6 Min Read
Real-World Lessons Learned from Maritime Cybersecurity Incidents
Written by Mission Secure

Current Threats to Maritime Security
If you’re in charge of cybersecurity for your maritime vessel networks, the last thing you want to wake up to is your mobile phone blowing up and your organization in the headlines because of a cyberattack. Between vessels being more connected than ever, the flourishing cybercrime economy contributing to over $1 trillion in losses and a global pandemic that has changed how we work, it seems that it’s all you can do to keep your vessel networks running.
With a 400% increase in attempted cyberattacks targeting the maritime industry since February 2020, it’s not just keeping your networks running that will keep you up at night. The global pandemic has brought on an influx of cybersecurity issues, including but not limited to phishing attempts, ransomware, employees working remotely, and network access adjustments due to travel restrictions. But hopefully, you’ve deployed your cybersecurity risk management plan and developed an optimal design for your vessel network infrastructure. Even after all of that, your hard work might have just delayed the inevitable – the day your organization ends up in the headlines. The good news is that sometimes, hindsight doesn’t have to be 20/20.
Learn about specific protective security measures in our Comprehensive Guide to Maritime Cybersecurity.
In this blog, we will walk through three cybersecurity incidents that made headlines in the maritime industry and detail the lessons learned from each event that can help you stay ahead of potentially catastrophic cyberattacks.
Maritime Cyber Attacks 2017 | Incident #1: Maersk
In June 2017, Danish shipping giant Maersk suffered one of the most high-profile and damaging maritime cybersecurity incidents to date. The largest container ship and supply vessel operator with offices across 130 countries and over 80,000 employees went dark after being hit with NotPetya.
What’s interesting about NotPetya is that while it has the general characteristics of ransomware, it is not technically ransomware. It’s able to spread on its own without any spam emails or social engineering. It relies on tools like the EternalBlue and EternalRomance exploits developed by the US National Security Agency (NSA). Designed as a wiper, NotPetya encrypts everything in its path and damages the data beyond repair with no way to recover. What was allegedly a state-sponsored Russian cyberattack targeted at Ukrainian companies, NotPetya spread beyond the Ukrainian borders and caused an estimated $10 billion in total damages worldwide.
When NotPetya hit Maersk, it propagated through the network in seven minutes. Computer screens faded to black, and employees scrambled to unplug any connected devices throughout the offices to protect against the fast-spreading malware. Except for an undamaged domain controller from the Ghana office that had experienced an unrelated power outage, Maersk lost most of its data, with over 49,000 laptops and 4,000 servers destroyed. Damages were estimated at over $300 million.
“In the event that we see something suspicious going on in the network, we don’t just flag it – we stop it.”
– Maersk's CISO
Lessons Learned from Maersk
Beyond Protection, Focus on Response Plans: You have to assume that hackers are already in your network, and you need extra intelligence to assess what or who is in your network. Maersk has invested in a separate internal threat team that studies emerging threats and determines how to respond to and mitigate future avenues of attack. Your response plans should be tested and updated frequently to improve processes, identify any shortcomings and determine new mitigation actions against any emerging cyberattacks.
Establish a Data Protection and Recovery Strategy: Yes, you need to ensure your vessel network and critical control systems are protected, but you also need a data protection and recovery plan in place so that if your network is knocked offline, you can still operate. You also need to rethink your backups. Standard online backups are no longer a safe approach. If your backups are attached to your network, they’re susceptible to attack. You need to protect your vessel OT network against data loss and be able to reconstruct your database after data loss, and the addition of offline backups should be considered.
Maritime Cyber Attacks 2018 | Incident #2: COSCO
Just over a year after the Maersk attack, it was time to find out if the maritime industry had taken steps to strengthen their cybersecurity defenses. That test would come in July 2018, when the China Ocean Shipping Company (COSCO) became a victim of the SamSam ransomware. When SamSam hit, it caused a failure across COSCO’s networks in the United States, Canada, Panama, Argentina, Brazil, Peru, Chile and Uruguay.
Similar to NotPetya, once SamSam gains access to your network, hackers can gain administrative rights and run executable files without human action or authorization. The group behind SamSam doesn’t push their ransomware as a commodity through a SaaS model – they keep development in-house and update it frequently to avoid enterprise security defenses.
The SamSam attack occurred soon after COSCO acquired one of its rivals, Orient Overseas Container Lines. By activating their contingency plans, COSCO’s operations were back to normal in five days. Any damages from the cyberattack have not been disclosed.
Lessons Learned from COSCO
Segment Your Maritime Networks: Because COSCO had isolated its internal networks across the globe, they were able to contain the damage. Network segmentation helps you reduce the attack surface and is a very useful architectural concept of a defense-in-depth cybersecurity strategy. Your OT and IT networks need to be segmented to limit the spread of a cyberattack and stop it from spreading laterally toward your critical vessel controls.
Have a Contingency Plan: As with any organization, those in the maritime industry need to have a contingency plan in place that will keep operations running in the interim while they recover from a cyberattack. In COSCO’s case, they made sure that they had alternative procedures to communicate with customers and deal with service requests. They also utilized social media to reply directly to service requests and updated a FAQ document every time there was a status change. While the process of communicating with customers via emails and phone calls took up a little more time, they were able to continue cargo handling in the United States and Canada without any disruptions.
Maritime Cyber Attacks 2019 | Incident #3: Norsk Hydro
In March 2019, a crippling ransomware attack brought Norsk Hydro’s worldwide network down to its knees, when they fell victim to the LockerGoga ransomware.
LockerGoga’s wrath is especially tumultuous because it disables the computer’s network adapter to disconnect it from the network, changes both user and admin passwords and logs the machine off. LockerGoga will sometimes leave the victim without the ability to see the ransom message or even know that they’ve been hit with the ransomware, further delaying an organization’s ability to recover their systems.
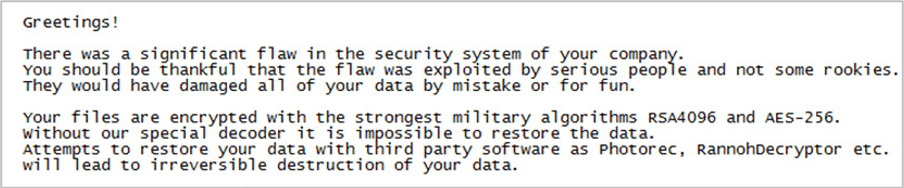
Text file message included on a Norsk Hydro system from the hackers
Norsk Hydro estimated that the hackers had been in their network two or three weeks before they were discovered. With over 22,000 computers and thousands of servers affected over five continents, LockerGoga brought down Norsk Hydro’s entire worldwide network, affecting their production and office operations. Damages were estimated at $71 million.
Lessons Learned from Norsk Hydro
Be Transparent: Just like Maersk, Norsk Hydro shared more information than usual with the authorities, giving investigators enough information to warn other organizations to prevent similar attacks. Norsk Hydro took their transparency to the next level to keep everyone informed. They held daily press conferences at their Oslo headquarters, set up a temporary website, provided updates on Facebook and conducted daily webcasts hosted by senior staff who answered audience questions.
Never Let Your Guard Down: It took several months for Norsk Hydro to rebuild its infrastructure and deploy a segmented network to ensure that IT and OT were protected. During their initial investigations, they found several variants of the virus that hackers had planted just in case they weren’t successful the first time. Hackers spend many hours developing, testing and executing their attacks, and you need to take that same approach with your cybersecurity strategy. Keeping your networks secure is a company-wide responsibility. It requires consistent security awareness and education for the organization and ongoing monitoring of your cybersecurity framework to minimize risk across your maritime environment.
“Gradually, new computers and servers are connected to these zones, and more and more employees can now connect to the network. The danger is still not over.”
– Norsk Hydro’s IT Manager
A Recap of Lessons Learned
While the Norsk Hydro cyberattack isn’t maritime-related, it serves as a wake-up call for the industry. Hackers do not discriminate – they are hitting organizations large and small, with or without abundant cybersecurity resources. Protecting your vessel OT environment is no easy task, but with the right security measures and procedures in place to help you maintain the integrity and continuity of your vessel operations, you’re off to a good start keeping ahead of malicious hackers.
Let’s recap our lessons learned for vessel cybersecurity and effective cyber risk management:
Beyond Protection, Focus on Response Plans: Your response plans need to be tested and updated frequently to identify any shortcomings, improve processes and determine new mitigation actions.
Establish a Data Protection and Recovery Strategy: A data protection and recovery plan will help you keep operations running in the event your network is knocked offline.
Segment Your Maritime Networks: Segmenting your networks will limit the spread of a cyberattack toward your critical vessel controls.
Have a Contingency Plan: A concrete contingency plan will help keep your operations running in the interim while your organization recovers from a cyberattack.
Be Transparent: Be transparent to help the authorities and help others in the maritime industry learn from your experience so that they are better prepared.
Never Let Your Guard Down: Protecting your maritime network requires consistent security awareness and education and ongoing monitoring of your cybersecurity framework.
Originally published August 17, 2020, updated December 14, 2020.


