Segmentation and Policy Enforcement
Implement effective Zero Trust security architectures with Mission Secure's industry-first OT policy enforcement capabilities.
Take complete control over your OT environment from signal to cloud
-
OT Network Segmentation
Implement OT network segmentation and microsegmentation with easy-to-configure network zones. -
Active Policy Enforcement
Create tailored policies to define allowable connections and conditions for each network segment or location.
-
Fine-Grained Controls
Control network activity based on dozens of variables, including user profiles, asset configuration, and real-time conditions.
Game-changing capabilities for OT security
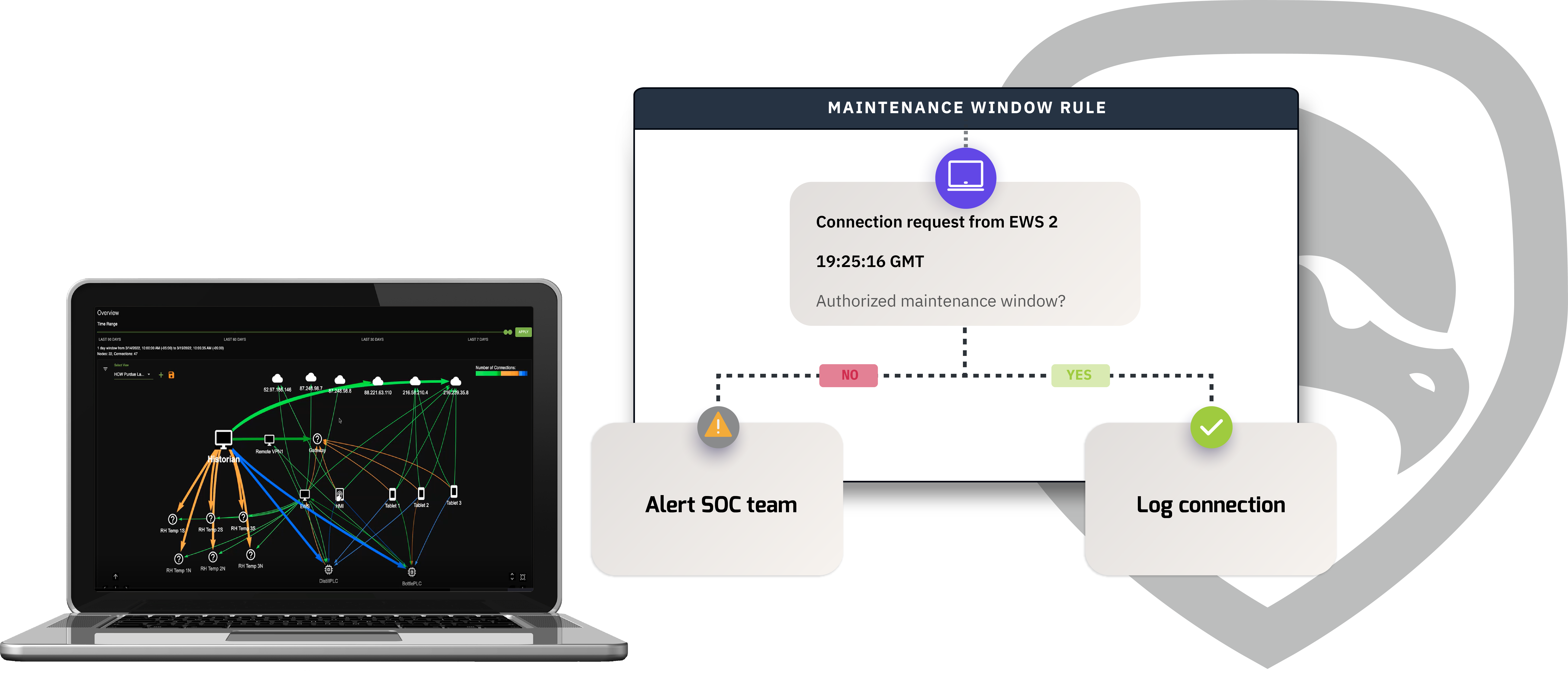
At the core of the Mission Secure platform is a fine-grained policy engine that enables highly sophisticated, OT-specific workflows, allowing organizations to take unprecedented control over their OT environments. With Mission Secure, it becomes possible to move beyond passive visibility and alerting into true Zero Trust security, with active controls based on a continuously updated picture of the OT network.
Segment Your Environment Without Rearchitecting the Network
Segmentation is often the first step in OT policy enforcement. Deploy Mission Secure’s platform as an overlay to your existing OT network, and minimize the damage from a potential attack by implementing network segments to limit east-west and north-south activity.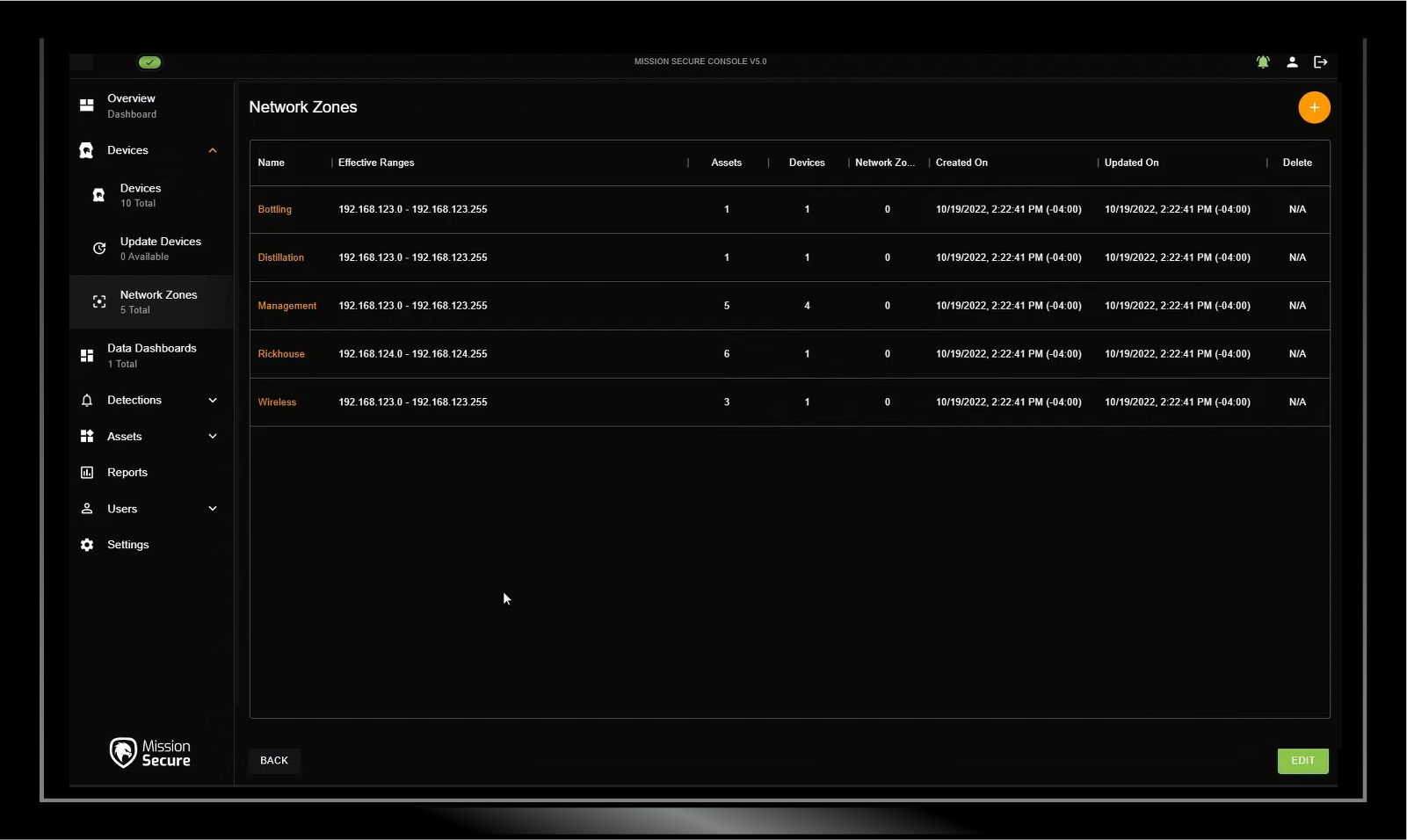
Limit Activity to "Known Good" Assets and Connections
Create and enforce rules to stop threats before they have a chance to cause damage. Define the conditions that must be met before devices are allowed to connect, and create guardrails to ensure network traffic fits what your organization expects and allows.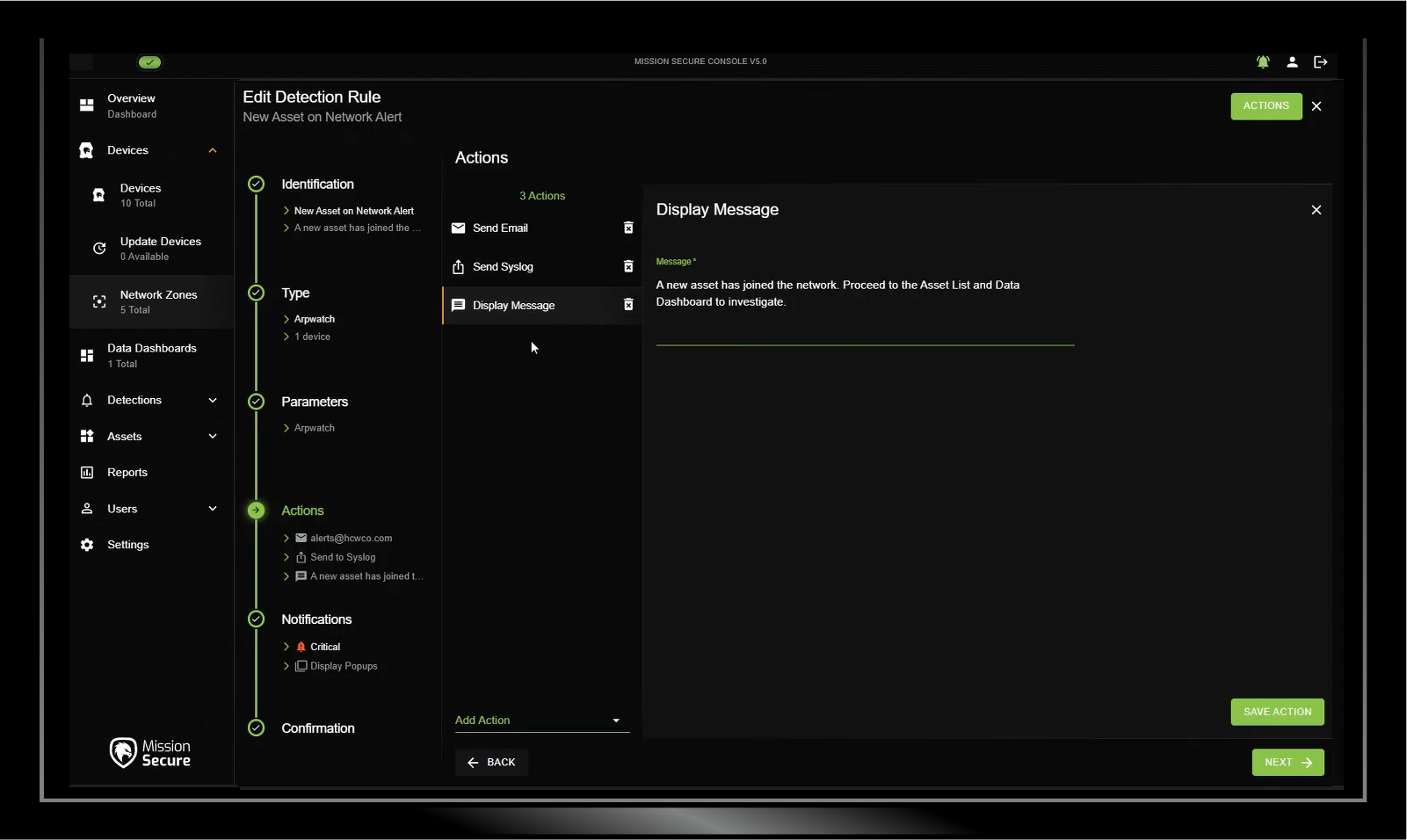
Create Rules Based on the Variables that Matter to You
Mission Secure puts the power in your hands by letting you create OT network rules based on the attributes and conditions that matter in your environment. Define policies based on asset firmware, patch status, vulnerability scores, protocols in use, user roles, or time of day, just to name a few.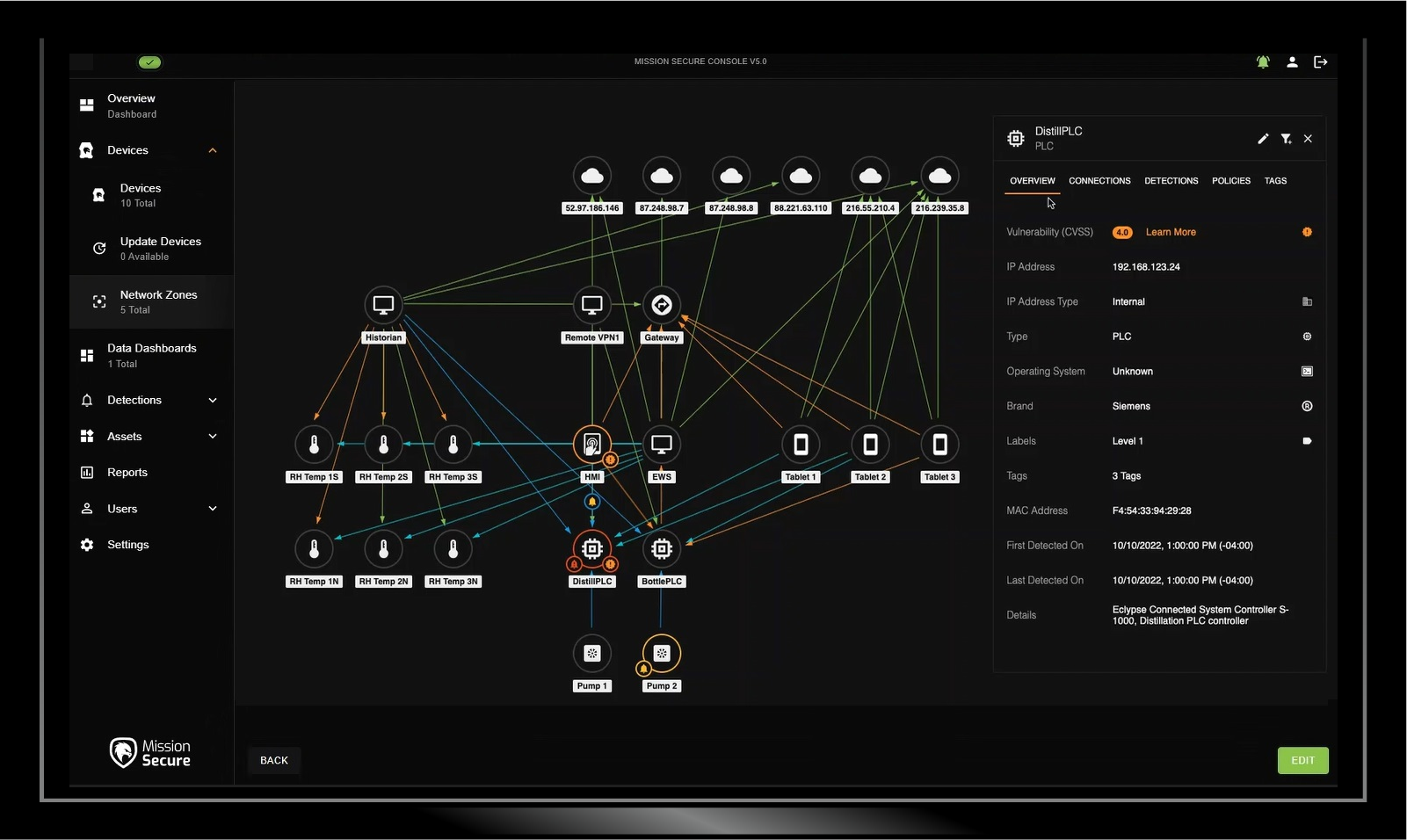
Learn more about the Mission Secure platform
Asset and network visibility is only the beginning of what Mission Secure's OT Native Zero Trust cybersecurity platform can do. Explore our advanced capabilities including threat and anomaly detection, network segmentation and policy enforcement, and Level 0 signal integrity validation.
Resources
-
Case Study
OT Cybersecurity Leads to Insurance Premium Savings
Read More » -
Blog
Your Vessel Exposed: 10 Potential Surprises to Expect from Your Maritime Cyber Risk Management Assessment
Read More » -
Datasheet
Mission Secure Platform
Read More » -
Blog
Zero Trust for Operational Technology: 6 Key Considerations
Read More »
Ready to learn more?
Our OT cybersecurity experts are standing by to discuss your organization's security goals and how Mission Secure can help you achieve them.