NERC CIP Compliance
Simplify NERC CIP compliance and reporting, and implement effective Zero Trust security in your OT network
Securing the power grid against advanced cyber threats
The power industry plays an essential role in modern society, providing electricity to homes, businesses, and critical infrastructure. In recent years, cyber attacks against the bulk electrical system (BES) have become more frequent, and their impact has grown more severe. The North American Electric Reliability Corporation (NERC) has established a set of critical infrastructure protection (CIP) standards to ensure the secure and reliable operation of the power grid.
Mission Secure's industry-leading OT cybersecurity platform delivers a wide range of capabilities that power industry organizations can use to meet (and exceed) their NERC CIP compliance obligations.
-
Identify and monitor OT assets
Detect and identify every asset connected to your OT network, and get real-time alerts on the changes that matter to you. -
Segment your network and control access
Prevent unauthorized connections, control lateral movement, and implement policies to protect critical assets. -
Demonstrate and maintain compliance
Mission Secure's OT security experts will help you develop a compliance roadmap and implement a solution tailored to meet your goals.
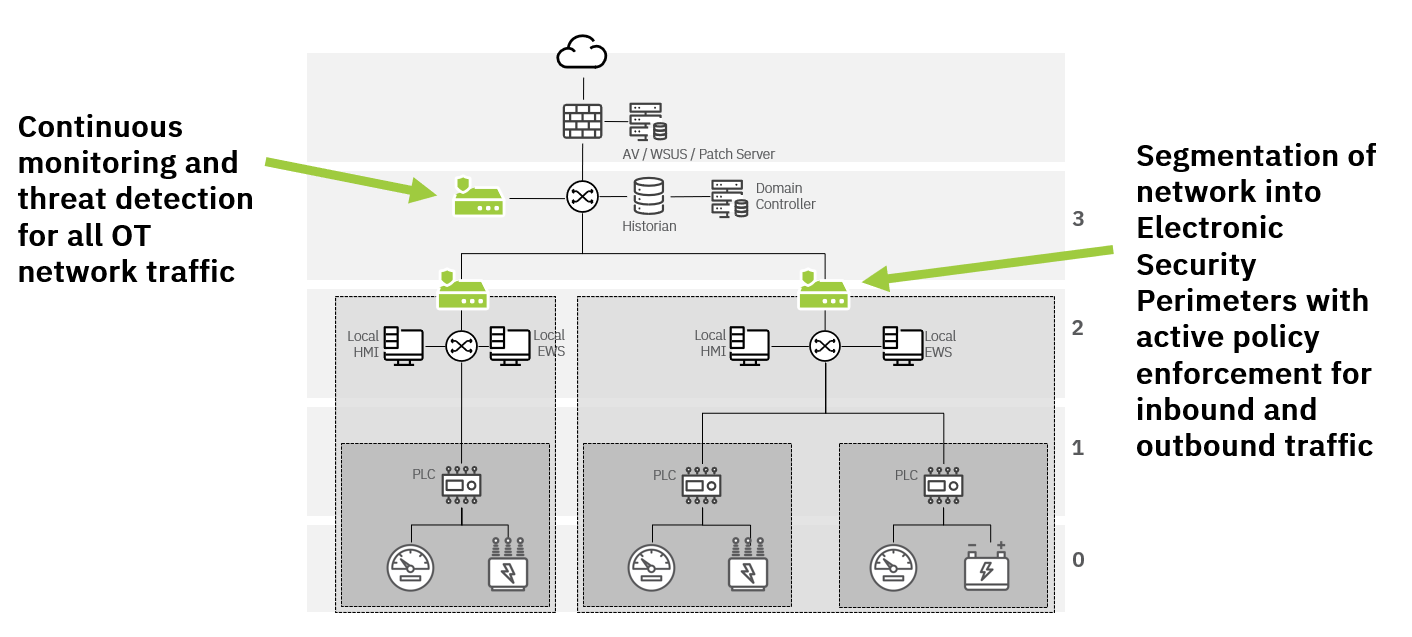
Meet NERC CIP requirements with Mission Secure
NERC CIP standards establish a set of requirements for power companies to ensure the reliability and security of the power grid. Compliance with these standards is essential for power companies to maintain their licenses and permits to operate. Non-compliance with NERC CIP standards could lead to significant penalties and fines, as well as damage to the company's reputation.
Solutions designed to meet NERC CIP standards
Mission Secure has worked with power industry customers and partners to develop capabilities that simplify NERC CIP compliance while strengthening the cybersecurity posture of power generation, transmission, and distribution systems. The table below gives a high-level overview of how Mission Secure's OT cybersecurity platform can help address a wide range of NERC CIP requirements.
For a detailed look at how we can help you meet your organization's unique needs and goals, contact us to schedule a consultation today.
CIP-002: BES Cyber System Categorization |
R1: Identification and categorization of BES Cyber Systems and assets
R2: Identification of additions or changes to asset inventories and categorization
|
CIP-005: Electronic Security Perimeter(s) |
R1: Electronic security perimeters
|
CIP-007: System Security Management
|
R1: Ports and services
R2: Security event monitoring
|
CIP-010: Configuration Change Management and Vulnerability Assessments |
R1: Configuration change mangement
R2: Configuration monitoring
R3: Vulnerability assessments
|
Wondering where to start?
OT cybersecurity can be a lot to take on, especially for organizations without dedicated OT security resources.
An OT cybersecurity assessment is the ideal starting point to determine where you are today and what you should prioritize as you develop your strategy. Mission Secure offers a variety of assessment options to help you identify your OT security challenges and opportunities.

Take the first step today!
To learn more about NERC CIP compliance and our other solutions for the power industry, contact us today. Our OT and ICS cybersecurity experts will be in touch right away.
As a company, we remain steadfastly focused on the use of technology to ensure operations remain safe and environmentally compliant, and that includes the cyber security of our operational control systems. Our work with Mission Secure is part of an on-going effort to maintain operational safety and resilience, including the reduction of cyber security risks.
EVP of Operations, Mission Secure customer
Resources
-
Case Study
OT Cybersecurity Leads to Insurance Premium Savings
Read More » -
Guide
A Comprehensive Guide to Operational Technology (OT) Cybersecurity
Read More » -
Podcast
Evercore ISI Podcast | Mission control in Energy, Oilfield Services, Equipment & Drilling
Read More »