift in how and where people work. Work-from-home policies have become mandatory in many locations and the use of remote access and digital communications (Zoom call, anyone?) has increased. Keeping workers healthy is especially important when those workers are essential personnel. CISA has released a guidance document, CISA Insights: Risk Management for Novel Coronavirus (COVID-19), which advises organizations take the following steps:
- Ensure VPNs and other remote access systems are fully patched
- Enhance system monitoring to receive early detection and alerts on abnormal activity
- Implement multi-factor authentication
- Ensure all machines have properly configured firewalls as well as anti-malware and intrusion prevention software installed.
- Test remote access solutions capacity or increase capacity
- Ensure continuity of operations plans or business continuity plans are up to date
- Increase awareness of information technology support mechanisms for employees who work remotely
- Update incident response plans to consider workforce changes in a distributed environment
What are Ten OT Cybersecurity Trends to Watch?
The biggest trend in the OT and IoT markets is growth. This growth is driven by the confluence of emerging and maturing technologies that enable a much broader adoption of visibility and control systems. This adoption is in turn is driving the accelerated integration of OT and IT, which raises a host of cybersecurity questions that will likely take another decade to fully address.
Attacks will Continue to Rise
“The 2020 IBM X-Force Threat Intelligence Index reports that attacks on OT systems jumped 2000% year over year in 2019. According to the report, ‘Threat actors continue to shift their sights to attack vectors including IoT, OT and connected industrial and medical systems.’”
The easiest prediction to make about ICS, OT, and IoT security is that things will surely get worse before they get better. The 2020 IBM X-Force Threat Intelligence Index reports that attacks on OT systems jumped 2000% year over year in 2019. According to the report, “Threat actors continue to shift their sights to attack vectors including IoT, OT and connected industrial and medical systems.” And a lack of alignment between IT security and OT security efforts is currently hindering the ability to fully protect OT systems, according to a Ponemon Institute survey conducted in 2020. That survey of more than 2,000 cybersecurity practitioners reported that “Sixty-three percent of respondents say OT and IT security risk management efforts are not coordinated making it difficult to achieve a strong security posture in the OT environment.”
 Figure 11: Cybersecurity OT - Ten Trends to Watch
Figure 11: Cybersecurity OT - Ten Trends to Watch
1. IoT Market Growth, Growth, Growth
Another easy prediction is the continued growth of the IoT market. A 2019 forecast from International Data Corporation (IDC) estimates that by 2025 there will be 41.6 billion connected IoT devices generating 79.4 zettabytes (ZB) of data. This tremendous growth is both driving and being driven by technology trends at every level of the IoT stack, which includes devices, connectivity, platforms or cloud, and applications. The speed at which IoT advancements are driving changes in more traditional OT environments is quite astonishing.
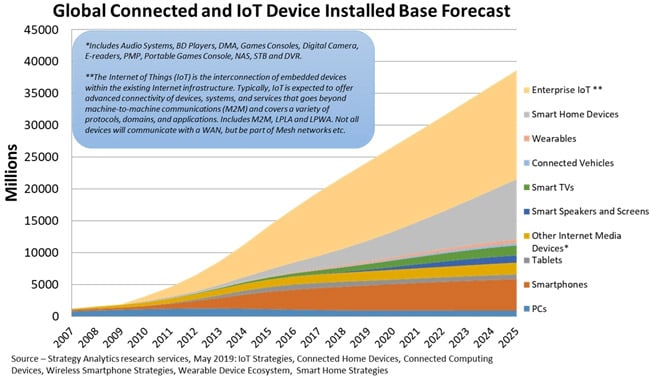
Figure 12: The Growth in Enterprise-Connected IoT
Image Source
A major positive trend in the device market is the continuing improvements, in both price and performance, of sensor technology. The broader adoption of connected sensors will further drive the development of sensor applications. Moreover, improved mobile connectivity made possible with the adoption of 5G will enable new applications, including augmented and virtual reality. And 5G is coming fast. According to a 2020 Business Insider survey, 39% of respondents are already planning to support 5G as part of their IoT projects before 2021.
2. The Impact and Adoption of the Cloud
Cloud is another technology that is proving itself in IoT environments but will increasingly be leveraged by OT systems. We expect advanced applications for managing SCADA systems, for example, to be adopted, driven by efficiency gains, cost reduction, and increased reliability. SCADA as a service will be positioned as providing redundancy and improving uptime. Demonstrating security will of course be key to rapid adoption.
3. OT Cybersecurity Benefits from AI and Big Data
Applications will increasingly take advantage of long-established trends, such as the 100x increase in computing power over the last 15 years, as well as newer trends, such as big data and advances in artificial intelligence (AI) and machine learning (ML). The continued adoption of connected devices and consolidation of sensor data will drive continued investment in AI, ML, simulation, and predictive maintenance.
These advances are also helping to further manufacturing technologies in areas such as industrial robotics and 3D printing. It is not an overstatement to say we have entered the fourth Industrial Revolution, which makes it no surprise then that IoT security spending is growing rapidly. Gartner projects that worldwide IoT security spending will reach $3.1 billion in 2021.
4. OT Cybersecurity and Risk Management Services
One of the fastest-growing segments in the OT space is risk management services. And yet, according to a Bloor Research report, in 2018, 81% of businesses still did not have an OT-specific security incident response plan in place. Many organizations will have to rely on external services to accelerate these efforts. This is becoming more critical as the need for unified incident response drives the ongoing consolidation and cross-fertilization between IT and OT security teams into consolidated security operations centers.
5. Cybersecurity Teams Need to Review All Technology Purchases
The introduction of new technologies requires complete visibility and early buy-in across the organization. Many organizations have established architecture review committees to fully vet new technologies, or modifications to existing technologies, being introduced into OT or IT environments. Risk management practices should include an information risk management component that addresses strategy, compliance, and reporting.
6. The Purdue Model will Continue to Evolve
The continuing convergence of IT and OT will raise more questions about the relevance of the Purdue model. There is not a business technology today that isn’t in use in industrial control systems. And while this has killed the network representation aspects of the traditional Purdue architecture, the model is still relevant with respect to how the components of OT should interoperate to create the desired operational functionality. That need for understanding interoperability was why the model’s hierarchy was developed in the first place. So, the Purdue model will continue to add value with respect to building taxonomy and classification between system elements.
For example, by mapping operational functionality relationships, the model can identify potential attack targets and attack paths. Going forward, it will be more useful to use the model to understand operational functionality interrelationships and to build security around those relationships, as opposed to focusing on traditional Purdue layers. This will be especially true as IIoT devices continue to find their way into OT systems and as control functions move up and out into the cloud.
7. The Zero Trust Model will Increasingly be Embraced in OT Cybersecurity
The concept of a zero-trust architecture assumes that even data traveling inside the network is suspect. Zero trust means that no communications have assumed trust. The assumption is that traffic is suspect until proven otherwise. The difference between whitelisting and blacklisting is another good example of how to reduce trust. The former practice blocks traffic unless it is on an approved list; the latter allows traffic unless it is on a block list. It’s a completely different mindset with respect to trust. Whitelisting is, in fact, another OT security best practice.

Industrial Cybersecurity: Applying Zero Trust and CARTA to Operational Technology (OT)
Learn more about zero trust architecture in OT environments8. Red Team Deployments will Increase
As we discussed earlier, penetration tests and red team exercises are a CIS Control best practice. CIS recommends the use of third-party specialists and recommends that organizations “consider conducting regular non-intrusive security assessments with the assistance of third-parties to identify a greater diversity of vulnerabilities and attack vectors that can be used to breach security of ICS systems.” The use of third-party experts would also be prudent given the concern of operational disruption during investigations. As organizations mature their OT cybersecurity strategies and evolve into more proactive defense, penetration testing, and red team exercises will take a more prominent role in determining security posture.
9. Cyber Insurance
“Some carriers have become skittish regarding potential payouts for physical damage resulting from cyber-attacks, and we suspect stand-alone policies will become more standard as cyber protections are viewed and priced as unique offerings, and as exclusions are explicitly written into more traditional policies with respect to cyber losses.”
The use of insurance policies to hedge cyber risk will grow. The market will continue to evolve however as insurance carriers move away from bundling cyber insurance with more traditional coverages, such as property and general liability. Some carriers have become skittish regarding potential payouts for physical damage resulting from cyber-attacks, and we suspect stand-alone policies will become more standard as cyber protections are viewed and priced as unique offerings, and as exclusions are explicitly written into more traditional policies with respect to cyber losses.
10. Expanding IoT Security Regulations
One important trend that has emerged is governments attempting to get ahead of cybersecurity concerns related to IoT. California became the first state to have an IoT cybersecurity law when SB-327 went into effect on January 1, 2020. The law requires the manufacturer of any device that connects “directly or indirectly” to the internet equip the device out-of-the-box with “reasonable” cybersecurity features designed to prevent unauthorized access, modification, or information disclosure. California tends to be a bellwether state for privacy and security laws, and we expect other states to follow its lead.
NIST is also contributing with guidance on what baseline cybersecurity should be built into IoT devices. In May 2020, the agency published Foundational Cybersecurity Activities for IoT Device Manufacturers, a report that describes “recommended activities related to cybersecurity that manufacturers should consider performing before their IoT devices are sold to customers.”
It is possible that federal legislation related to IoT that passed the Senate in 2020 may become law. The Developing Innovation and Growing the Internet of Things Act, or the DIGIT Act, is designed chiefly to identify and eliminate any federal inhibitors to continued growth in IoT, but it also addresses potential privacy, security, and safety issues associated with the technology. A recent KPMG report, After the Rainfall of IoT Regulations, notes IoT security regulation efforts in China, Japan, Australia, Canada, Brazil, the UK, and the EU, in addition to the United States.
OT Cybersecurity Resources
Need help getting started on your cybersecurity action plan or just want to learn more about OT cybersecurity? Here are some resources that can get you on the right track:
- NIST Internet of Things (IoT)
- NIST Industrial Control Systems (ICS)
- U.S. Foundational Cybersecurity Resources
- International Cybersecurity Resources
- Australian Government Critical Infrastructure Centre (CIC)
- Australian CIC Compliance Strategy
- EU Network and Information Security (NIS) directive
- European Union Agency for Cybersecurity (ENISA) Mapping of OES Security Requirements to Specific Sectors
- German Plattform Industrie 4.0
- UK National Cyber Security Centre (NCSC) OT Security Design Principles
- Cross-Industry Cybersecurity Resources
- ANSI/ISA-95 Enterprise Control System Integration
- Cloud Security Alliance (CSA) IoT Security Controls Framework
- ENISA Good Practices for Security of Internet of Things in the context of Smart Manufacturing
- Industrial Internet Consortium IIoT
- The International Society of Automation Global Cybersecurity Alliance (ISAGCA)
- IoT Security Foundation IoT Security Compliance Framework
- ISA/IEC 62443 Industrial Automation and Control Systems Security
- ISO 31000:2018 Risk Management
- Operational Technology Cybersecurity Alliance (OTCSA)
- The SANS Institute Secure Architecture for Industrial Control Systems
- Industry-Specific Cybersecurity Resources
- Best Practice Security Controls
- Cyber threat awareness
- Threat Frameworks
- IoT Cloud Service Providers
- IoT Platform Providers
- Global System for Mobile Communications Association (GSMA)

