Guide
A Comprehensive Guide to Maritime Cybersecurity
In this guide, we will help you navigate the ins and outs of maritime cybersecurity, address cybersecurity challenges and compliance considerations, and get you geared up to establish your maritime cybersecurity action plan.
Download your Ebook
Take your reading offline and get an in-depth look at industrial control system (ICS) & operational technology (OT) cybersecurity for maritime & shipping.
Download the Ebook
Table of Contents
Ships and other vessels may seem like unusual targets for cyberattacks. But with their growing use of industrial control systems (ICS) and satellite communications, hackers have a new playground that’s ripe for attack.”
Maritime is one of the oldest industries and lifeblood of the global economy, accounting for the carriage of 90% of world trade. Ships and other vessels may seem like unusual targets for cyber-attacks. But with their growing use of industrial control systems (ICS) and satellite communications, hackers have a new playground that’s ripe for attack.
In a 2020 Safety at Sea and BIMCO Maritime Cyber Security survey, despite the majority of respondents (77%) viewing cyber-attacks as a high or medium risk to their organizations, few appear to be prepared for the aftermath of such an attack. 64% of respondents said their organization has a business continuity plan in place to follow in the event of a cyber incident, but only 24% claimed it was tested every three months, and only 15% said that it was tested every six to 12 months. Only 42% of respondents said that their organization protects vessels from operational technology (OT) cyber threats, and some respondents went so far as to describe their company policy to OT cyber risk as “careless.”
-
77%
77% view cyber-attacks as high or medium risks
YET
-
42%
only 42% protect vessels from OT cyber threats.
As hackers become even more sophisticated in their tactics, it’s inevitable that cyber-attacks against OT on ships are becoming the norm rather than the exception. It’s time for the maritime industry to take a look at every aspect of their ship operations to ensure they’re protected and resilient against these growing threats.
In this guide, we will help you navigate the ins and outs of maritime cybersecurity, address cybersecurity challenges and compliance considerations, and get you geared up to establish your maritime cybersecurity action plan.
Let's get started
What is Maritime Cybersecurity?
Maritime cybersecurity is the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance, and technologies used to protect maritime organizations, their vessels, and their cyber environment.
...the collection of tools, policies, security concepts, security safeguards, guidelines, risk management approaches, actions, training, best practices, assurance, and technologies used to protect maritime organizations, their vessels, and their cyber environment.
And according to the International Maritime Organization (IMO), maritime cyber risk refers to a measure of the extent to which a technology asset could be threatened by a potential circumstance or event, which may result in shipping-related operational, safety, or security failures as a consequence of information or systems being corrupted, lost or compromised.
Many of the globally connected networks and infrastructures at sea still leverage legacy technologies that were not built to be connected to the Internet. These complex networks include a blend of information technology (IT) and operational technology (OT) systems (we’ll cover those in the next section) used by internal crew and third-party vendors, extending the potential for a compromise by hackers or insider threats.
There was a time when connectivity on a vessel was minimal, and ship control engineers addressed security issues with air gapping to physically isolate a secure network from unsecured networks. By definition, an air-gapped system is neither connected to the Internet nor any other system. But now, using something as simple as a USB flash drive or unsecured Wi-Fi connection, a malicious hacker or even an inexperienced insider could infiltrate and infect critical systems. This development is especially concerning given the connectivity of modern maritime vessels.
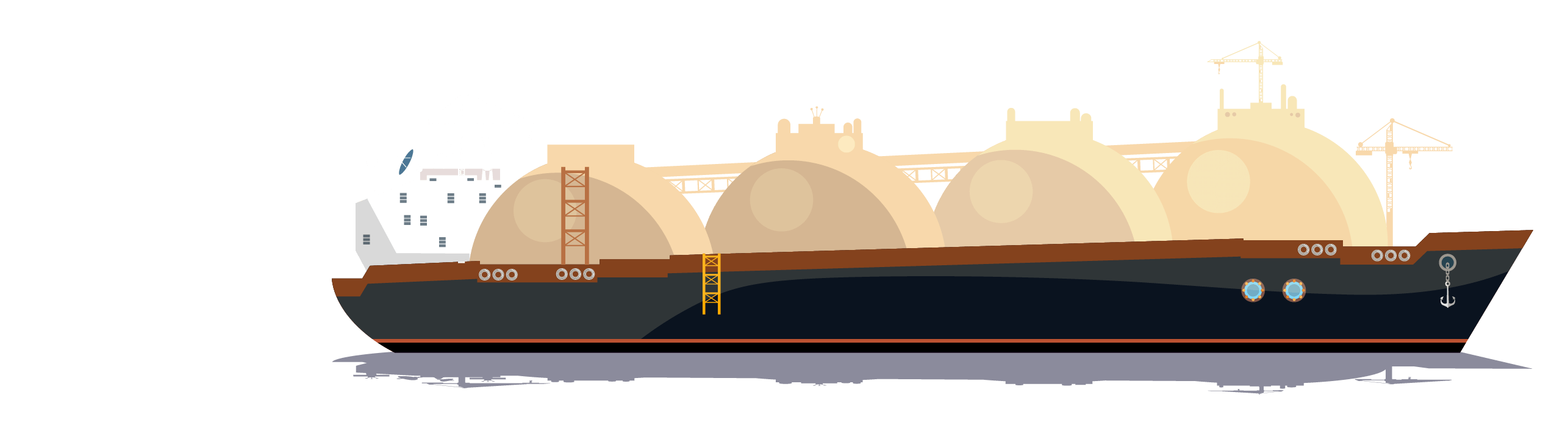
Connectivity on a Modern Maritime Vessel
-
Bridge Control
Bridge systems, automatic identification system (AIS), voyage data recorder (VDR), automatic radar plotting aid (ARPA) -
Propulsion & Power
Engine control, steering, fuel management, onboard machinery monitoring and control, generators -
Navigation
GPS/GNSS, electronic chart display and information system (ECDIS), radar, weather systems
-
Loading & Stability
Ballast systems, hull stress, stability control, stability decision support systems, cargo management systems -
Safety Systems
Fire and flood control, tracking, shipboard security, CCTV, emergency shutdown -
Communications
Satellite internet communications, ship-to-shore, ship-to-ship, handheld radios, voice-over-IP (VoIP)
-
Operations Security
Human-machine interfaces (HMIs), logic controllers (PLCs), digital and analog sensors, electronics -
Network Security
Firewalls, segmentation devices, antivirus software, software updates, vendor patches -
Physical Security
Server rooms, access control, bridge, machinery spaces, network infrastructure
-
Ship Networks
Email, customs and immigration, personnel administration, maintenance and spares management -
Crew Network
Email, Wi-Fi, wired, bring your own device (BYOD) -
Supply Chain
Remote or on-shore vendor updates, maintenance, and administration
Whether moving dry or liquid bulk, containers or cars, crude oil, products, or chemicals, the maritime industry is a critical backbone of our global economy. Protecting a vessel’s critical operations from cyber threats poses unique challenges with operation centers and fleets of numerous classes and vintages spread across the world, increasingly digitalized operations, and a complex environment merging IT with industrial control systems (ICS) and operational technology (OT).

Maritime Cyber Attacks: Real-World Lessons Learned from Maritime Cybersecurity Incidents
Read MoreHow do IT and OT Cybersecurity Differ?
Operational technology (OT) is hardware and software that detects or causes a change through the direct monitoring and control of industrial equipment, assets, processes, and events. In contrast, information technology covers the entire spectrum of technologies for information processing, including software, hardware, communications technologies, and related services.
Before we delve into the cybersecurity challenges affecting the maritime industry, let’s take a step back and examine some of the differences between IT and OT systems. Some of the differences in system requirements include:
Differences in System Requirements*
IT System Requirements |
OT System Requirements |
|
|---|---|---|
| Performance |
|
|
| Availability/Reliability |
|
|
| Risk Management |
|
|
| System Operations |
|
|
| Resource Constraints |
|
|
| Communications |
|
|
| Component Lifetime |
|
|
| Component Location |
|
|
*Table modified from NIST Special Publication 800-82, Revision 2 (Table 2-1)
From a cybersecurity perspective, OT and IT are different in several ways. On staffing, there is a cybersecurity specialization on the IT side. Professionals have been specifically trained and certified in application security, network security, or other security disciplines. In OT, those tasked with security are usually operational technology people. As part of their day job, they have to also deal with security—it's an add-on, not a specialization.
OT and IT are different, especially in attack outcomes. An attack on IT could lead to data theft, while an attack on OT could lead to injury or loss of life, asset damage, or environmental impact. Traditional cybersecurity measures fail to protect vessels from cyber-attacks and leave the OT network exposed, falling short on providing the visibility and protection required for cyber-physical processes underlying in the maritime industry. And with the convergence of IT and OT, organizations must balance the use of traditional IT security tools at the network and endpoint layer with specialized security tools designed for OT requirements.
CIA vs. CAIC
One of the best ways to distinguish the difference between IT security and OT security is the CIA triad. The CIA triad is a model designed to guide policies for information security within an organization. Ranked in order of priority, CIA stands for confidentiality, integrity, and availability.
-
INFORMATION TECHNOLOGY (IT)
CIA
Confidentiality
Integrity
Availability
VS
-
OPERATIONAL TECHNOLOGY (OT)
CAIC
Control
Availability
Integrity
Confidentiality
IT Priorities vs. OT Priorities
By contrast, the OT benchmark is CAIC, which stands for control, availability, integrity, and confidentiality. Although OT cares about the same security properties, they’re ranked in a different order, with safety forever being the top priority.
Learn More
-
- Dive in and learn more about the CIA triad
-
- IT/OT Convergence is Hard Work — Here’s Why It’s Worth It
In the CAIC model, availability is more important than confidentiality because of the nature of processes and the impact that shutting down and restarting systems can have on productivity. Control refers to the ability to control a process and change a state when needed in a safe and secure manner. Since it can impact people, safety, and assets, it will have the highest priority when considering the attack surface of any system.

Maritime Security Challenges: The Physical Impact of Maritime Cyber Threats.
Read MoreWhat are the Cybersecurity Challenges Affecting the Maritime Industry?
Many of the common cybersecurity challenges that affect the maritime industry mirror those in other industries that deal with IT networks:
- No clear understanding of all systems and devices on the OT network across a fleet or operation
- Lack of visibility into each vessel’s OT networks
- Lack of real-time monitoring or segmentation of the OT network
- Inadvertently connected IT and OT networks
- Use of unsecured wireless networks
- 24/7 remote access granted to third-party OEMs
- Lack of visibility into third-party OEM networks (black box)
- Poor physical security controls
- Lack of cybersecurity awareness among the crew, employees, and contractors
Potential Maritime Cybersecurity Attacks
Cybersecurity is not just about preventing hackers from gaining access to systems and information. It is also about protecting digital assets and data, ensuring business continuity, and ensuring that the maritime industry is resilient to external and internal threats. It is crucial to keep ship systems safe from physical attacks and to ensure the integrity of supporting systems.
The complexities associated with vessels and tankers make them vulnerable to high-impact attacks. Cyber incidents can last for hours, days, or weeks. When one ship is impacted, it can often spread malware to sister vessels via the corporate network. Some of the potential attacks that can cripple a vessel's operations include:
- An attack on an OEM network or third-party supplier that spreads to their client’s on-vessel OT network
- An attack on a satellite provider that gains access to a vessel’s IT/OT network
- Exploited cyber vulnerabilities that grant access to a vessel’s OT network and provide various attack options, including:
- GPS/navigation system attack
- Open/close critical valves
- Propulsion and rudder control
- Ballast control
- Ransomware/Malware
- Gain full administrative privileges
A compromised ship system could initiate physical harm to the IT and OT systems, personnel, and cargo, potentially endangering lives or causing the loss of the ship and the loss of sensitive information, including commercially-sensitive or personal data.
Recent Maritime Cybersecurity Attacks
Cybersecurity attacks are not new in the maritime industry, but many incidents go unreported. There is an ongoing reluctance to share critical information with law enforcement agencies and collaborate with other peers to share threat information to thwart future attacks and build cybersecurity best practices. And with the rate of maritime cyberattacks increasing by 900% since 2017, the number of reported incidents is set to reach a record by the end of 2020. A sampling of cyberattacks affecting the maritime industry in 2020 alone shows that all organizations can be susceptible to attack, regardless of size or location:
-
APRIL 2020
Mediterranean Shipping Company (MSC)
Geneva, Switzerland
Incident Type: Malware
Malware: Unknown -
APRIL 2020
DESMI
Denmark
Incident Type: Ransomware
Malware: Unknown
-
MAY 2020
Shahid Rajaee Port Terminal
Iran
Incident Type: Unidentified Hacker(s)
Malware: Unknown -
MAY 2020
Toll
Australia
Incident Type: Ransomware
Malware: Nefilim
-
MAY 2020
Anglo-Eastern
Hong Kong
Incident Type: Ransomware
Malware: Unknown -
JUNE 2020
Vard
International
Incident Type: Ransomware
Malware: Unknown
-
AUGUST 2020
Carnival Corporation
International
Incident Type: Ransomware
Malware: Unknown -
SEPTEMBER 2020
CMA CGM SA
Asia-Pacific
Incident Type: Ransomware
Malware: Ragnar Locker
-
SEPTEMBER 2020
US Tugboat
Louisiana, United States
Incident Type: Phishing Email
Malware: Unknown -
OCTOBER 2020
The International Maritime Organization (IMO)
International
Incident Type: Malware
Malware: Unknown
-
OCTOBER 2020
Iran Port Authority
Iran
Incident Type: Unidentified Hacker(s)
Malware: Unknown -
OCTOBER 2020
Red Funnel
United Kingdom
Incident Type: Unidentified Hacker(s)
Malware: Unknown
-
NOVEMEBER 2020
Port of Kennewick
Washington, United States
Incident Type: Ransomware
Malware: Unknown
Maritime Security Incidents: NotPetya
One of the most significant and most devastating cyberattacks to date is NotPetya, which caused more than $10 billion in total damages in June 2017. Primarily targeted at Ukrainian companies, NotPetya’s reach went far beyond Ukraine and hit many large organizations, including pharmaceutical company Merck, delivery company FedEx and Danish shipping giant Maersk (A.P. Møller-Maersk), which handles one out of seven containers shipped globally.
Maersk was hit particularly hard, to the tune of $300 million and lost most of its data:
- All end-user devices, including 49,000 laptops and print capability, were destroyed
- All of their 1,200 applications were inaccessible, and approximately 1,000 were destroyed
- Data was preserved on back-ups, but the applications themselves couldn't be restored as they would be reinfected
- 3,500 of their 6,200 servers were destroyed and couldn’t be reinstalled
- All fixed-line phones were inoperable due to the network damage, and because they'd been synchronized with Outlook, all contacts had been wiped from mobiles, severely hampering any coordinated response

The Maritime Executive: Playing Catch-up with Cybersecurity
"If we had to place a number on the 90,000 commercial vessels worldwide, perhaps 5% to 10% are prepared today for full compliance and/or to defend against cyberattacks."
Read the Full ArticleMaritime Security Incidents: COVID-19 Pandemic
More recently, with the onset of the COVID-19 pandemic, the number of shipping cyberattacks has jumped 400% since February.
Travel restrictions, social distancing, and the economic recession are having an impact on the maritime industry and its ability to protect itself. OEMs, technicians, and vendors are forced to connect standalone systems to the Internet to service them. Ship and offshore staff are connecting their OT systems to onshore networks for brief periods to carry out diagnostics and upload software updates, leaving endpoints, critical systems, and components susceptible to attack since they are no longer segmented. Also, stress levels of short-staffed crews can leave vessels vulnerable to scams, misconfigurations, and human error.

Maritime Security Incidents: Disruptive Cyber-attack Cripples Port Facility
Learn MoreWhat are the Maritime Cybersecurity Compliance Measures You Need to Consider?
Some of the maritime cybersecurity compliance measures you need to consider include IMO Resolution MSC. 428(98), ISA/IEC 62443, ISO/IEC 27001, and TMSA. There are also other industry and regulatory standards that you need to adhere to based on your country of operation and nature of your vessels’ operations.
As connectivity and reliance on the Internet are now the norms with many technologies essential to the operation and management of vessels, the security, safety, and reliability of these systems is paramount. To that end, the maritime industry is recognizing the need for cybersecurity oversight to ensure the effective management and mitigation of evolving cyber threats. Let’s take a look at a few of the compliance measures in depth:
IMO Resolution MSC.428(98)
A significant cybersecurity compliance deadline facing the maritime industry is the International Maritime Organization’s (IMO) Resolution MSC.428(98), which encourages administrations to ensure that cyber risks are appropriately addressed in existing safety management systems (as defined in the ISM Code) no later than the first annual verification of the company's Document of Compliance after January 1, 2021. These are based on the NIST 800-53 R4 cybersecurity framework and tailored for the Maritime industry to provide a standardized approach for applying and evaluating security controls within an OT environment.
These guidelines provide recommendations and include functional elements that support effective cyber risk management:
- Identify: Define personnel roles and responsibilities for cyber risk management and identify the systems, assets, data, and capabilities that, when disrupted, pose risks to ship operations.
- Protect: Implement risk control processes and measures, and contingency planning to protect against a cyber-event and ensure continuity of shipping operations.
- Detect: Develop and implement activities necessary to detect a cyber-event in a timely manner.
- Respond: Develop and implement activities and plans to provide resilience and to restore systems necessary for shipping operations or services impaired due to a cyber event.
- Recover: Identify measures to back-up and restore cyber systems necessary for shipping operations impacted by a cyber-event.

Overview: IMO 2021 Cybersecurity
Learn more about what is required to comply with the new IMO cybersecurity resolution. This regulatory overview summarizes key parts of the IMO 2021 cybersecurity measures, complete with cross-references to ISO/IEC 27001 and the Guidelines on Cyber Security on Board Ships.
Read the Full ArticleISA/IEC 62443
The ISA/IEC 62443 series of standards have been developed jointly by the ISA99 committee and IEC Technical Committee 65 Working Group 10 customized to address the need to design cybersecurity robustness and resilience into industrial automation control systems (IACS). An IACS is defined as a collection of personnel, hardware, software, and policies involved in the operation of the industrial process, and that can affect or influence its safe, secure, and reliable operation. The ISA/IEC 62443 Series Standards and Technical Reports are arranged in four groups:
ISA/IEC 62443 Family of Standards
ISA-62443-1-1
Terminology, concepts, and models
ISA-62443-1-2
Master glossary of terms and abbreviations
ISA-62443-1-3
System security conformance metrics
ISA-62443-1-4
IACS security lifecycle and use-cases
ISA-62443-2-1
Establishing an IACS security program
ISA-62443-2-2
IACS security program ratings
ISA-62443-2-3
Patch management in the IACS environment
ISA-62443-2-4
Security program requirements for IACS service providers
ISA-62443-2-5
Implementation guide for IACS asset owners
ISA-62443-3-1
Security technologies for IACS
ISA-62443-3-2
Security risk assessment for system design
ISA-62443-3-3
System security requirements and security levels
ISA-62443-4-1
Product security development lifecycle requirements
ISA-62443-4-2
Technical security requirements for IACS components
General—This group includes documents that address topics that are common to the entire series:
- Part 1-1: Terminology, concepts, and models introduce the concepts and models used throughout the series.
- Part 1-2: Master glossary of terms and definitions is a list of terms and abbreviations used throughout the series.
- Part 1-3: System security conformance metrics describe a methodology to develop quantitative metrics derived from the process and technical requirements in the standards.
- Part 1-4: IACS security lifecycle and use cases provide a more detailed description of the underlying lifecycle for IACS security, as well as several use cases that illustrate various applications.
Policies and Procedures—Documents in this group focus on the policies and procedures associated with IACS security:
- Part 2-1: Establishing an IACS security program describes what is required to define and implement an effective IACS cybersecurity management system.
- Part 2-2: IACS security program ratings provide a methodology for evaluating the level of protection provided by an operational IACS against the requirements in the ISA/IEC 62443 Series of standards.
- Part 2-3: Patch management in the IACS environment provides guidance on patch management for ACS.
- Part 2-4: Security program requirements for IACS service providers specify requirements for IACS service providers such as system integrators or maintenance providers.
- Part 2-5: Implementation guidance for IACS asset owners provides guidance on what is required to operate an effective IACS cybersecurity program.
System Requirements—The documents in the third group address requirements at the system level:
- Part 3-1: Security technologies for IACS describes the application of various security technologies to an IACS environment.
- Part 3-2: Security risk assessment for system design addresses cybersecurity risk assessment and system design for IACS.
- Part 3-3: System security requirements and security levels describe the requirements for an IACS system based on the security level.
Component Requirements—The fourth and final group includes documents that provide information about the more specific and detailed requirements associated with the development of IACS products:
- Part 4-1: Product security development life cycle requirements describe the requirements for a product developer’s security development lifecycle.
- Part 4-2: Technical security requirement for IACS components describes the requirements for IACS Components based on the security level. Components include Embedded Devices, Host Devices, Network Devices, and Software Applications.
ISO/IEC 27001
ISO 27001 is a technology-neutral, vendor-neutral information security management standard that offers a prescription of the features of an effective information security management system (ISMS). The mandatory requirements for ISO 27001 are defined in its clauses 4 through 10 – to receive certification or to pass an audit, your ISMS must conform to these requirements.
-
CLAUSE 4
Context of the Organization
defines requirements for understanding external and internal issues, interested parties and their requirements, and defining the ISMS scope.
-
CLAUSE 5
Leadership
defines top management responsibilities, setting the roles and responsibilities, and contents of the top-level Information Security Policy.
-
CLAUSE 6
Planning
defines requirements for risk assessment, risk treatment, Statement of Applicability, risk treatment plan, and setting the information security objectives.
-
CLAUSE 7
Support
defines requirements for the availability of resources, competencies, awareness, communication, and control of documents and records.
-
CLAUSE 8
Operation
defines the implementation of risk assessment and treatment, as well as controls and other processes needed to achieve information security objectives.
-
CLAUSE 9
Performance Evaluations
defines requirements for monitoring, measurement, analysis, evaluation, internal audit, and management review.
-
CLAUSE 10
Improvement
defines requirements for nonconformities, corrections, corrective actions, and continual improvement.
TMSA
In 2004, the Oil Companies International Marine Forum (OCIMF) introduced the Tanker Management and Self Assessment (TMSA) program to help vessel operators assess, measure, and improve their safety management systems. It complements industry quality codes and is intended to encourage self-regulation and promote continuous improvement among tanker operators.
The TMSA framework is based on 12 elements of management practice. Each element includes a clear objective and a set of supporting KPIs:
- Management, leadership, and accountability
- Recruitment and management of shore-based personnel
- Recruitment and management of vessel personnel
- Reliability and maintenance standards
- Navigational safety
- Cargo, ballast and mooring operations
- Management of change
- Incident investigation analysis
- Safety management
- Environmental management
- Emergency preparedness and contingency planning
- Measurement, analysis, and improvement
Guidelines on activities, grouped into four stages, are provided to help you meet these objectives. You should work through the 12 elements to produce as accurate and substantive an assessment as possible. You can use the assessment to conduct a gap analysis to identify which elements and stages have yet to be attained and how best to develop a performance improvement program.

IMO 2021: Three Steps to Ensure IMO/ISM Cybersecurity Compliance
Learn MoreHow Do You Start Designing Your On-Vessel Maritime Cybersecurity Action Plan?
Your maritime cybersecurity action plan will take some time to pull together, you can do several things in the short-term to jumpstart your efforts and establish an initial baseline of cybersecurity for your vessels:
Your On-Vessel Maritime Cybersecurity Action Plan
Click on each item to cross it off your maritime cybersecurity to-do list. Select the expander next to each item to get more information.
Update the admin password on critical systems and devices on your OT network
Make sure you change the admin password on your critical systems and devices from the manufacturer default. Hackers can quickly identify and access internet-connected systems that use shared default passwords. It is imperative to change default manufacturer passwords and restrict network access to critical vessel systems.
Update your passwords regularly and use multi-factor authentication, where possible
If you do not have one in place already, deploy a password management system for your critical computers and devices on your OT network. This includes adding multi factor authentication, where possible, and changing passwords (including any that are shared) on a regular basis.
Make sure your critical systems and devices are not accessible via the Internet
Most providers offer a private IP address space to keep hackers from reaching your systems over the Internet. You can determine if your vessel terminals are public by entering the IP address in a browser to see if you can route to the terminal web interface.
Update the software on critical systems and devices
Most updates include fixes for security flaws, so make sure your systems are running the latest software versions and ensure they are updated every time the manufacturer publishes an update.
Secure USB ports on all ship systems
Lock down USB access to prevent malware from entering vessel systems. If critical systems can only be updated by USB, keep dedicated USB keys in a secure location.
Segment your bridge, engine room, crew, Wi-Fi and business networks on board
If a device on your vessel is compromised, segmented networks will ensure critical systems are not susceptible to an attacker. Ensure that the crew’s personal devices and laptops do not have access to navigation systems and other critical areas of the ship’s network.
Educate your crew about cybersecurity
Establish a cybersecurity training program for your crew. You can also take advantage of complimentary resources like ESET’s online cybersecurity awareness training and the Be Cyber Aware At Sea campaign to raise cybersecurity awareness and help train your crew to avoid opening the vessel to compromise. Security starts with your people.
Maritime Security: Getting Started with Your Action Plan
There is so much to consider when developing a maritime security plan. Your plan must include a significant cybersecurity component to ensure the safety of your vessels and offshore operations from the growing number of maritime cyber threats. As ships become more sophisticated in the digital era, at the same time, crews are shrinking and dedicated resources to cybersecurity may be scarce. But cybersecurity cannot be an afterthought – it needs to be elevated as a board-level priority issue.
We’ve touched on some of the security frameworks and compliance considerations that you can leverage in your planning efforts. Establishing your cybersecurity plan will not happen overnight. The burden and responsibility of cybersecurity fall on everyone – process and cultural changes will need to happen for an effective cybersecurity plan.
As you begin your in-depth cybersecurity planning efforts, the cyber risk management approach * from “The Guidelines on Cyber Security Onboard Ships,” produced and supported by BIMCO, Cruise Lines International Association (CLIA), International Chamber of Shipping (ICS), International Association of Dry Cargo Shipowners (INTERCARGO), InterManager, INTERTANKO, International Union of Marine Insurance (IUMI), Oil Companies International Marine Forum (OCIMF), and World Shipping Council (WSC) guides shipowners and operators on procedures and actions to maintain the security of cyber systems in their organization and onboard their vessels.
Cyber Risk Management Approach
from The Guidelines on Cyber Security Onboard Ships
-
Identify Threats
- Understand the external cybersecurity threats to the ship.
- Understand the internal cybersecurity threat posed by inappropriate use and lack of awareness.
-
Identify Vulnerabilities
-
Develop inventories of onboard systems with direct and indirect communication links.
-
Understand the consequences of a cybersecurity threat on these systems.
-
Understand the capabilities and limitations of existing protection measures.
-
-
Assess Risk Exposure
-
Determine the likelihood of vulnerabilities being exploited by external threats.
-
Determine the likelihood of vulnerabilities being exposed by inappropriate use.
-
Determine the security and safety impact of any individual or combination of vulnerabilities being exploited.
-
-
Develop protection & detection measures
-
Reduce the likelihood of vulnerabilities being exploited through protection measures.
-
Reduce the potential impact of a vulnerability being exploited.
-
-
Establish contingency plans
- Develop a prioritized contingency plan to mitigate any potential identified cyber risk.
-
Respond & Recover
- Respond to and recover from cybersecurity incidents using the contingency plan.
- Assess the impact of the effectiveness of the response plan and re-assess threats and vulnerabilities.
Identify Threats
The cyber risk is specific to the company, ship, operation, and/or trade. When assessing the risk, organizations should consider any specific aspects of their operations that might increase their vulnerability to cyber incidents.
There are motives for organizations and individuals to exploit cyber vulnerabilities. There is the possibility that company personnel, onboard and ashore, could compromise cyber systems and data. In general, the organization should realize that this may be unintentional and caused by human error when operating and managing IT and OT systems or failure to respect technical and procedural protection measures. There is, however, the possibility that actions may be malicious and are a deliberate attempt by a disgruntled employee to damage the company and the ship.
Identify Vulnerabilities
It is recommended that a shipping company performs an assessment of the potential threats that may be faced. This should be followed by an assessment of the systems and onboard procedures to map their robustness to handle the current level of threats. The result should be a strategy centered around the key risks.
Standalone systems will be less vulnerable to external cyberattacks compared to those attached to uncontrolled networks or directly to the Internet. Care should be taken to understand how critical onboard systems might be connected to uncontrolled networks.
Assess Risk Exposure
Cyber risk assessment should start at the senior management level of a company, instead of immediately delegated to the ship security officer or the head of the IT department:
- Initiatives to heighten cybersecurity and safety may also affect standard business procedures and operations, rendering them more time consuming and costly. This usually becomes a senior management level decision to evaluate and decide on risk mitigation.
- Some initiatives, which would improve cyber risk management, are related to business processes, training, the safety of the vessel, and the environment – not to IT systems, and should be anchored organizationally outside the IT department.
- Initiatives which heighten cyber awareness may change how the company interacts with customers, suppliers, and authorities, and impose new requirements on the co-operation between the parties. It is a senior management level decision whether and how to drive these changes in relationships.
Develop Protection and Detection Measures
The outcome of the company's risk assessment and subsequent cybersecurity strategy should be a reduction in risk to be as low as reasonably practicable. At a technical level, this would include the necessary actions to be implemented to establish and maintain an agreed level of cybersecurity. It is crucial to identify how to manage cybersecurity onboard and delegate responsibilities to the master, responsible officers, and, when appropriate, the company security officer.
Establish Contingency/Incident Response (IR) Plans
When developing contingency plans for implementation onboard ships, it is important to understand the significance of any cyber incident and prioritize response actions accordingly.
Any cyber incident should be assessed to estimate the impact on operations, assets, etc. In most cases, and with the exception of load planning and management systems, a loss of IT systems onboard, including a data breach of confidential information, will be a business continuity issue and should not have any impact on the safe operation of the vessel.
The loss of OT systems may have a significant and immediate impact on the safe operation of the vessel. Should a cyber incident result in the loss or malfunctioning of OT systems, it will be essential that effective actions are taken to help ensure the immediate safety of the crew, ship, cargo, and protection of the marine environment. Your crews should be trained regularly on the response plans. These plans should be regularly practiced by vessel crews, officers, and IT support management and staff – similar to the safety response exercises that are routinely done today. Third-party system providers on board the vessels should be included and required to be part of these IR exercises and planning.
Respond to and Recover from Cyber Security Incidents
It is important to understand that cyber incidents may not disappear by themselves. If, for example, the emergency chart display and information system (ECDIS) has been infected with malware, starting up the back-up ECDIS may cause another cyber incident. Therefore, it is recommended to plan how to carry out the cleaning and restoration of infected systems.
Disaster recovery (DR) plans need to be an integral part of any maritime cybersecurity plan. This includes the preservation of cyber data for forensic purposes in addition to the restoration and protection of your OT processes and ship controls. These plans should also be exercised regularly and updated as necessary both at sea and on shore. Any third-party system providers you partner with should be included and required to be part of the planning and execution of these DR exercises. Any knowledge you obtain about previously identified cyber incidents should be used to improve the response plans of all ships in your company's fleet, and you should consider an information strategy for such incidents.
We’ve touched on some of the security frameworks and compliance considerations that you can leverage in your planning efforts. Establishing your cybersecurity plan will not happen overnight. The burden and responsibility of cybersecurity fall on everyone – process and cultural changes will need to happen to ensure your success in developing an effective cybersecurity plan.
Your Vessel Exposed: 10 Potential Surprises to Expect from Your Maritime Cyber Risk Management Assessment
Learn MoreMaritime Cybersecurity Resources
Need help getting started on your cybersecurity action plan or just want to learn more about maritime security? Here are some resources dedicated to maritime cybersecurity that can get you on the right track:
-
NIST Cybersecurity Framework: This framework helps organizations focus on using business drivers to guide cybersecurity activities and considering cybersecurity risks as part of their risk management processes.
-
NIST Guide to Industrial Control Systems (ICS) Security: This document provides an overview of ICS and typical system topologies, identifies typical threats and vulnerabilities to these systems, and provides recommended security countermeasures to mitigate the associated risks.
-
International Maritime Organization (IMO) Guidelines on Maritime Cyber Risk Management: These guidelines provide high-level recommendations on maritime cyber risk management to safeguard shipping from current and emerging cyber threats and vulnerabilities.
-
ISA/IEC 62443: The 62443 series of standards was developed jointly by the ISA99 committee and IEC Technical Committee 65 Working Group 10 to address the need to design cybersecurity robustness and resilience into industrial automation control systems
-
ISO/IEC 27001: ISO/IEC 27001 provides requirements for an information security management system.
-
Tanker Management and Self Assessment (TMSA): The TMSA program provides companies with the means to improve and measure their own safety management systems.
-
The Guidelines on Cyber Security Onboard Ships: This document offers guidance to shipowners and operators on procedures and actions to maintain the security of cyber systems in their organization and onboard their vessels.
