4 Min Read
Maritime Security Challenges: The Physical Impact of Maritime Cyber Threats
Written by Mission Secure

An attack on an OT network (or maritime vessel network) can have disastrous consequences and lead to injury, loss of life, asset damage or environmental impact.
When we see a dangerous security vulnerability or debilitating cyberattack appear in the (almost) daily headlines, the story is usually the same: a hacker compromises an enterprise network and steals personnel data, credit card numbers, product roadmaps, confidential emails and more. And just for fun (and money), a hacker will hold the data for a sizeable ransom and threaten to publish the information if the payment isn’t received.
But there is a whole other world of cyberattacks, where hackers target operational technology (OT) environments that support infrastructures in manufacturing, transportation, defense, utilities and others.
Read more in our Comprehensive Guide to Maritime Cybersecurity.
An attack on an OT network (or maritime vessel network) can have disastrous consequences and lead to injury, loss of life, asset damage or environmental impact.
In this post, we’ll dive into how a hacker can attempt to compromise the on-vessel OT network, look at a couple of real-world examples and help you eliminate the physical impact of cyber threats in your maritime environment.
Let’s Get Physical: A Hacker’s Approach
The allure of hacking industrial systems and programmable logic controllers (PLCs) on maritime vessels stems from their lack of built-in security. Also, maritime vessel networks have historically been flat and isolated, with air-gapping as the “security solution” of choice. Because of this, security had not been top of mind. But as these networks become more connected, the attack surface on a vessel increases. With inadequate or no segmentation at all between the IT and vessel networks, the threat of malware making its way into the vessel networks and spreading laterally toward critical controls is real.
As maritime organizations review and adjust their security architectures, one of the recommended frameworks for them to adopt is the Purdue model.
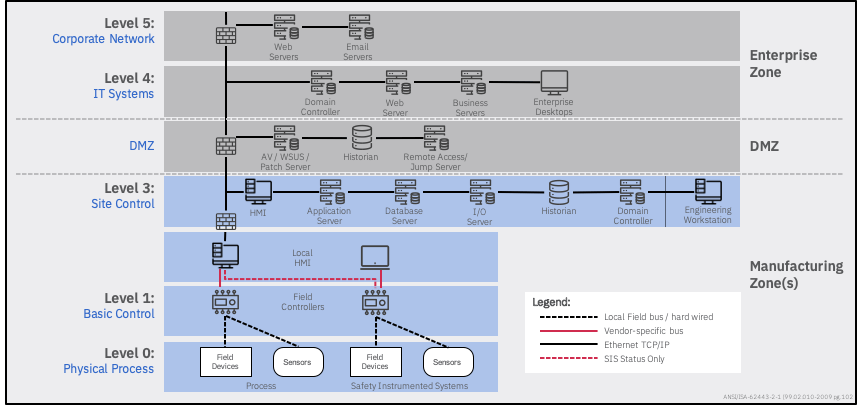
Figure 1: Purdue Enterprise Reference Architecture
If we look at a typical attack sequence, a hacker will probably attempt to infiltrate the vessel’s OT network through various methods. They will look for vulnerable entry points through satellite communications terminals, open or unprotected Wi-Fi networks, endpoints in the IT/corporate network and maritime-specific systems. Some common attack vectors include spear phishing, compromised or misconfigured endpoints, and stolen credentials. If the hacker is onboard, they can infiltrate systems directly with infected USB thumb drives.
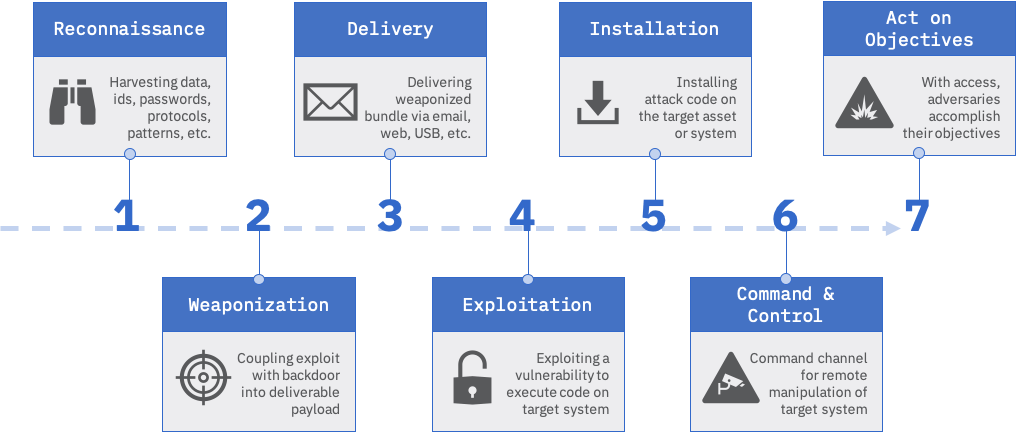
Figure 2: Hacker Attack Sequence
Once they get in, they’ll hide through various obfuscation methods and eventually assume control of critical control systems and devices. The hacker can now compromise things like navigation and communications systems, open or close critical valves, and take over propulsion and rudder controls – and the consequences can be disastrous.
Maritime Security Incidents: Physical Cyber Threats in the Real-World
There have been a growing number of cyberthreats targeting OT networks, but more often than not, those incidents are not reported. According to the SANS 2019 State of OT/ICS Cybersecurity Survey, despite the growing demand to publicly acknowledge incidents, 43% of respondents admit being restricted by internal policy from sharing such information outside of official organizational channels, as opposed to 25% in 2017. In fact, the United States Coast Guard’s 2018 warning on the Emotet malware came after a merchant vessel was infected with it due to an almost total lack of cybersecurity safeguards. The ship was not named to encourage others to report cybersecurity incidents. And since the Coast Guard’s 2018 warning, there have been additional warnings issued, and they have shared cybersecurity best practices for commercial vessels.
On July 5, 2020, X-FAB Group, a leading analog/mixed-signal and micro-electro-mechanical systems foundry group manufacturing silicon wafers for automotive, industrial, consumer, medical and other applications, became the latest victim of Maze ransomware. The attack resulted in a total shutdown of X-FAB Group’s IT systems and production at all six manufacturing sites, as well as the postponement of the company’s publication of second-quarter results. Also, the group behind the attack has publicly released some of the data stolen from the company in the form of zip files. As of July 13, 2020, production has resumed at one of X-FAB Group’s manufacturing sites, with the others back in production as of August 27, 2020.
In 2015, a steel mill in Germany was struck by hackers in what was, at the time, only the second confirmed case of a cyberattack causing physical damage (Stuxnet being the first). Hackers gained access to the steel mill through the enterprise network via a spear-phishing attack and were then able to work their way into production networks to access systems that controlled plant equipment. Showing expertise in their knowledge of industrial control systems, the hackers were able to compromise individual control components and even entire systems. The plant was unable to shut down a blast furnace, resulting in massive damage to the system.
In the maritime cybersecurity world, Danish shipping giant Maersk (A.P. Møller-Maersk) fell victim to NotPetya in June 2017. While Maersk lost most of its data, applications, over 49,000 laptops and almost half of their servers, the computers on their actual ships were spared. However, the terminals’ software designed to receive the Electronic Data Interchange files from those ships had been wiped entirely.
Where ships’ systems were affected occurred in June 2017, when a GPS spoofing attack involving over 20 ships in the Black Sea made them “disappear.” Instead of showing actual positions, ships were being shown 25 to 30 miles away at Gelendzhik airport. When one ship operator radioed the other vessels, it was confirmed that there was an issue with everyone’s GPS. GPS spoofing can deliver potentially catastrophic consequences: ships could be directed off course and criminals could take advantage to steal precious cargo.
Maritime Security Today: How Can You Eliminate the Physical Impact of Maritime Cyberthreats?
Before you can eliminate the physical impact of maritime cyberthreats, you need to have a baseline understanding of what is in your IT/OT network environment so that you can classify and manage them appropriately. Then you can analyze communication flows, identify any security gaps and take the appropriate actions to:
Protect: Restrict unauthorized access and block abnormal or malicious activity from reaching important controllers and Level 1 devices.
Monitor: Continuously monitor network IP levels, alongside digital and analog signals with a secure, multi-layered system.
Detect: Conduct analysis in real-time with automated incident detection.
Inform: Keep trusted operators and cybersecurity professionals informed through dedicated communications systems.
Collect: Gather system data from digital and analog sensors, actuators, controllers, and the OT network for forensic purposes.
Correct: Execute automated or operator-guided responses, system restorations, and reset functions to safe operating states.
Originally published July 31, 2020, updated December 14, 2020.