Visibility and Control from Signal to Cloud
Mission Secure delivers the only OT cybersecurity platform that enables complete control over your environment, including visibility, anomaly and threat detection, policy enforcement, and Level 0 signal validation.
OT Native Cybersecurity: Visibility, Monitoring, and Enforcement
For the first time, OT organizations can implement true Zero Trust security strategies, with fine-grained cybersecurity policy monitoring and enforcement, including the ability to allow or block connections to cyber-physical systems based on conditions such as asset vulnerability score, patch status, user profile, or time of day.
Mission Secure: 3-Minute Demo
Mission Secure's OT cybersecurity platform delivers industry-leading asset inventory, vulnerability management, and anomaly detection capabilities. Check out this short video for glimpse of what Mission Secure has to offer.
For a full demonstration of the Mission Secure platform and to learn more about how we can help you identify and mitigate OT cyber risk, contact us today!
-
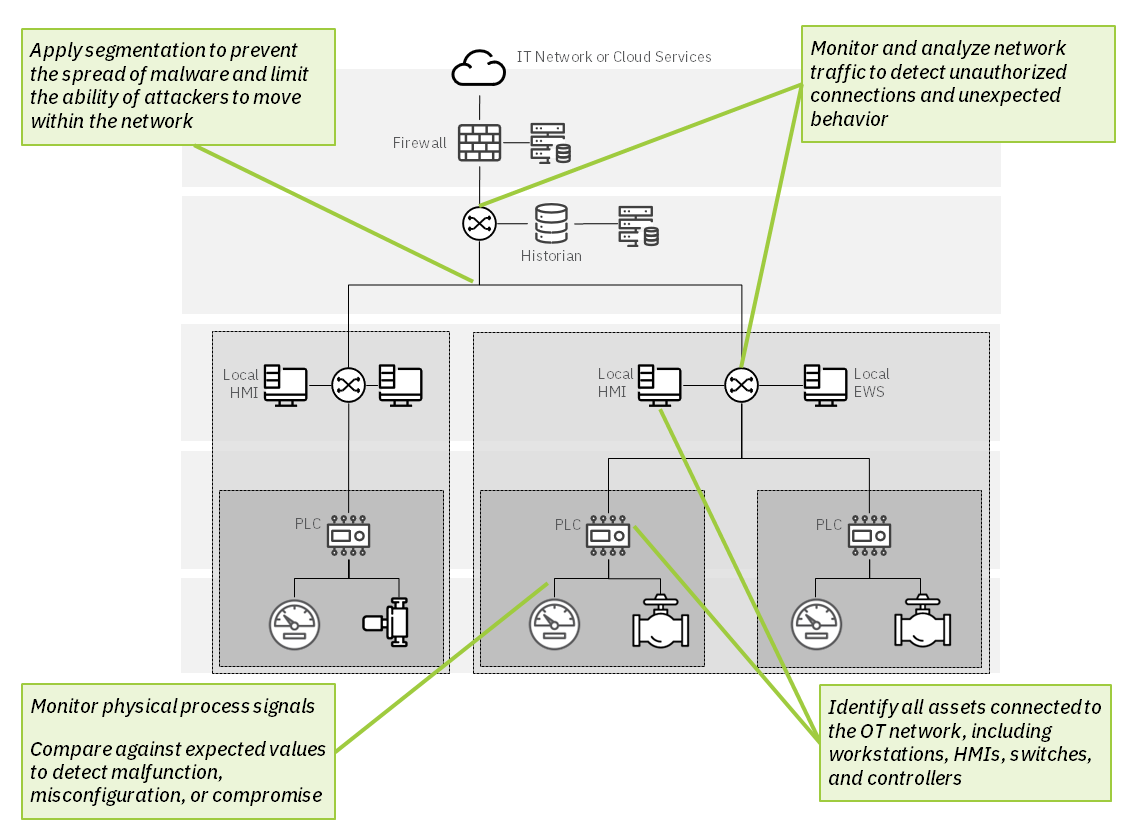
Asset and Network Visibility
Discover and visualize every asset and every network connection in your OT environment -
Anomaly and Threat Detection
Identify unexpected or unauthorized activity, from Level 0 signals to cloud connections -
Policy Enforcement
Segment your network and enforce granular policies for true Zero Trust cybersecurity -
Signal Integrity Validation
Monitor physical process signals to detect threats and prevent system damage
Asset and Traffic Visibility
OT cybersecurity begins with visibility. Before you can effectively segment your network, detect unauthorized activity, or enforce access policies, you need to understand which assets are connected to your network and how they’re communicating. Mission Secure provides advanced asset discovery, network discovery, and network visualization tools to give you the insights you need.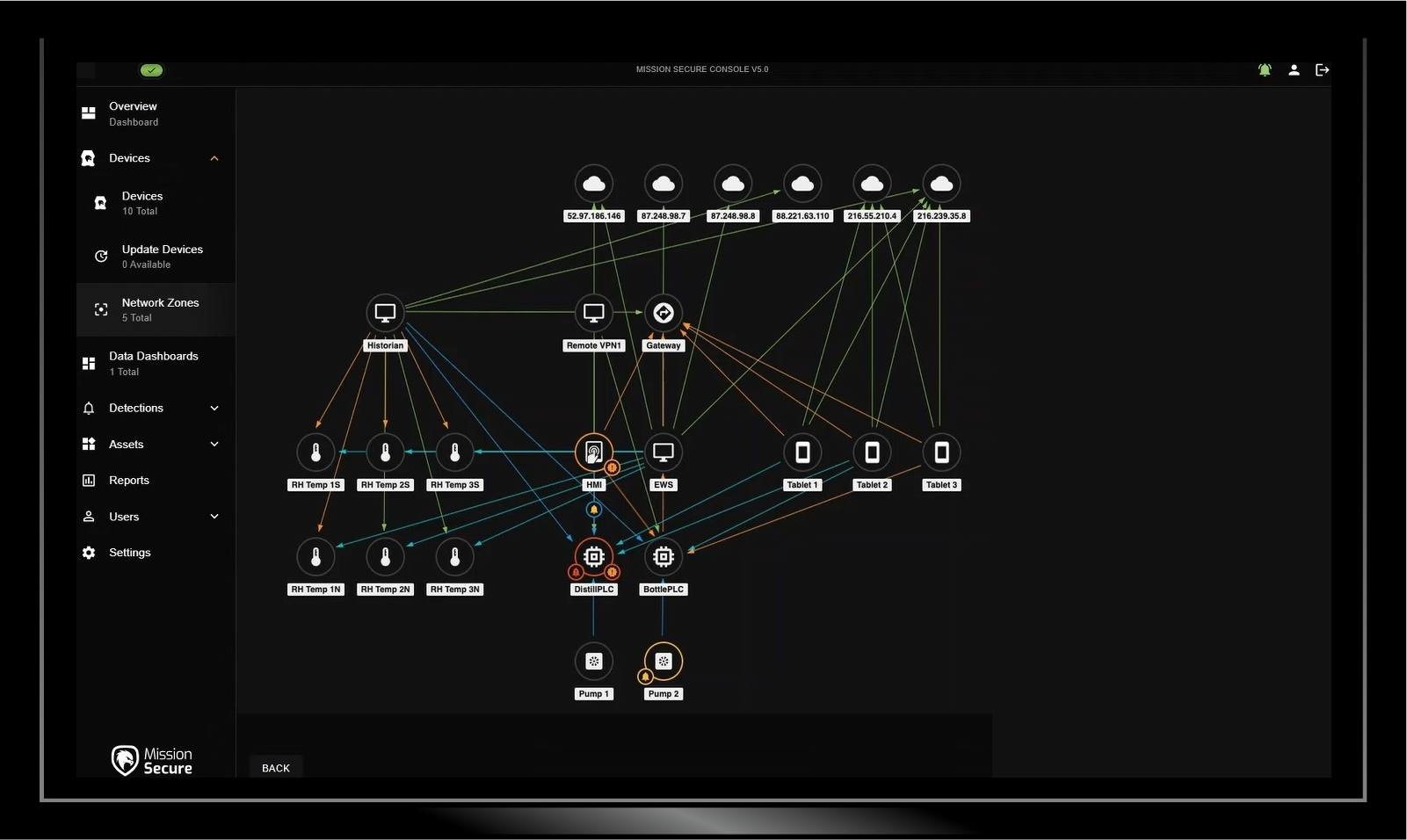
Anomaly and Threat Detection
Trouble in the OT network can show itself in many forms. Connections between devices that have never communicated before, the use of an unexpected protocol, an increase in traffic to or from a device, or a change in a Level 0 process variable can all indicate the presence of a system fault or a cyber attack. Mission Secure’s OT-native anomaly and threat detection capabilities can give you a head start on isolating and remediating potential problems.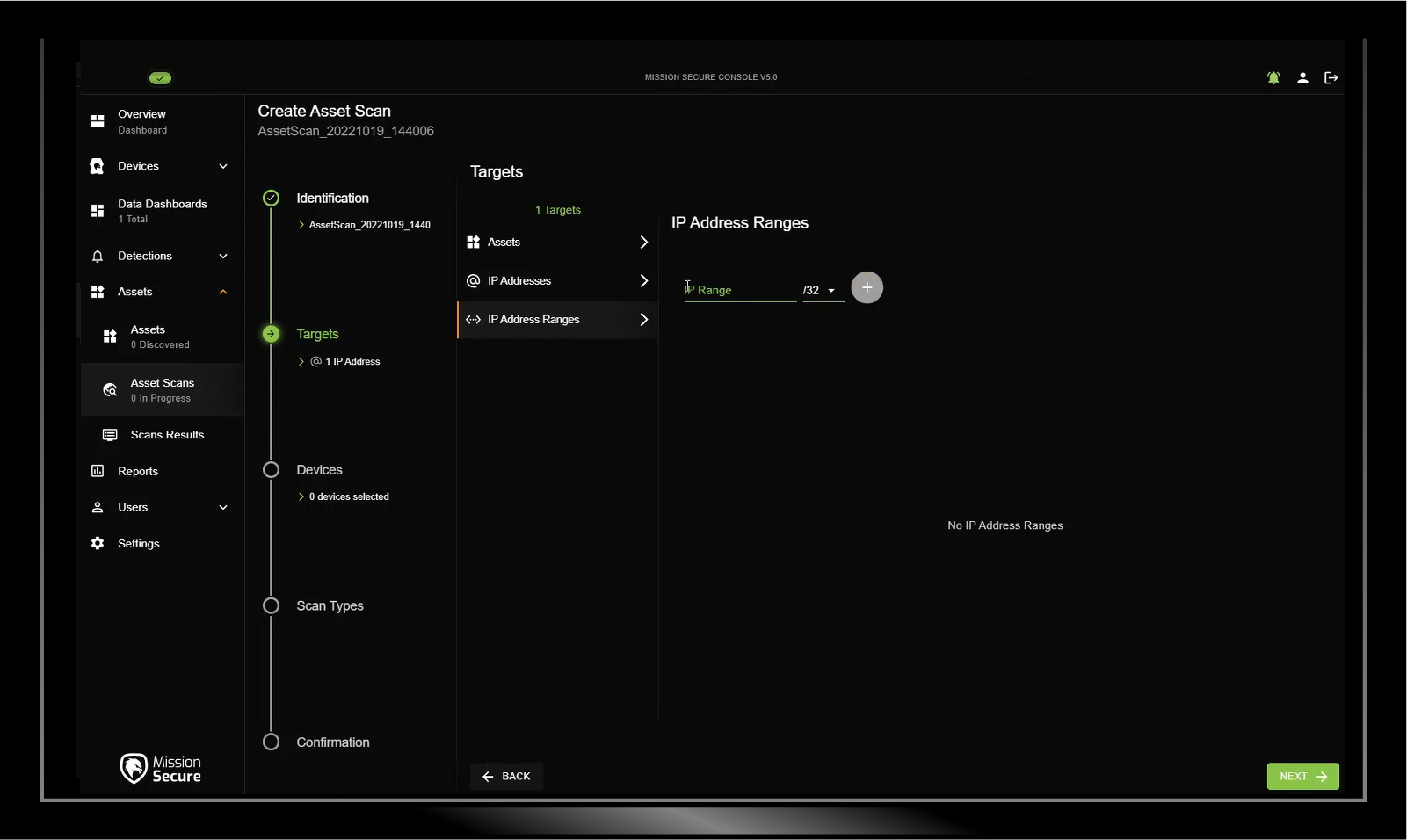
Segmentation and Policy Enforcement
Dozens of variables factor in to the level of risk facing your OT assets. Mission Secure provides a detailed, organized view of each asset's security posture, including key indicators such as firmware versions, patch status, CVSS scoring, inbound and outbound connections, and applicable policies.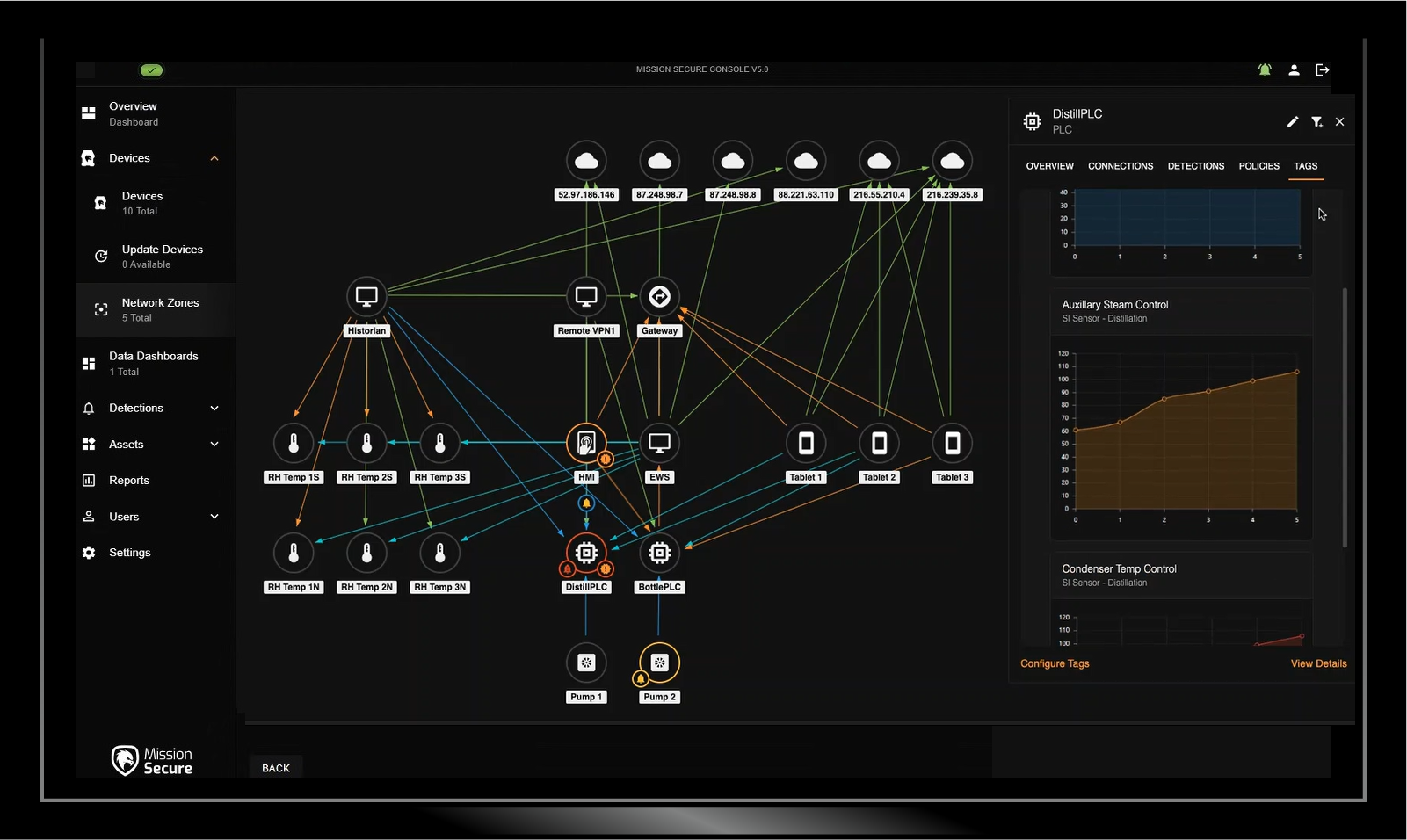
Signal Integrity Validation
The most valuable assets in your OT environment are the devices that do work in the physical world–sensors, actuators, and the other devices that create value for your organization. These are also prime targets for threat actors, and are often the most difficult assets to secure. Mission Secure’s Level 0 signal integrity validation technology monitors the analog or digital signals generated by your cyber-physical assets to detect signs of signal spoofing or other low-level attacks.
Built to address the unique needs of OT and ICS environments, Mission Secure's technology and managed services protect critical assets from human error, insider threats, and external attacks.
Resources
-
Case Study
OT Cybersecurity Leads to Insurance Premium Savings
Read More » -
Blog
Zero Trust for Operational Technology: 6 Key Considerations
Read More » -
Datasheet
Mission Secure Platform
Read More » -
Blog
PIPEDREAM Malware: Understanding and Mitigating the Threat
Read More »
Ready to learn more?
Our OT cybersecurity experts are standing by to discuss your organization's security goals and how Mission Secure can help you achieve them.