2 Min Read
Another Safety System Cyber Attack in Critical Infrastructure - What to know and how to be better prepared
Written by Mission Secure News Desk
April 12, 2019
What to know and how to be better prepared
A second critical infrastructure facility has been the target of a cyber attack aimed at its safety systems according to a report released Wednesday by FireEye. The attack comes from the same nation state actor behind the TRITON attack on a Saudi petrochemical facility's safety systems announced in late 2017, and now at a second facility. FireEye believes facilities at other critical infrastructure providers may also be targets, while companies may be unaware of the attacker's presence in their networks.
The 2017 TRITON attack focused on Schneider Triconex Safety Instrumented Systems and resulted in the accidental shutdown of a plant. The current attack uses a new set of custom tools developed by the attacker to traverse from IT to OT networks, maintain stealth and persistence. This attack also demonstrates TRITON, and the attackers behind it, are still working to improve their capabilities and carry out successful attacks against industrial control systems.
As with prior attacks the adversaries enter the IT networks, traverse into the operational technology (OT), gain access to a key engineering work station and ultimately target level 1 controllers, a safety instrumented system (SIS) in this case, where they install malware. This pattern is similar to numerous other control system focused attacks (i.e. Stuxnet, Ukraine 2016, Triton 2017 and more). As Mark Twain said, "history doesn't repeat but it often rhymes", and so too with control system cyber attacks.
The attackers spent nearly a year on the target's network before accessing the SIS workstation and utilized a number of techniques to evade detection. One example includes hitting target controllers off-hours when fewer engineers were around who could react to potential alarms. This new attack was uncovered when the attacker tried to install TRITON on the SIS controllers. FireEye's investigation and response is ongoing.
These types of attacks are not about stealing corporate information or data, rather they seek to obtain control of level 1 devices (i.e. programmable logic controllers, safety instrumented systems, RTUs) enabling the attacker to take control of the process and cause severe physical damage (i.e disconnect substations and shut down power, attempt to critically damage a chemical plant, control a dam, blow up a steel plant and more.)
Many plant operators feel protected because of firewalls separating IT from OT and having "air gapped" systems. With modern automation and the advancement of digitalization IT and OT are becoming inextricably connected, while third party remote monitoring and contractor access remain soft targets. Supply chain interdictions can also introduce malware into equipment before being installed at the factory.
The Purdue Model highlights attack vectors at level 2 (engineering workstation), and level 1 (controllers) with the goal of controlling the process at level 0. The patented MSi Platform is purpose built for industrial environments to provide monitoring AND protection across all of these levels.
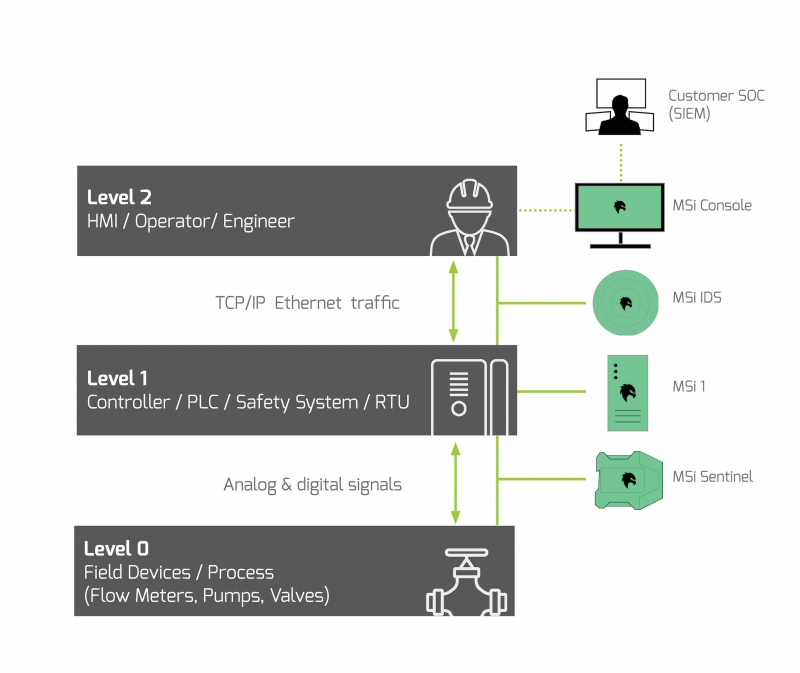
How should critical infrastructure providers prepare for and protect against cyber attacks?
Step 1: Asses
Every critical infrastructure provider should do a deep-dive cyber assessment of its operational technology (OT) networks and critical assets. The assessment should involve industry standards, site visits, and use technology with control system and OT cybersecurity experts who can analyze OT network traffic to identify high priority cyber risks.
Step 2: Design
Once a better understanding of the "As Is" state of OT networks exists, and critical risks have been identified, a secure design architecture should be developed with defense-in-depth across the OT including people, process and technology. This should also include a gap analysis to develop an actionable roadmap with priorities, estimated timing, level of investment and how this will mitigate OT cyber risks.
Step 3: Deploy
It is important to take remediation actions, including updating end of life equipment, tightening rules, updating policies and procedures, and deploying cybersecurity solutions that provide real-time OT network monitoring, asset discovery, as well as end point protection for controllers and safety systems with the ability to monitor critical I/O at level 0.
Mission Secure works with defense and industrial customers every day to assess their most critical OT cyber risks, enhance their cybersecurity defense architecture, and deploy the patented MSi Platform to provide visibility and protection down to levels 1 and 0 - where they matter the most.
Please contact us to learn more and speak with one of our OT cybersecurity professionals.
Originally published April 12, 2019, updated November 20, 2020.