5 Min Read
IMO 2021: Three Steps to Ensure IMO/ISM Cybersecurity Compliance
Written by Mission Secure

IMO Guidelines on Maritime Cyber Risk Management
New Year’s Day 2021 will not just be the start of a new year – it will also be a date of significance for those in the maritime industry. The International Maritime Organization (IMO) will be enforcing Resolution MSC. 428(98) that “encourages administrations to ensure that cyber risks are appropriately addressed in existing safety management systems (as defined in the International Safety Management (ISM) Code) no later than the first annual verification of the company’s Document of Compliance (DOC) after January 1, 2021.”
Maritime organizations now need to follow the guidance and recommendations outlined by the IMO to ensure their vessel operations are protected from potentially catastrophic cyberattacks.
Maritime cybersecurity is no longer on the back-burner. Vessel systems are more connected than ever, and despite a global pandemic, hackers have ramped up their efforts to compromise critical vessel OT systems. Maritime organizations now need to follow the guidance and recommendations outlined by the IMO to ensure their vessel operations are protected from potentially catastrophic cyberattacks.
Learn about current threats to maritime security and effective cyber risk management in our Comprehensive Guide to Maritime Cybersecurity.
In this post, we’ll walk you through the three recommended steps to ensure IMO cybersecurity compliance to get you ahead of the upcoming January 2021 deadline.
Why is IMO Cybersecurity Compliance Important?
With sophisticated cyber threats now taking full aim at the maritime industry, there must be protections in place to safeguard the carriage of 90% of world trade. There is an immediate need for companies to not only develop and implement a safety management system (SMS) for vessels within their fleet but also to do it uniformly to reduce inconsistencies across the entire industry.
The IMO Resolution is designed to standardize and document processes that will reduce the number of cybersecurity incidents on vessels and addresses people, process and technology from a cybersecurity perspective within the safety management system. Within the IMO Resolution is MSC-FAL.1/Circ.3, which provides recommendatory guidelines on maritime cyber risk management. It includes information on additional guidance and standards that those in the maritime industry should take into consideration in addition to any other international and industry standards and best practices. Among the recommended standards is ISO/IEC 27001, a technology-neutral, vendor-neutral information security management standard that offers a prescription of the features of an effective information security management system (ISMS).
Another standard recommended is The Guidelines on Cyber Security Onboard Ships, which is supported by BIMCO, CLIA, the International Chamber of Shipping (ICS), INTERCARGO, INTERMANAGER, INTERTANKO, the International Union of Marine Insurance (IUMI), OCIMF and the World Shipping Council. This extensive document offers guidance to shipowners and operators on procedures and actions to maintain the security of cyber systems in their organization and onboard their vessels and also includes direction based on another IMO-recommended standard: National Institute of Standards and Technology (NIST) Cybersecurity Framework.
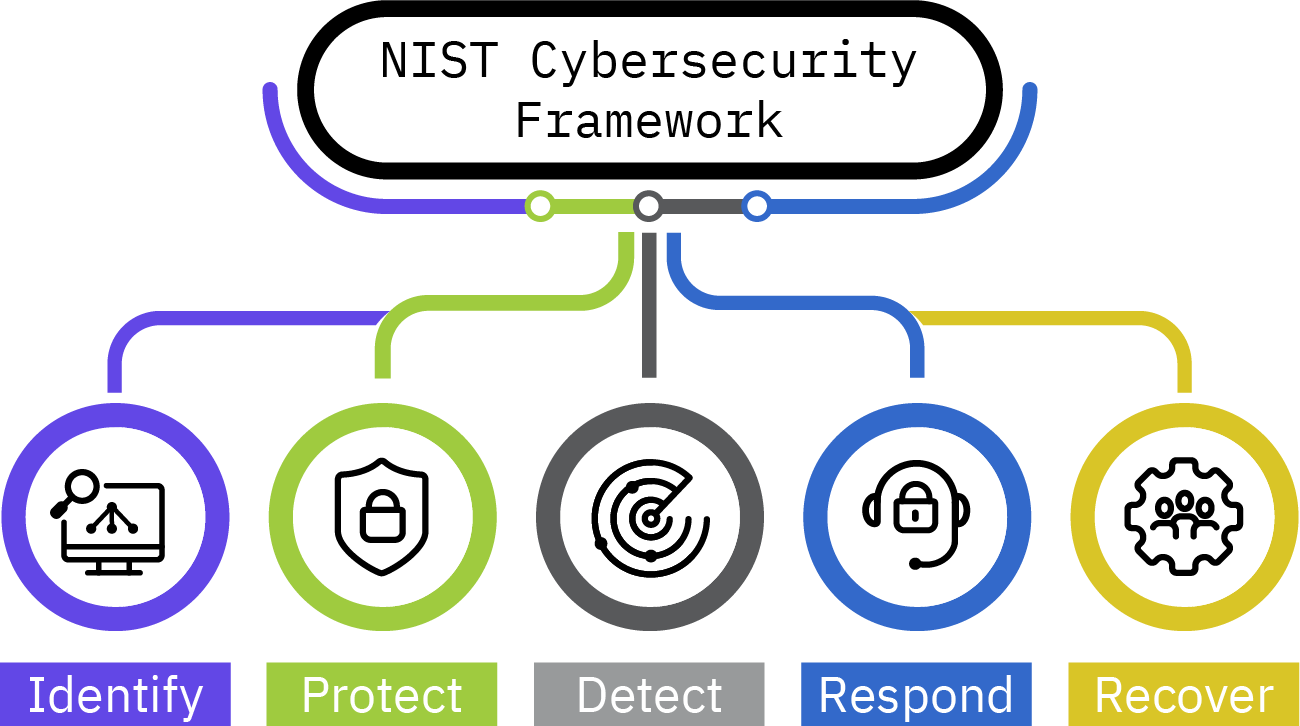
The NIST Cybersecurity Framework is a living document based on international standards and guided by academia and the public and private sectors. It applies to any type of risk management, defines the entire breadth of cybersecurity and includes the functional elements that support effective cyber risk management:
Identify: Define personnel roles and responsibilities for cyber risk management and identify the systems, assets, data and capabilities that, when disrupted, pose risks to ship operations.
Protect: Implement risk control processes and measures, and contingency planning to protect against a cyber-event and ensure continuity of shipping operations.
Detect: Develop and implement activities necessary to detect a cyber-event in a timely manner.
Respond: Develop and implement activities and plans to provide resilience and restore systems essential for shipping operations or services impaired due to a cyber event.
Recover: Identify measures to backup and restore cyber systems necessary for shipping operations impacted by a cyber-event.
As we walk through the three steps to ensure IMO Cybersecurity Compliance, keep in mind that they cover people, process and technology across the functional elements of the NIST Cybersecurity Framework:
Ensure IMO Cybersecurity Compliance with These Three Recommended Steps
These three recommended steps represent an overall approach that will help you address maritime cybersecurity and comply with the IMO Resolution and ISM Code. Before you can begin your approach to complying with IMO’s compliance requirements, you need to evaluate the cyber risks in your vessel OT environment. And to have a clear understanding of your entire maritime environment, you need comprehensive visibility so that you can make real-time, continuous assessments of your environment.
1. Assess Maritime Cybersecurity Risks
Your vessel IT and OT network consists of many interconnected systems, and all of them can be vulnerable to cyberattacks, including: propulsion and machinery management and power control systems; communication systems; bridge systems; access control systems; cargo handling and management systems; public-facing networks; passenger servicing and management systems; and administrative and crew welfare systems. Information and data are exchanged within these systems and they must be evaluated for any cyber risks as any sudden failure due to a cyberattack can result in potentially catastrophic conditions.
It would be best if you also looked at your vessel’s processes to ensure they are sound against cyber threats from benign, malicious, intentional, unintentional, current or emerging sources. You need to evaluate design, operation, integration or maintenance inadequacies that can potentially impact safety and cybersecurity and review any potential inappropriate or procedural lapses by the crew or any third parties that need to interact with vessel systems.
And last but not least, you need to include your people as part of your cybersecurity risk assessment. Cybersecurity awareness and the training of your crew is crucial to the cybersecurity of your vessels. You need to ensure that your people maintain a level of cyber discipline and hygiene so that there are no lapses in your cybersecurity risk management.
And speaking of cybersecurity risk management, once you have a proper assessment of any potential maritime cybersecurity risks across your people, processes and technologies, you need to incorporate your cybersecurity policy across all levels of your maritime organization, onboard and ashore, and develop a continuous process of reviews, inspections, internal cybersecurity audits and feedback mechanisms.
Don’t know where to start? Check out our comprehensive IMO Readiness Review.
Our experts will remotely walk through a detailed compliance questionnaire with your team, give you an IMO Readiness Score, and let you know how you stack up relative to the IMO requirements and other maritime organizations. Click here to request a free IMO Readiness Review with Mission Secure.
2. Design a Secure Maritime Cyber Architecture
Per the guidelines in the ISM Code and IMO Guide, maritime organizations are encouraged to design, establish or incorporate cyber risk management into their safety management system. Organizations in the maritime industry will have different needs and levels of maturity when it comes to the breadth of their vessel OT networks and cyber-related systems, so approaches to securing their maritime cyber architectures will vary.
There are a couple of ways that maritime organizations can design a secure maritime cyber architecture.
One approach that is accepted by the IMO is to compare a current comprehensive cyber risk assessment to an organization’s desired cyber risk management posture. Any identified gaps can be addressed to achieve risk management objectives and can enable you to apply your resources most effectively.
Or you can develop your cybersecurity policy or cyber risk management approach encompassing the elements of the NIST Cybersecurity Framework that will help you ensure the cybersecurity practices in your vessel’s operations and environment. Your policy should incorporate a comprehensive assessment of all identified cyber risks as they relate to your ships, personnel and environment, as well as continuous improvement of cyber risk management.
The IMO also suggests updates to your safety management system (SMS) to account for your maritime cyber risk management framework and the inclusion of cyber risk documentation that details critical assets that can adversely affect ship operations if compromised; roles and responsibilities for crucial cybersecurity personnel; how objectives will be met; procedures for corrective actions and recurrence prevention; incident response plans; creation and maintenance of backups; and procedures for cyber non-conformity, accidents or incident reporting.
3. Protect Vessels and Maritime Operations
Ultimately, the goal of the IMO Resolution is to protect vessels and maritime operations. The functional elements of the NIST Cybersecurity Framework need to be a consistent part of your maritime cybersecurity policy so that you can execute the following:
Identify:
• Critical cyber systems through asset discovery and inventory tracking
• Network traffic flows across IT and OT vessel networks
Protect:
• Critical devices through network segmentation, continuous monitoring and validation
• Network traffic against unauthorized or unknown traffic
• Network access through green-lighting, blocking or restricting rights
• Assets and systems with robust encryption mechanisms
Detect:
• Critical devices, assets or data through real-time monitoring
• Unauthorized or unknown network traffic and/or devices
• Abnormal events
• Data validation using analog and digital signals
• Potential cyberattacks with real-time notifications or alerts
Respond and Recover:
• Critical devices, assets or data through real-time monitoring
• Real-time notifications or alerts to key personnel
• Automated and/or operator-guided corrective actions
Navigate Your Way to IMO Cybersecurity Compliance
Now is the time to review your operations and management of your vessels to ensure their security, safety and reliability from the onslaught of emerging cyberattacks. With a thorough and effective cybersecurity risk management approach, you’ll be able to ensure that you have the resources needed to protect your onshore and offshore operations. And with real-time visualization of your data and protection of critical assets and continuous monitoring across your vessels and maritime operations, you will be on your way to achieving IMO cybersecurity compliance.
Originally published August 17, 2020, updated April 28, 2021.