4 Min Read
Current Threats to Maritime Security: A Prime Target for Cyber Adversaries
Written by Mission Secure
“Cyber-attacks on the maritime industry’s operational technology (OT) systems have increased by 900% over the last three years, with the number of reported incidents set to reach record volumes by year end.”
- Marine Log
Recent reports highlight the exponential growth in OT cyber-attacks targeting the maritime industry, increasing a staggering 900% over the last three years. As Marine Log reports, “Cyber-attacks on the maritime industry’s operational technology (OT) systems have increased by 900% over the last three years, with the number of reported incidents set to reach record volumes by year end.” The Maritime Professional previously reported attacks have increased 400% since the COVID-19 outbreak.
Accounting for the carriage of 90% of world trade, maritime is one of the oldest industries and lifeblood of the global economy. Ships and other vessels may seem like unusual targets for cyberattacks. But, with the IT/OT convergence and growing use of satellite communications, hackers have a new playground that’s ripe for an attack—a fact these new cyber-attack statistics further illuminate.
Current threats to maritime security
“From a hacker’s perspective, maritime operations—onshore and at sea—remain highly vulnerable to cyber adversaries,” comments Weston Hecker, ethical hacker at Mission Secure. “Having tested vessels and onshore operations, there are many vulnerabilities and risks within maritime operations that make them attractive to adversaries across several fronts.” Hecker further dives into maritime cybersecurity from a hacker’s perspective in the upcoming podcast, Risk X.0, by the American Bureau of Shipping (ABS) Group.
Maritime security challenges: Operational technology (OT)
Despite the new headline-making stats, cyber risks for the maritime industry isn’t a new challenge. An industry survey published earlier this year found only 4 of 10 respondents said their organization protects vessels from OT cyber threats, with some even describing their organizations OT cyber risk policy as “careless.”
“Working to secure the maritime industry over the last few years, we’ve seen a high-degree of OT cyber risks and challenges first-hand,” states Don Ward, SVP of Global Services. “But more importantly, how do organizations start to secure their OT environments from cyber risks and threats? That needs to be the focus.”
Drawing from extensive experience in maritime OT cybersecurity, Ward recounts some of the most common cyber risks seen in the field, including a few real-world examples and recommended actions to secure vessels and operations.
Common vessel cybersecurity vulnerabilities
The maritime industry is uniquely complex. Liquified natural gas (LNG) tankers, for example, combine maritime, offshore, cryogenics, and more, with connectivity to onshore and third-party vendors, suppliers, and contractors. Common cybersecurity vulnerabilities seen in the field include:
• No clear understanding of all systems and devices on the OT network across a fleet or operation
• A lack of visibility into each vessel’s OT network
• No real-time monitoring of the OT network
• No segmentation of the OT network
• Inadvertently connected IT and OT networks
• 24/7 remote access for third parties
• End of life and unpatched operating systems on critical OT servers and workstations
Attacker ingress points: Unsecured VoIP Systems
One common cyber risk is attacker ingress points such as unsecured, unpatched, or unmanaged VoIP Systems and other communication devices. An exploitable VoIP phone, for example, can allow cyber adversaries to get access to the ship network, as shown in Figure 1.
In this situation, an attacker plugs into the ship via any open port. While the vessel’s network automatically moves the attacker to the guest network, the attacker gains unauthorized access to the network through an exploitable VoIP phone. From there, the attacker gains access to the IT network and, further, the ship network.
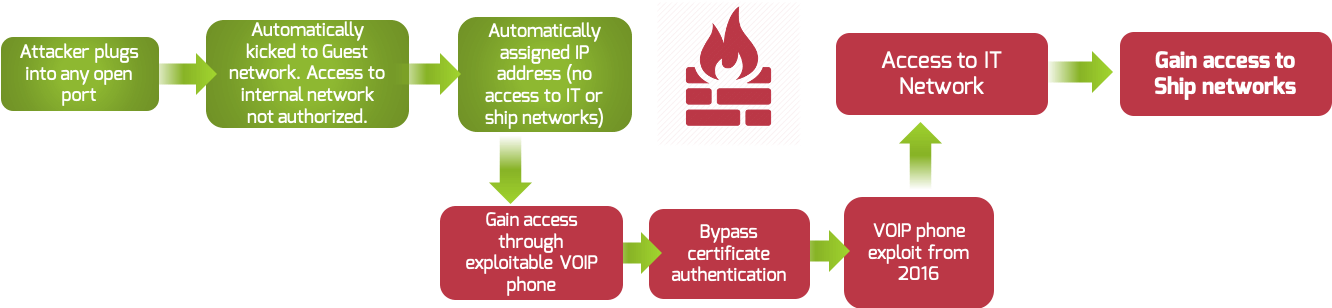
Figure 1: Cyber-attack path for an Unsecured VoIP System
In another example, a vessel used an FTP server to transition data and files between the IT and OT networks. This particular server was unpatched, thus becoming an attacker ingress point. Through the FTP server, the Mission Secure team was able to gain full administration-level control to the entire vessel within minutes. Printers are also notorious for being unpatched and often connected to both IT and OT networks.
From real field testing, attacker ingress points need to be monitored, managed, and secured to prevent unintentional security holes. When it comes to cybersecurity, no device can be left behind.
Vendors and suppliers: Third-party access
Another common risk comes from vendors, suppliers, and contractors. Remote third-party access management is often lacking in vessels, giving third parties unlimited access to the vessel’s systems. In less nefarious situations, uncontrolled third-party access can allow human errors to be introduced in the operations. For example, in one case, a third-party vendor made an unscheduled update to the vessel’s systems while in production, causing a physical process to stop errantly!
On the adversarial side, unmanaged third-party access is another route into a vessel or operation. In one such case, a third-party vendor acted as the virus carrier, infecting a vessel with malware from a USB stick. The malware was unknown to the vendor (and crew), and none of the vendor’s actions were abnormal. Nevertheless, the introduction of malware via USB stick infected the vessel and even spread to the onshore IT network.
Robust access management and OT network segmentation go hand-in-hand. Segmentation and micro-segmentation stop unbridled access in IT environments and should be doing the same in ICS environments. In the above examples, effective OT network segmentation can restrict vendor access (and potential damage) to specific areas of the network and/or expire at a set time. Segmentation can also help control and specify accessible systems and updates.
Securing maritime OT networks and operations
Securing maritime vessels and operations is critical to maintaining the efficient, safe, and reliable flow of goods and services. With the International Maritime Organisation (IMO) Resolution MSC.428(98), Maritime Cyber Risk Management in Safety Management Systems, enforcement date slotted for January 1, 2021, the maritime industry has taken notice of the security and safety risks from cyber adversaries.
“The IMO regulations are a step in the right direction,” states Ward. “But as we’ve seen in other industries like power, compliance is not security. Cyber resiliency and safety need to be the end goal. And for that to occur, OT systems—controlling propulsion, steering, navigation, ballast control, and a variety of loading and offloading processes—need to be locked down.”
Learn more in A Comprehensive Guide to Maritime Cybersecurity.
As hackers become even more sophisticated in their tactics, it’s inevitable that cyber-attacks against OT on ships are becoming the norm rather than the exception. It’s time for the maritime industry to take a look at every aspect of their ship operations to ensure they’re protected and resilient against these growing threats.
Originally published July 29, 2020, updated November 19, 2020.


