6 Min Read
3 Reasons to Worry About the Microsoft Exchange Server Hacks – Even If You Aren’t Vulnerable!
Written by Paul Robertson

A little more than a week into the Microsoft Exchange Server cyber-attack leveraging four zero-day exploits, organizations and governments continue to work on mitigation strategies – namely patching – and to uncover the extent, nature, and damage of the attack.
Whether you were never vulnerable to the exploit or patched before a compromise occurred, the Microsoft Exchange zero-day exploits have created a new normal for business communications. And while few are addressing this reality today, it’s a fact that all organizations will need to be aware of, manage, and protect against going forward.
What Makes the Microsoft Exchange Attack So Special?
The biggest differences are two-fold:
-
The scale of the attacks eclipses even the massive SolarWinds software supply chain breach.
-
The second, is that you can’t know if the people you’re communicating with have been compromised.
3 Reasons You Need to Worry, and Take Immediate Action
Within the last week, Microsoft issued an emergency patch and alternative mitigation techniques for its flagship Exchange Server reportedly attacked by Chinese nation-state actors in an automated malicious campaign and impacting potentially hundreds of thousands of victims globally and around sixty thousand in the United States.
While organizations should follow best practices to remediate the vulnerabilities, this particular cyber-attack doesn’t end there – for a number of reasons.
1. Who didn’t apply the patch?
The first issue is who has or hasn’t applied the patch and when.
A 2020 report from security firm Rapid7 looked at patch adoption rates for one Microsoft Exchange Server bug.
Eight months after the patch was released, the report found 61% of organizations still failed to apply the patch. Apply that percentage to the Microsoft Exchange Server vulnerability and we have the equivalent of 18,300 or more unpatched email servers in the U.S. alone.
At this rate, it will take 20 ½ months for nearly all vulnerable servers to be patched. And this new Microsoft Exchange Server emergency patch covers four vulnerabilities. And to further complicate patching the vulnerabilities, users are already reporting and experiencing issues applying the patch successfully.
At this rate, it will take 20 ½ months for nearly all vulnerable servers to be patched.
2. Who didn’t check for compromise?
Second, Microsoft clearly states the patch does not evict an adversary who has already compromised a server. In this situation, it’s not enough to patch alone – which history proves is a feat in and of itself. But then, organizations impacted by the vulnerabilities need to verify they were not compromised and search for indicators of compromise.
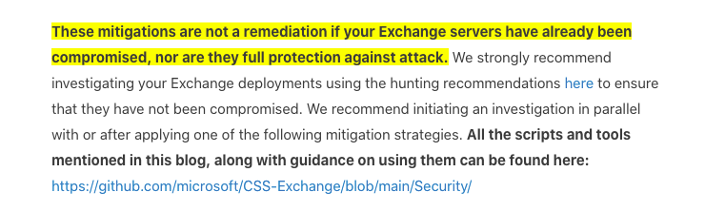
So, if you patched, did you also check for indicators of compromise and verify no adversaries were present?
Consider that Microsoft Email Exchange is one of the market leaders in the space and on-premise deployments — those affected by the attack — still comprise a portion of global Exchange mailboxes. The chances are high that someone in your business or greater business ecosystem hasn’t applied the patch or taken effective mitigation actions once the patch was applied to check for compromise.
3. Who can you trust now?
The Microsoft zero-day vulnerabilities don’t just allow bad actors to steal existing data and traverse networks. (Although another reason why segmentation and micro-segmentation are so important.) It also allows them to impersonate email addresses, add new addresses, or take full control of mailboxes remotely. The Exchange server exploits potentially give bad actors full access to email systems like an admin.
So, even if organizations patch at an infallible rate and check for compromise (which is highly unlikely), the threat will persist across organizations and around the world. Why? Who can you trust now?
For the greater ecosystem — vendors, service provides, and customers (VSCs) — the damage is done. It’s escalated the threat landscape and lowered our ability to trust the most basic functions of everyday business: email.
An Exponential Problem: Vendors, Service Providers, and Customers (VSC)
Before the Microsoft Exchange exploits, business email compromise (BEC) was already a multi-billion-dollar criminal enterprise. In 2019, the FBI estimated BEC (also known as email account compromise or EAC) comprised nearly half of all cyber-crime losses for the year, totaling at $1.77 billion. In a 2017 report, the FBI stated, “At its heart, BEC relies on the oldest trick in the con artist’s handbook: deception.”
BEC has been fundamentally changed with the Microsoft Exchange exploits, accelerating this illicit industry’s growth and threat. It’s no longer just spoofed or fake email accounts, spear phishing, and malware; the Microsoft zero-day exploits allow bad actors to leverage authentic, verified accounts (or servers) just as the real user would.
Consider the following:
-
Working with vendors: A long-time vendor sends an email to accounts payable (AP) to change their banking information. The clerk responds requesting additional verification, to which the vendor is able to verify as the authorized, correct person. The clerk confirms the banking change with the vendor and assures the updated information will be used for the next and future invoices.
Unbeknownst to the clerk, the Microsoft Exchange attack compromised the vendor, giving the adversary access to the email server. Because the server was compromised, all correspondences appeared to come from the correct user. And the malicious actor deletes all messages from the user’s mailbox before the real user notices them.
-
Working with third-party service providers: A third-party vendor (IT or industrial control system) engineer requests remote access to your network to update and configure new features. Access has already been set up for the engineer, but the engineer claims the latest update has affected the access, and it doesn’t work anymore. After validating via email or calling the number in the email signature line, your team verifies the engineer and expedites the new access request.
The Exchange attack has also compromised that service provider. Moreover, the adversaries not only took control of the engineer’s email but spoofed his phone number in his email signature.
-
Working with customers: A customer reaches out to technical support about a problem with their product. They aren’t sure what the problem is but are adamant it isn’t working, and they need immediate assistance. The technical support team accesses the network to review the product and run diagnostics.
However, the customer has an unknowingly compromised network. And behind the scenes, an adversary is causing issues and monitoring activity to gain access credentials.
In these situations, the real user and adversary are the same from the victim’s perspective. They are indistinguishable based on today’s common processes and policies. And bad actors will use the exploits for impersonating others. They’ll use them for fraud. They’ll use them to take advantage of existing relationships.
This is One of Those Big “New Normal” Moments.
In organizations with the Exchange server problem — whether unpatched or compromised — even emails from coworkers are not trustworthy. Anyone that has even one degree of separation away cannot trust communications from that unknown pool. But the larger question is more difficult to address; how do you know you have a problem across the business ecosystem?
Microsoft Zero-day Exploits: Your Next Steps
In this situation, taking proactive steps will only benefit companies. The following are four steps to take today to mitigate the risks of falling victims to the Microsoft Exchange exploits.
-
Spread the word. Ignorance can be costly, so spreading the word and generating awareness is the first step. Ensure your teams know how to think about email in light of this cyber-attack and how to evaluate the consequences of the new normal. This includes partners, vendors, suppliers, and customers. You need to know if you or your trusted partners were affected.
-
Do not trust email by itself. What is authentic and authorized versus fake and adversarial will become ever harder to identify. Organizations simply cannot afford to trust email alone. For that matter, any single communication channel should be suspect. Email and text messages are increasingly easy to compromise, fake, and abuse. And voice and video are following fast on their heels.
-
Establish a multi-channel change management program. Companies and employees simply cannot afford to trust email for unanticipated changes. Never alter payments, send credentials, or make ‘quick’ decisions based on email messages alone. Setting up a multi-channel change management program can help organizations and their employees set up more robust procedures before errant or adversarial changes are initiated.
-
If in doubt, double-check live. More than ever before, if something seems suspicious, out of the blue, or unexpected, call the real person and verify live (not through text messages alone).
When in-person and face-to-face contact is at all-time lows, today’s remote work world is a prime environment for the Microsoft Exchange attack. Taking proactive actions starts with awareness and a high level of attention to details, moves to additional communications paths and procedures, and will likely result in better tools and reputation tracking in the future.
Now that the patches are out, multiple groups are already making and using new exploits. Vendors, service providers, and customers (VSC) are going to be amongst those with unpatched or compromised servers. And we already see the impacts. As Bloomberg states (emphasis added), “A sophisticated attack on Microsoft Corp.’s widely used business email software is morphing into a global cybersecurity crisis, as hackers race to infect as many victims as possible before companies can secure their computer systems.” Even today, reports have emerged of adversaries leveraging the exploit to mine cryptocurrency — and it’s anticipated the adversaries and malicious uses will only explode in the days and weeks to come.
The attackers have been creating email accounts and intercepting messages to current accounts, as well as compromising additional systems. The world will continue to see the negative impacts from organizations that were compromised or haven’t patched for a long time.
*Mission Secure will also be providing free resources on our website to help organizations mitigate and manage the Microsoft Exchange vulnerabilities.
Originally published March 17, 2021, updated April 28, 2021.