Cyber Monitoring and Risk Reduction for Water and Wastewater Systems
Purpose-built OT cybersecurity solutions to lock down your assets and your operations
Securing vital resources against advanced cyber threats
Of all the resources on which civilization depends, a safe and reliable water supply may be the most essential of all.
Water and wastewater systems around the world rely on decades-old control networks that were never intended for external connectivity. Digitalization and IT/OT convergence have exposed these networks to rapidly evolving cyber threats from criminal groups and state-sponsored actors. A global leader in OT cybersecurity, Mission Secure offers proven technology and an active approach to keeping our water supply secure and resilient.
-
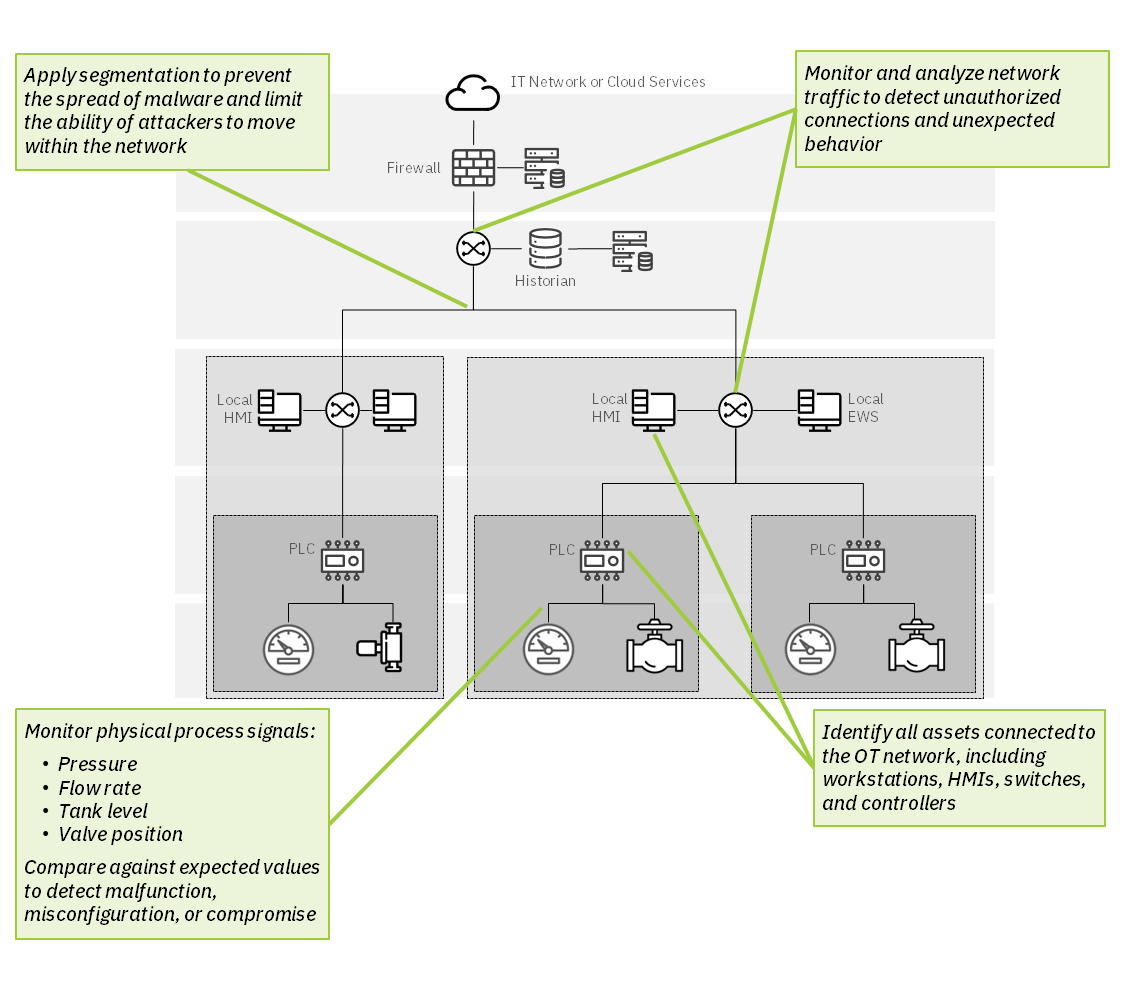
Identify and monitor OT assets
Detect and identify every asset connected to your OT network, and get real-time alerts on the changes that matter to you. -
Segment your network and control access
Prevent unauthorized connections, control lateral movement, and implement policies to protect critical assets. -
Demonstrate and maintain compliance
Mission Secure's OT security experts will help you develop a compliance roadmap and implement a solution tailored to meet your goals.
High Consequence Events: Water and Wastewater Systems
Given their critical importance to daily life, water and wastewater systems have several adverse scenarios to consider:- Disruption of the water supply due to control system manipulation or cyber-enabled equipment sabotage
- Disrupted operations due to ransomware attacks against IT networks
- Contamination of water supply through manipulation of filtration, disinfection, and monitoring processes
- Release of untreated sewage into the environment

Common Vulnerabilities: Water and Wastewater Systems
Digitalization has changed the way the water industry operates, but increased connectivity often means increased risk. Water and wastewater systems are subject to many common OT cyber vulnerabilities:- Unmanaged connectivity between IT and OT networks
- Unmanaged OT-to-cloud connections
- Unpatched workstations, HMIs, controllers, or switches in OT network
- Lack of authentication, segmentation, and other cybersecurity controls in OT network
.jpg?width=2000&name=iStock-1437909264(1).jpg)
Proactive cyber defense
Mission Secure enables water and wastewater system operators to gain full visibility and control over their OT networks, and take effective action to reduce not only the chance of an intrusion, but the real-world consequences of a cyber attack.
Layered protection for legacy and newly developed systems
Mission Secure is a leader in cybersecurity for operational technology and industrial control systems, helping customers gain visibility and control over their critical assets.With unmatched threat detection and policy enforcement capabilities, Mission Secure enables effective Zero Trust architectures for customers in oil and gas, power, water, smart cities, and other industries.

The Mission Secure Platform
Mission Secure delivers the only OT cybersecurity platform that enables complete control over your environment, including visibility, anomaly and threat detection, policy enforcement, and Level 0 signal validation.
-
Asset and Network Visibility
Discover and visualize every asset and every network connection in your OT environment
Learn More » -
Anomaly and Threat Detection
Identify unexpected or unauthorized activity, from Level 0 signals to cloud connections
Learn More » -
Policy Enforcement
Segment your network and enforce granular policies for true Zero Trust cybersecurity
Learn More » -
Signal Integrity Validation
Monitor physical process signals to detect threats and prevent system damage
Learn More »
Protect your OT network
Mission Secure delivers the technology and expertise you need to begin your journey toward Zero Trust, and to implement intelligent, resilient cybersecurity in your OT network, while enhancing—not disrupting—reliability and productivity.
Get in contact to schedule a consultation with our OT cybersecurity experts today!
Today, public water systems are frequent targets of malicious cyber activity, which has the same or even greater potential to compromise the treatment and distribution of safe drinking water as a physical attack.
U.S. EPA Memorandum: “Addressing PWS Cybersecurity in Sanitary Surveys or an Alternate Process”
Resources
-
Datasheet
Mission Secure Platform
Read More » -
Guide
A Comprehensive Guide to Operational Technology (OT) Cybersecurity
Read More » -
Case Study
Top 50 City Secures Traffic Signal System and Connected Vehicle Technology with Mission Secure
Read More »