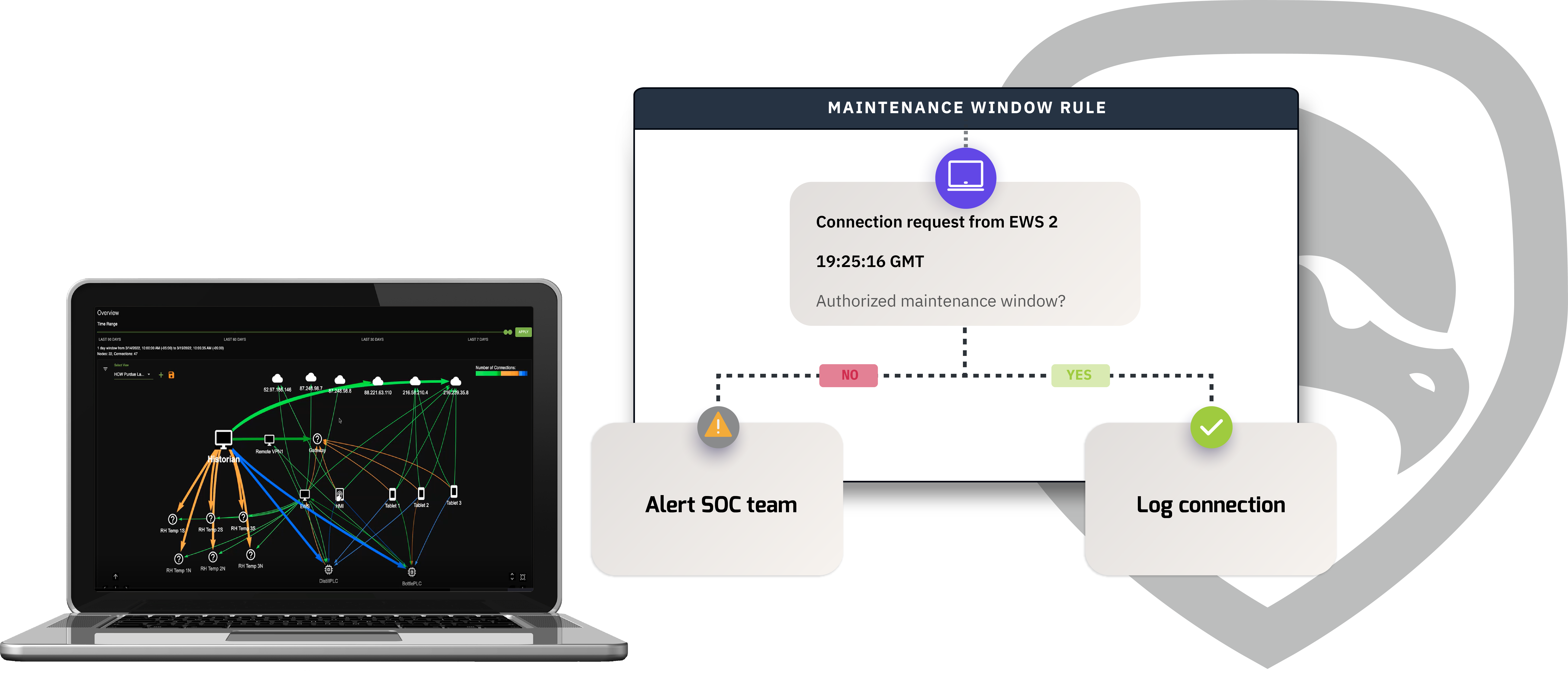
Vulnerability Management
Make sense of risk in your OT environment. Mission Secure makes it easy to identify, analyze, and prioritize the vulnerabilities associated with your industrial assets.
Identify, analyze, and prioritize cyber vulnerabilities in your OT and ICS environment
-
Accurate Detection
Get reliable, real-time data on vulnerabilities found on your industrial assets -
Advanced Visualization
Make sense of your risk exposure with intuitive, easy-to-navigate risk dashboards -
Effective Remediation
Make your remediation efforts more efficient and effective by focusing on the vulnerabilities that matter
Making OT Vulnerability Data Manageable
Tens of thousands of new cybersecurity vulnerabilities are reported each year. Some are purely theoretical, some are potentially problematic, and some are being actively exploited in cyber attacks today. OT asset owners need tools to help them cut through the noise and get a clear understanding of their risk exposure and priorities.
Mission Secure makes OT vulnerability data manageable by providing detailed analysis and meaningful context that helps you know which assets are vulnerable and which vulnerabilities represent the biggest risks to your operations.
Start with a comprehensive asset inventory
Mission Secure's asset discovery and querying engine identifies and interrogates OT assets to build a comprehensive, detail-rich asset inventory. We capture dozens of attributes including product code, firmware version, OS version, and installed applications to ensure a complete view of each asset's security posture.
Visualize and prioritize your vulnerabilities
Mission Secure provides multiple ways to visualize your risk landscape, including an intuitive vulnerability dashboard that makes it easy to see which assets represent the biggest targets for ransomware and cyber-enabled sabotage.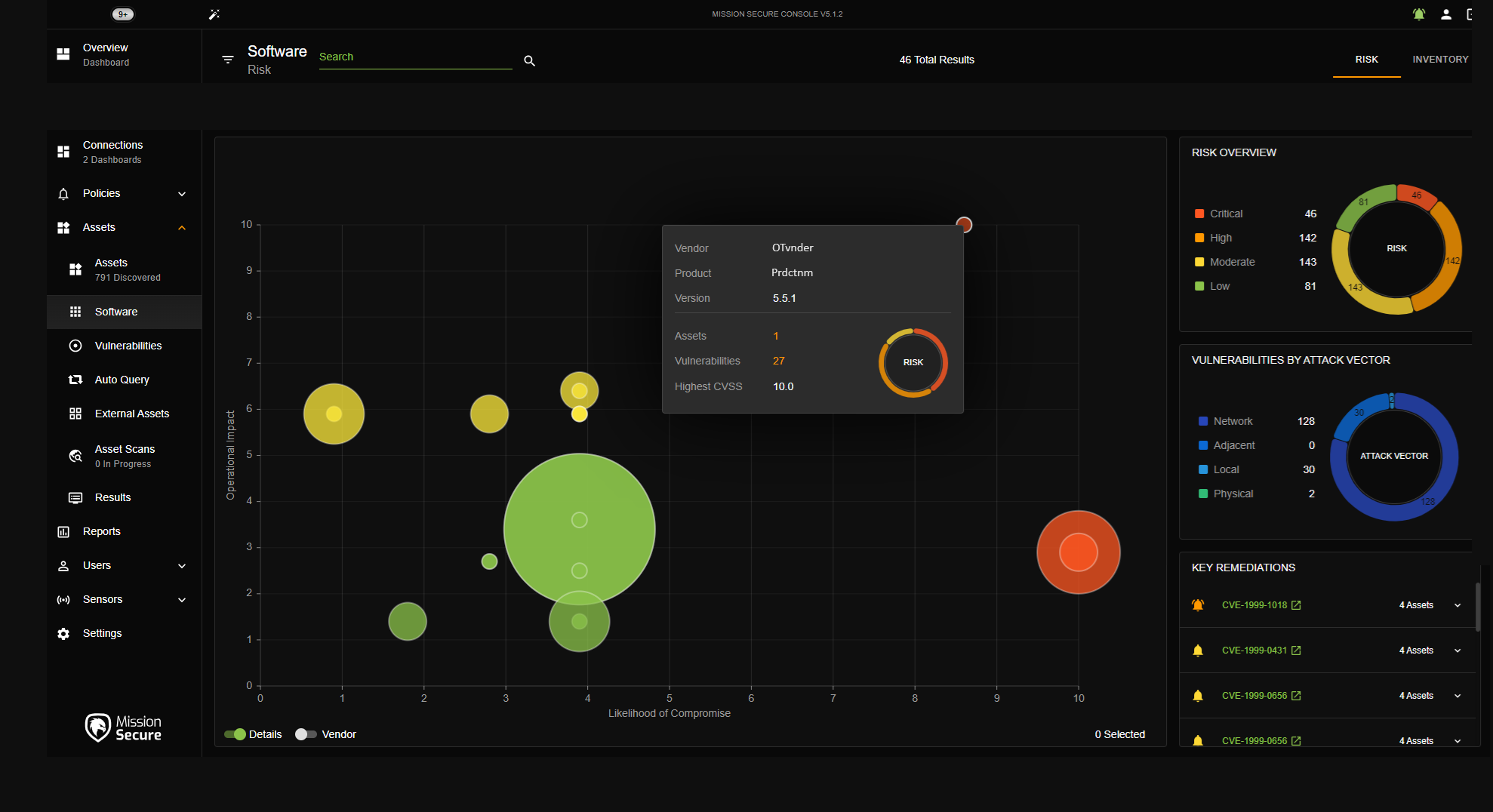
Review details and mitigations
Is a vulnerability on the list of Known Exploited Vulnerabilities? Are specific patches or compensating controls recommended by the asset OEM? Mission Secure provides the context you need in order to take meaningful action on the vulnerabilities that matter.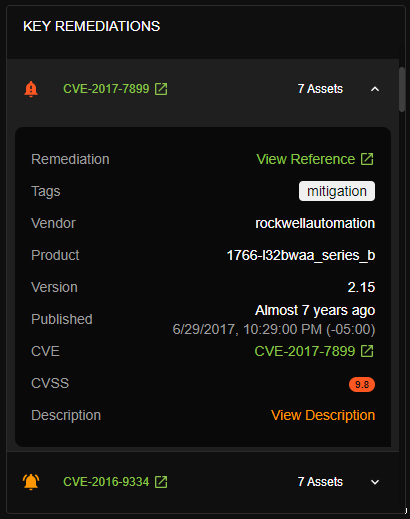
OT Vulnerability Bulletin
Sign up to receive Mission Secure's OT Vulnerability Bulletin for timely updates on new CVEs or KEVs that affect OT and ICS assets
Resources
-
Case Study
OT Cybersecurity Leads to Insurance Premium Savings
Read More » -
Blog
Zero Trust for Operational Technology: 6 Key Considerations
Read More » -
Datasheet
Mission Secure Platform
Read More » -
Blog
Your Vessel Exposed: 10 Potential Surprises to Expect from Your Maritime Cyber Risk Management Assessment
Read More »
Ready to learn more?
Our OT cybersecurity experts are standing by to discuss your organization's security goals and how Mission Secure can help you achieve them.