Guide
A Comprehensive Guide to Manufacturing Cyber Security
Securing critical manufacturing sectors from today’s cyber risks & threats.
The manufacturing sector is one of the largest, most diverse, and rapidly changing segments of the global economy. And it is a top target for cyber adversaries. Robotics, automation, machinery, IoT/IIoT, smart devices — it’s time to secure manufacturing from threats, hackers, and risks.
New sections in the Comprehensive Guide to Manufacturing Cyber Security will be published over the next several weeks. Don’t forget to subscribe to get notifications!

Table of Contents
Key manufacturing segments include aerospace and defense, automotive, chemicals, computer hardware, electronics, construction, consumer packaged goods (CPG), food and beverage, transportation, pharmaceuticals, and industrial manufacturing.”
What is Critical Manufacturing, and Where is it Going?
Many manufacturing segments of the economy are classified as critical infrastructure in the United States and elsewhere in the world. This is understandable given that manufacturers create the infrastructure needed by so many other sectors of the economy. Manufacturing is, therefore, foundational to other areas of the economy, and a vibrant manufacturing base is viewed by many countries as a particularly important metric of overall national strength and vitality.
The manufacturing sector is, in fact, one of the largest, most diverse, and rapidly changing segments of the global economy. Key manufacturing segments include aerospace and defense, automotive, chemicals, computer hardware, electronics, construction, consumer packaged goods (CPG), food and beverage, transportation, pharmaceuticals, and industrial manufacturing.
Industry 4.0
This revolution is driving a wholesale re-evaluation of how to approach cybersecurity in manufacturing and has created a consensus that a complete migration to this new manufacturing environment cannot be successful without cybersecurity itself becoming a foundational pillar of this new era.”
We are in the midst of a fourth Industrial Revolution that is upending traditional notions of best practice in operations, supply chain management, cybersecurity, disaster recovery, and other aspects of manufacturing. This revolution is driving a wholesale re-evaluation of how to approach cybersecurity in manufacturing and has created a consensus that a complete migration to this new manufacturing environment cannot be successful without cybersecurity itself becoming a foundational pillar of this new era.
What has become known as Industry 4.0 has been evolving and consolidating for almost a decade, with Germany driving innovation and investment. (Aspects of this idea are also found in Japan’s Society 5.0 initiative and China’s Made in China 2025 industrial plan.) The number of technologies finding their way onto manufacturing floors, into supply chains, and new categories of connected objects is both impressive and bewildering. There truly is a revolution underway, and it is global in its reach and increasingly in its impact. Early adopters have included automotive, mechanical and plant engineering, electronics, and high technology manufacturers.
Industry 4.0 refers to a combination of hardware, software, and services that is modernizing manufacturing infrastructure to improve efficiencies in all aspects of manufacturing processes. Technologies that are being applied to create smart factories include: robotics, sensor technology, additive manufacturing (3-D printing), augmented and virtual reality, wearables, artificial intelligence and machine learning, big data analytics, and cloud computing.
The goal of integrating these technologies into manufacturing is to deliver smart, more aware, more agile, and more resilient infrastructure to design, optimize, and create manufactured goods. This is all done while delivering a safer work environment that uses fewer resources and optimizes maintenance practices to limit downtime.
Industry 4.0 adoption is reaching down into small- and medium-sized businesses (SMB) and across all types of manufacturing. Many of these technologies do not require large capital investments. Not every manufacturer needs expensive robotics, for example. The most important technologies being deployed broadly by manufacturers are robotics, wearables, connected devices (IoT), additive manufacturing (3-D printing), virtual reality (VR) and augmented reality (AR), artificial intelligence (AI) and machine learning (ML), and big data analytics.
Robotics
The first industrial robot was deployed in 1961. While the use of robots in manufacturing has continued to expand over the decades, the majority are still used in automotive plants, where they represent more than half the “labor” needed to build automobiles and trucks. Robotics has advanced to the point that 100% automated “lights-out” factories have been operational for several decades in sectors such as computer manufacturing.

Wearables
Wearable computing and sensor devices are finding numerous applications in manufacturing environments. Devices fall into several categories, many of which are focused on employee safety, such as fall prevention, sleep prevention, noise reduction, or improved respiration. Many wearables are also focused on enabling better communication, potentially including access control — between employees and between machinery — as well as on providing easier access to information through a host of delivery mechanisms.

Internet of Things/ Industrial Internet of Things
The Internet of Things (IoT)/ Industrial Internet of Things (IIoT) references a broad set of physical devices that combine embedded sensors, processing power, software, and often analytic capabilities to communicate real-time information about aspects of the physical world, such as temperature, pressure, motion, etc. Consumer applications can include smart home devices, among many others. A subcategory of more hardened devices generally termed the Industrial Internet of Things (IIoT) has also developed and found its way into manufacturing plants. IIoT devices can include an actuation component and, therefore, can function as industrial control system (ICS) devices. The manufacturing applications of IIoT are almost limitless.

3-D Printing
Additive, or 3-D, printing enables the creation of three-dimensional objects directly from a CAD drawing by building up an object one layer of material at a time. 3-D printing is particularly useful in the prototyping phase of product development. Still, the size, speed, and quality of 3-D printing have improved to the degree that the technique is used in space, aerospace, wind turbine, and many other critical manufacturing sectors.

Virtual Reality/Augmented Reality
Virtual reality (VR) describes a self-contained, computer-simulated environment and is another technology with broad application in product development applications for manufacturers. It is also an important tool for worker training. Augmented reality (AR) is a less immersive experience and involves superimposing digital information into the real world. This information can be as simple as a heads-up display of written material, for example, repair manuals, or it can be much more immersive and include other senses such as hearing and touch.
Machine Learning/Artificial Intelligence
Machine learning (ML) is a subset of artificial intelligence (AI). ML is a technique where computer algorithms can be trained to “improve” through experience. AI and ML can improve manufacturing techniques in a host of ways and are being applied to generate general process improvements, accelerate product development, and improve quality control. Manufacturers today are using AI/ML to improve manufacturing yields, optimize asset management, manage supply chain and inventory, improve predictive maintenance and demand forecasting, among many other applications.

Big Data Analytics
Many technologies, particularly IIoT, are driving the need for better analysis of large data sets. Big data analytics is a field of research that addresses techniques for analyzing data sets that are too large to be dealt with in traditional data processing application software. Big data and IIoT work in tandem to monitor, analyze, and react to environmental data in manufacturing environments. Again, the applications are almost unlimited, but an early use case was predictive maintenance.
5G
5G is the fifth-generation technology standard for broadband cellular networks. Telecommunications providers began rolling out this successor to 4G in 2019. 5G is designed to deliver massive bandwidth improvements over its predecessor, with maximum download speeds of 10 Gbps. This should allow the networks to not only act as a traditional network for cellular calls but also to become general-purpose networks for internet service providers. This ubiquitous, global, wireless bandwidth is expected to enable further a multitude of IIoT use cases, as well as traditional industrial control system (ICS) applications.
Building a Framework
There is a lot of effort underway to provide a framework that encompasses all of the technological changes currently underway in manufacturing. For example, the German Electrical and Electronic Manufacturers’ Association published the Reference Architecture Model for Industry 4.0 (RAMI 4.0) in July 2015. The RAMI 4.0 model maps hierarchical levels (e.g., the Purdue model) against functional communication levels that run from high-level business concerns to individual assets. Finally, the model considers the life cycle of a product under development or in manufacturing.
The big-picture approaches are welcome, and organizations should certainly be considering the strategic implications of each new technology purchase and how those technologies can best be deployed, integrated, and leveraged. Investments in these new technologies are typically made piecemeal, but by adhering to a common reference architecture, these incremental investments can provide more holistic benefits.

Cybersecurity in Action
Learn how improved cybersecurity helped a paper mill manufacturer extend control system lifespan.
Read the Case StudyDeploying Industry 4.0 Technologies
Manufacturers can benefit from these technologies in multiple deployment scenarios. Broadly, they can be seen as affecting the supply chain, smart factory, and connected objects. Application of each technology can be found across this value chain, but these buckets will prove useful when thinking about common use cases as well as compliance requirements associated with manufacturing activity, which is too broad a sector to have an overarching regulatory framework.
The manufacturing sector is one of the largest, most diverse, and rapidly changing segments of the global economy. And it is a top target for cyber adversaries. Robotics, automation, machinery, IoT/IIoT, smart devices — it’s time to secure manufacturing from threats, hackers, and risks.
Critical Manufacturing Cybersecurity
It should come as no surprise that all of this technological change is causing the industry to reevaluate how to approach cybersecurity in manufacturing for both information technology (IT) and operational technology (OT) infrastructure. Industry 4.0 requires an even tighter coupling of traditional IT and OT. In almost every case, these new technologies create additional data, create additional connections to existing data, or enable the storage and use of data in new, more distributed locations.
These architectural changes raise obvious questions about cybersecurity. But they also make clear the need to reconsider traditional approaches to disaster recovery and resiliency planning. Organizations will have a much richer set of operational data that are both distributed and redundant, along with powerful predictive analytic capabilities that will make preventing or recovering from system outages simpler. But the additional connectivity to OT infrastructure required to enable this benefit is accompanied by greater exposure to cybersecurity threats as the attack surface is enlarged.
Industry 4.0 requires an even tighter coupling of traditional IT and OT. In almost every case, these new technologies create additional data, create additional connections to existing data, or enable the storage and use of data in new, more distributed locations.
Legacy Challenges
Legacy OT systems are burdened with a long list of cybersecurity concerns, including:
- Equipment with decades-long life cycles,
- An inability to patch systems due to stability concerns,
- And a lack of basic cybersecurity features such as user authentication or encryption.
Historically, OT security personnel could at least credibly claim that such systems were “air-gapped” to ensure isolation from the rest of the world. However, complete isolation, if it ever existed, has become impossible today. No manufacturing organization can embrace an Industry 4.0 strategy without addressing the severe cybersecurity risks that attend it. This strategy requires a recognition of the almost complete integration of IT with OT in modern Industry 4.0 deployments.
OT cybersecurity has traditionally been its own discipline. Analyst firm Gartner defines OT cybersecurity as: “The practices and technologies used to protect people, assets and information involved in the monitoring and/or control of physical devices, processes and events, particularly in production and operations.” Over the years, as IT has been incorporated into OT systems, the approaches to cyber protection have also merged, but the primary goals of the two disciplines remain distinct.
IT and OT cybersecurity differ in fundamental ways but not only because the systems often require different security controls. The real distinction is that IT and OT security practitioners have different goals for “securing” their assets and different definitions of “secure.” This is hardly surprising given that IT is chiefly concerned with digital assets and OT is chiefly concerned with physical assets.
The Physical Impact of Manufacturing Cyberthreats
CIA vs. CAIC
The standard for IT cybersecurity is the well-known confidentiality, integrity, and availability (CIA) triad. Enterprise data is considered proprietary intellectual property, and therefore keeping digital assets under lock and key has been the primary objective of IT cybersecurity strategies. This is followed by the need to ensure the integrity of digital assets. Organizations must not only keep their data out of competitors’ hands, but they must also ensure that data is not corrupted, either intentionally or otherwise. Finally, that data should be available internally to appropriate employees and partners, and potentially, customers.
The standard for OT cybersecurity, however, requires a broader and a reordered set of priorities, namely control, availability, integrity, and confidentiality (CAIC). Maintaining control of all physical assets to ensure their safe operation at all times is the primary objective of OT cybersecurity and overrides all other concerns. The next most important goal for OT cybersecurity is availability. OT is present in all critical infrastructure facilities, and critical infrastructure typically needs to be available 24/7/365. Integrity is also essential, particularly to the degree it ensures safety and availability. The confidentiality of OT data is the least important concern.
-
INFORMATION TECHNOLOGY (IT)
CIA
Confidentiality
Integrity
Availability
VS
-
OPERATIONAL TECHNOLOGY (OT)
CAIC
Control
Availability
Integrity
Confidentiality
Cybersecurity Challenges Affecting the Manufacturing Industry
The 2020 IBM X-Force Threat Intelligence Index reported an unprecedented 2,000% year-over-year increase in incidents targeting OT environments, like critical infrastructure manufacturing. Attackers are taking advantage of the larger attack surface of these systems and, unfortunately, often are not finding them difficult to penetrate. Typical attacks include brute-force password attacks against legacy OT hardware and software, as well as targeted attacks against known vulnerabilities in legacy equipment.
While that extraordinary growth in attacks might astonish even close industry watchers, it should shock no one that attacks are on the rise. Juniper Research has forecast that globally there will be 83 billion connected IoT devices by 2024, and 70% of these will be in the industrial sector. This level of connectedness completely changes the relationship between IT and OT. And unfortunately, many new connected devices are built with just enough processing power and bandwidth to create vulnerabilities but not enough headroom either to support a firmware update if a vulnerability is discovered or to support an agent to provide protection in the event of an attack. This, of course, necessitates the need for a comprehensive OT protection strategy that reassesses the level of connectivity to and interdependency with traditionally OT assets.
"And unfortunately, many new connected devices are built with just enough processing power and bandwidth to create vulnerabilities but not enough headroom either to support a firmware update if a vulnerability is discovered or to support an agent to provide protection in the event of an attack."
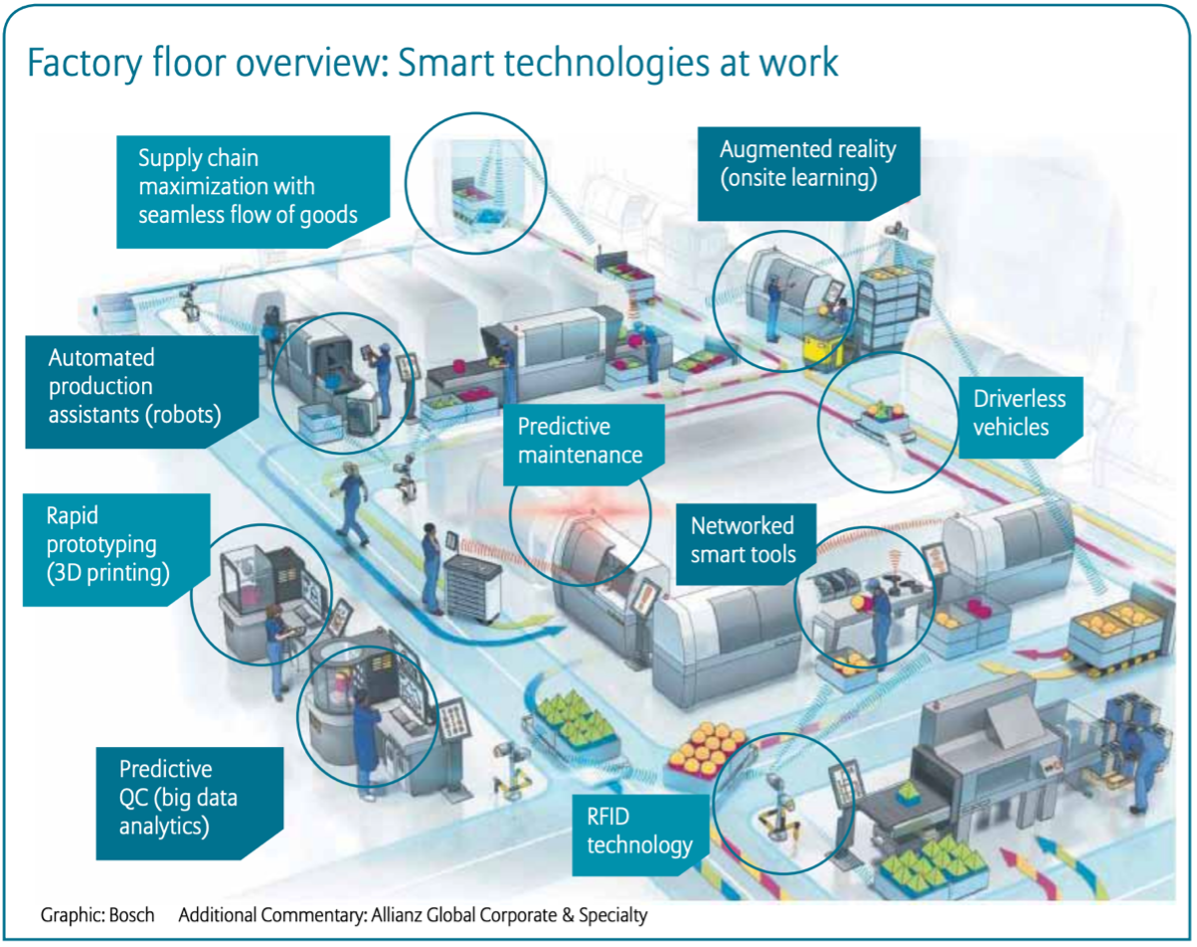
Figure: Factory Floor Overview – Smart Technologies at Work
Main Operational Technology (OT) Threat Actors
Attacks Against Manufacturers
According to a report by the cyber insurance company Allianz, cyberattacks against critical infrastructure are more likely to target ICS than attempt to steal data. A survey of critical infrastructure suppliers showed that 54% reported attempts to control systems, and 40% had experienced attempts to shut down systems. While manufacturers are particularly vulnerable to attacks designed to cause extended operational downtime, they are also highly sensitive to the loss of trade secrets and customer data. This is true across the board but particularly for manufacturers working in the Defense Industrial Base (DIB) sector.
According to a report by the cyber insurance company Allianz, cyberattacks against critical infrastructure are more likely to target ICS than attempt to steal data.
Disruptive Cyberattack Example at Honda Manufacturing Plant
Unfortunately, business changes made in response to the COVID-19 virus have likely contributed to the increase in attacks during 2020. Remote workers are particularly vulnerable to phishing attacks, which can become a vector for ransomware attacks. Ransomware typically locks down data until a ransom is paid, but for a manufacturer, that is the equivalent of locking down the production line. Manufacturers have been particularly hard hit by ransomware, seeing the steepest increase of any industry in the first quarter of 2020, according to a June 2020 report from cyber insurer Beazley.
Manufacturers suffer from having to maintain highly dispersed and heterogeneous infrastructure and supply chains. Embracing Industry 4.0 technologies makes it even more difficult for organizations to create and maintain accurate real-time inventories of their OT/IoT devices and systems. But this is a minimum requirement for developing a baseline cybersecurity strategy for OT and IT systems: manufacturers must be able to monitor their network state in real-time and understand device behavior. The ability to detect anomalous activity in near real-time is key to preventing operational disruptions, whether from maintenance issues or cyberattacks.
Another difficulty is that basic threat intelligence information is often lacking on attacks targeting OT and IIoT infrastructure. Cybersecurity teams need to be able to detect, analyze, and react to indicators of compromise (IOCs) and anomalous behavior in their network. The broad deployment of IIoT devices provides numerous beachheads for attackers who can then quickly move laterally through a network. Network segmentation is, therefore, a critical component of OT cybersecurity strategies.
The 2019 Deloitte and MAPI Smart Factory Study conducted by Deloitte and the Manufacturer’s Alliance for Productivity and Innovation (MAPI) found that over 12 months, 40% of the manufacturers surveyed had operations affected by a cyber incident. Of those affected, 87% suffered unauthorized access to infrastructure; 86% experienced operational disruptions; and 85% experienced intellectual property theft.
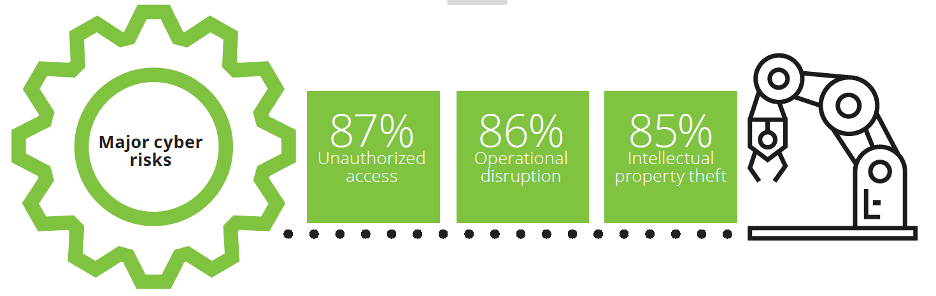
Figure: Stats from the 2019 Deloitte and MAPI Smart Factory Study
Recent Successful Attacks
Unsurprisingly, there have been a host of successful attacks against even the largest manufacturing companies over the last several years. Mondelez was hit by the encrypting malware NotPetya in 2017. Renault-Nissan stopped production in five plants in 2017 when the WannaCry ransomware struck. LockerGoga ransomware was also deployed successfully against aluminum manufacturer Norsk Hydro in 2020. The company was forced to temporarily close many of its plants. In 2019, space and defense manufacturer Visser Precision was hit with the DoppelPaymer ransomware.
Significant Cyber incidents against Manufacturers in Recent Years
-
AUGUST 2020
Israeli Defense Manufacturers:
The Israeli defense ministry announced that it had successfully defended against a cyberattack on Israeli defense manufacturers launched by a suspected North Korean hacking group.
-
APRIL 2020
Pharmaceutical Manufacturers:
U.S. officials reported seeing a surge of attacks by Chinese hackers against healthcare providers, pharmaceutical manufacturers, and the U.S. Department of Health and Human services amidst the COVID-19 pandemic.
-
MARCH 2020
Manufacturing Sector:
Chinese hackers targeted over 75 organizations around the world in the manufacturing, media, healthcare, and nonprofit sectors as part of a broad-ranging cyber espionage campaign.
-
NOVEMBER 2019
Manufacturing Sector:
Microsoft security researchers found that in the last year, an Iranian hacker group carried out “password-spraying attacks” on thousands of organizations, but since October, they have focused on the employees of dozens of manufacturers, suppliers, or maintainers of industrial control system equipment and software.
-
AUGUST 2019
Semiconductor Manufacturing:
A previously unidentified Chinese espionage group was found to have worked since 2012 to gather data from foreign firms in industries identified as strategic priorities by the Chinese government, including telecommunications, healthcare, semiconductor manufacturing, and machine learning. The group was also active in the theft of virtual currencies and the monitoring of dissidents in Hong Kong.
-
MARCH 2018
U.S. Manufacturing Facilities:
The FBI and Department of Homeland Security issued a joint technical alert to warn of Russian cyberattacks against U.S. critical infrastructure. Targets included energy, nuclear, water, aviation, and manufacturing facilities.
-
JANUARY 2016
Aerospace Manufacturing:
Austrian-based aerospace parts manufacturer FACC had $54.5 million stolen in a cyberattack. The attackers ignored FACC’s intellectual property or proprietary data, and business operations were not affected.
Source: Center for Strategic & International Studies: Significant Cyber Incidents
Manufacturers are attractive targets for both criminal and nation-state attackers. The June 2020 attack against automaker Honda is particularly interesting. As described in The New York Times, “ . . . the attack appears to have been carried out by software designed to attack the control systems for a wide variety of industrial facilities like factories and power plants. Such cyberweapons previously were only known to have been used by state agents.”
The attack temporarily halted production in Honda plants in North America, Brazil, India, and Turkey. The attack tool was suspected to be a new variant of ransomware (in the Ekans/Snake family) designed to disrupt industrial systems. It is unusual in that in addition to encrypting data files, Ekans also includes functionality designed to stop a number of processes related to ICS operations. Argentinian energy company Edesur S.A. was also attacked with Ekans in June 2020.
Manufacturing Cybersecurity Compliance Considerations
In the U.S., the manufacturing sector does not have overarching, mandatory cybersecurity regulations, but many manufacturers meet the official criteria for “critical infrastructure,” which does come under special scrutiny.
Leading OT Cyber Regulations
More often, regulatory oversight will depend on what a manufacturer makes or to whom it sells products. For example, medical device manufacturers would follow U.S. Food and Drug Administration (FDA) cybersecurity regulations, while DIB manufacturers would look to the U.S. Department of Defense (DoD), while IoT device manufacturers are facing a wave of new cyber regulations from multiple states, as local jurisdictions attempt to place cybersecurity requirements what they see as a growing attack surface. Finally, the U.S. Securities and Exchange Commission (SEC) issued interpretive guidance in 2018 that outlined its expectations for corporate disclosure on cybersecurity risks for any public corporation, which it considers material information for investors.
Manufacturers in the U.S. should view recommendations for critical infrastructure providers as best practices. The cybersecurity regulation regarding critical infrastructure providers has been evolving since shortly after the 911 attacks. There have been numerous Executive Orders, particularly over the last decade, that have attempted to improve critical infrastructure cybersecurity.
Quick History of U.S. Regulations
These Executive Orders include Executive Order 13636: “Improving Critical Infrastructure Cybersecurity,” (February 12, 2013); Executive Order 13800: “Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure” (May 11, 2017); and Executive Order 13873: “Securing the Information and Communications Technology and Services Supply Chain.” (May 15, 2019).
In 2015, the Department of Homeland Security (DHS) released a Critical Manufacturing Sector-Specific plan as an annex to the National Infrastructure Protection Plan. Cyberattacks were called out as a significant critical manufacturing sector risk. In the same year, DHS released “Critical Manufacturing Sector Cybersecurity Framework Implementation Guidance.” And in 2017, the National Institute of Standards and Technology (NIST) released its internal report titled “Cybersecurity Framework Manufacturing Profile” (NISTIR 8183). Regardless of whether a manufacturer technically falls under the DHS definition of “critical manufacturer,” these documents should be viewed as providing current best practice guidance for cybersecurity.
A Quick Look at the IoT Cybersecurity Improvement Act of 2020
European Union Activity
The European Union (EU) Directive on security of network and information systems (NIS Directive) entered into force in EU countries in 2016. The EU Cybersecurity Act became effective in 2019, strengthening the role of the EU Agency for cybersecurity (ENISA). The act created a permanent mandate for the agency, expanded powers, and widened its scope, including setting up a European cybersecurity certification framework. ENISA is particularly active with respect to Industry 4.0 and IIoT guidance. Two important ENISA documents are “Industry 4.0 Cybersecurity: Challenges & Recommendations” and “Good Practices for Security of Internet of Things in the Context of Smart Manufacturing.”
Manufacturing Cybersecurity Maturity Model
A particularly vexing problem for manufacturers is the global nature of their supply chains. This has led to several efforts to create more secure supply chains, most notably perhaps the DHS’s Cybersecurity Maturity Model Certification (CMMC) program for the DoD supply chain.
In 2020, Carnegie Mellon University and the Johns Hopkins University Applied Physics Laboratory LLC released CMMC version 1.0 as part of work funded by the DoD. The CMMC is designed to help improve the security posture of the 300,000 companies that make up the DIB sector and the supply chain of the DoD.
The initial mandate of the CMMC is relatively modest: to protect unclassified (but sensitive) data across the DIB ecosystem. This includes federal contract information and controlled unclassified information. Although manufacturers represent only a subset of the companies covered by CMMC, and DIB manufacturers likewise are only a subset of the critical manufacturing sector, the CMMC is worth understanding both as an example of best practice and because it is likely to become a blueprint for broader regulation, at least in the U.S. For best practice in protecting OT manufacturing infrastructure, we will turn shortly to the NIST Cybersecurity Framework Manufacturing Profile, which also provides a coarse-grained maturity model.
As the CMMC document notes, “a maturity model is a set of characteristics, attributes, indicators, or patterns that represent capability and progression in a particular discipline. The content of such a model typically exemplifies best practices and may incorporate standards or other codes of practice to that discipline.”
The CMMC model framework organizes cybersecurity processes and practices into domains that are mapped across five maturity levels.
- Level 1 corresponds to Basic Cyber Hygiene practices that typically involve ad-hoc implementation with limited or no documentation.
- Level 2 corresponds to Intermediate Cyber Hygiene practices and is viewed as a transitional stage with a focus on a prioritized subset of security requirements.
- Organizations at Level 3 are considered as practicing Good Cyber Hygiene, meeting all the security requirements of the benchmark NIST SP 800-171 standard.
- Level 4 practices indicate a more Proactive posture with security practices reviewed and measured for effectiveness and with corrective action taken as necessary.
- And finally, the Advanced/Progressive practices of Level 5 require organizations to optimize their security process implementation across their assets and include a focus on protecting against advanced persistent threats (APTs).
(See the Cybersecurity Maturity Model Certification Version 1.0 Appendices published on January 30, 2020 for more detail on policy construction recommendations at each maturity level.)
The biggest value of a maturity model is its focus on cybersecurity as a process that needs to be structured, prioritized, and well documented. This should be the orientation regardless of whether the focus is on cybersecurity for IT or for OT.
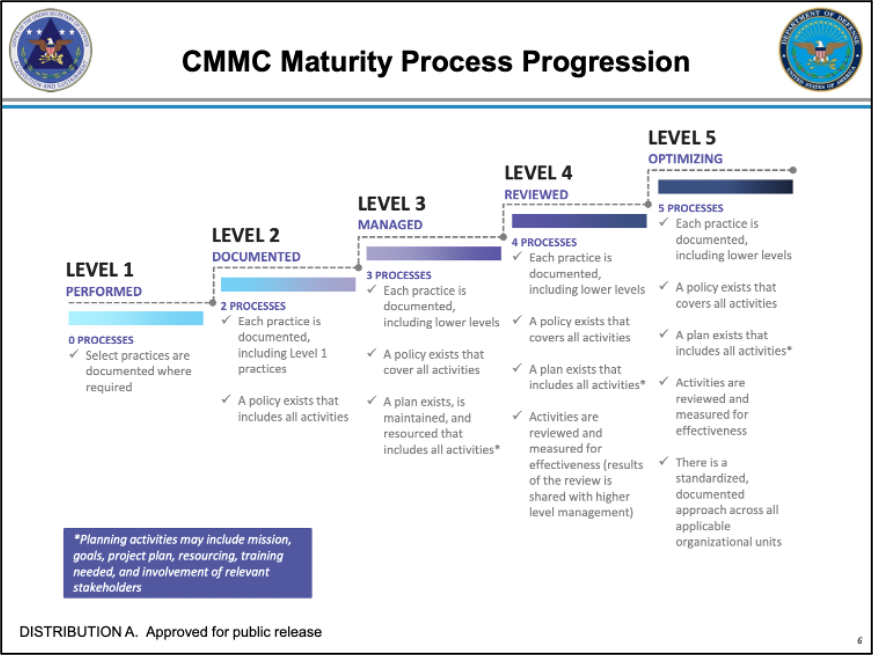 Figure: CMMC Maturity Process Progression
Figure: CMMC Maturity Process Progression
The NIST Cybersecurity Framework Manufacturing Profile
The NIST Cybersecurity Framework Manufacturing Profile provides a useful framework for protecting both IT and OT infrastructure. As the document notes, the “reliance on technology, communication, and interconnectivity of ICS [industrial control systems] and IT has changed and expanded the potential vulnerabilities and increased potential risk to manufacturing system operations.”
NIST takes a broad view of manufacturers, addressing the needs of process-based manufacturers—both continuous and batch, as well as the needs of discrete-based manufacturers. The Manufacturing Profile builds on the five concurrent and continuous functions at the core of the NIST Cybersecurity Framework: Identify, Protect, Detect, Respond, and Recover.
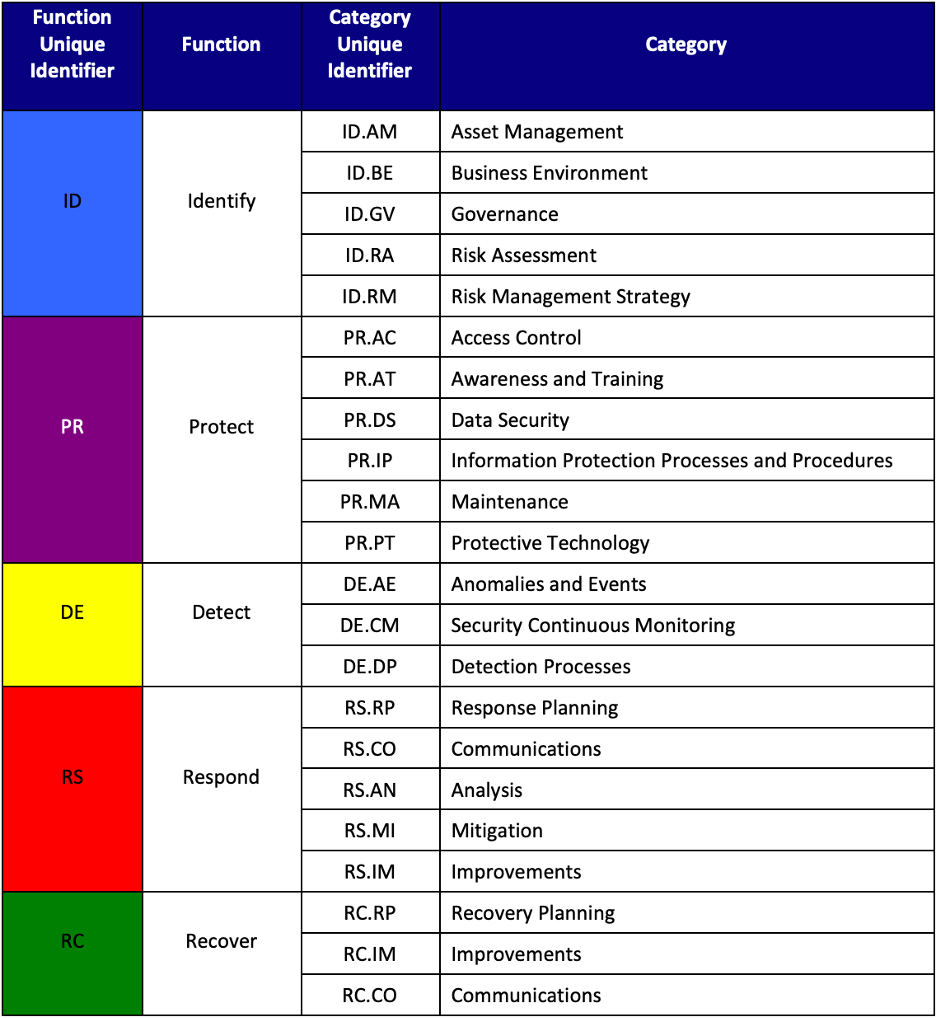
Figure: NIST Cybersecurity Framework - Identify, Protect, Detect, Respond, and Recover
The Manufacturing Profile is designed to support cybersecurity outcomes based on the business needs of each manufacturer, which are determined from selected framework categories and subcategories. The detailed subcategories are derived from the security controls of NIST Special Publication 800-53 (NIST SP 800-53). The Profile provides tailored values for cybersecurity controls for manufacturing infrastructure. Categories and subcategories are created “based on domain-specific relevance, business drivers, risk assessment, and the manufacturer’s priorities.”
Objectives and Functions
The manufacturing business objectives of maintaining human safety, environmental safety, quality of product, production goals, and trade secrets are aligned across functions, categories, and subcategories of cybersecurity objectives. In addition to these, security levels of Low, medium, and High are used to prioritize implementation of the framework. Severity levels can be used to inform a maturity model but should not be confused as a substitute for a maturity model. The former is tactical, and the latter is strategy. The Profile should therefore not be viewed as a maturity model so much as a road map that is progressively more useful to organizations with higher levels of cybersecurity maturity.
For example, the “Asset Management” category and its “Asset Identification” subcategory fall under the framework’s “Identify” function. NIST classifies the automated detection of unauthorized hardware and firmware as a “high” impact task. Clearly, however, the task’s value is higher if it is part of a continuous process of well-documented asset discovery and management than if it is a one-off scan of OT assets.
One of the most important benefits of moving up the maturity curve is the ability to integrate with broader enterprise risk management solutions. There is currently a significant gap between the output of most cybersecurity risk management programs and the input that is required to effectively integrate cybersecurity into traditional enterprise risk management systems. NIST is attempting to address this issue, and in 2020 it released NISTIR 8286: “Integrating Cybersecurity and Enterprise Risk Management (ERM),” which provides a good overview of the issues and some potential solutions.
A Manufacturing Cybersecurity Action Plan
Individual manufacturers’ action plans will, of course, depend on which, if any, regulatory regimes they fall under. Again, in the U.S., this could be the SEC, DoD, FDA, or other agencies depending on what is being manufactured and or to whom it is sold. There is some general guidance, however, that should be considered best practice by any manufacturer.
An obvious first step for an organization, after determining which, if any, regulatory jurisdictions it falls under, is to perform a cybersecurity assessment. In the U.S., manufacturers that are considered critical infrastructure can take advantage of multiple assessment tools developed by CISA. Small and medium-sized manufacturers of any sort can take advantage of the cybersecurity resources for manufacturers developed by NIST as part of its Manufacturing Extension Partnership. These resources include a cybersecurity self-assessment. There also several third-party providers that offer assessment services tailored for OT cybersecurity requirements. Takepoint Research has published an as well as an Industrial Cyber Technology Buyer’s Guide.
High-Level Checklist
At a high level, cybersecurity action plans are fairly similar and would include the following steps. (These steps follow recommendations from the U.S. Nuclear Regulatory Commission.)
|
1. Train and qualify cybersecurity assessment team (CSAT) |
|
|
2. Identify critical systems and critical digital assets |
|
|
3. Develop cybersecurity defensive strategy |
|
|
4. Implement cybersecurity defense-in-depth architecture |
|
|
5. Establish cybersecurity program policies/ procedures |
|
|
6. Perform and document the cybersecurity assessment described in the cybersecurity plan |
|
|
7. Implement security controls not requiring plant modification |
|
|
8. Implement security controls requiring plant modification |
|
Lessons Learned from Manufacturing Cybersecurity Incidents
Resiliency Planning
When developing a cybersecurity action plan, it is important to consider how it fits into an organization’s broader resiliency planning. The U.S. National Security Agency (NSA) and the U.S. Cybersecurity & Infrastructure Security Agency (CISA) strongly recommend having a resiliency plan in place to deal with potential cyber disruption. Those agencies suggest that organizations need an OT resilience plan that allows them to:
The CMMC model framework organizes cybersecurity processes and practices into domains that are mapped across five maturity levels.
- Immediately disconnect any systems from the internet that do not need internet connectivity for safe and reliable operations. Additionally, implement compensating controls for systems where connectivity cannot be safely removed.
- Be prepared to operate processes manually should ICS infrastructure become unavailable or should it need to be deactivated due to cyberattack.
- Remove any additional functionality that could induce risk and increase the attack surface area.
- Identify and understand system and operational dependencies.
- Restore OT devices and services in a timely manner.
- Create and safely store gold-copy backup resources, such as firmware, software, ladder logic, service contracts, product licenses, product keys, and configuration information.
- Periodically test and validate data backups and processes in the event of data loss due to malicious cyber activity.
For manufacturers, creating and understanding an accurate “as-operated” map of OT connectivity is critical to initiating a risk reduction cybersecurity plan. Again, the NSA and CISA recommend the following actions to identify assets:
Your Risk Reduction Cybersecurity Action Plan
Click on each item to cross it off your maritime cybersecurity to-do list. Select the expander next to each item to get more information.
Document and validate an accurate “as-operated” OT network map.
- Use vendor-provided tools and procedures to identify OT assets.
- Use publicly available passive network mapping tools.
- Physically walk down to verify the OT infrastructure map.
Create an asset inventory.
-
Include OT devices assigned an Internet Protocol (IP) address.
-
Include software and firmware versions.
-
Include process logic and OT programs.
-
Include removable media.
-
Include standby and spare equipment.
Identify all communication protocols used across the OT networks.
- Use vendor-provided tools and procedures to identify OT communications.
- Use publicly available passive network mapping tools.
Investigate all unauthorized OT communications.
- Use vendor-provided tools and procedures to identify unauthorized and/or unknown OT communication.
- Have a process and procedure for the investigation of identified unauthorized communications.
- Use vendor-provided tools to explicitly deny unauthorized OT communications.
Catalog all external connections to and from the OT networks.
-
Include all business, vendor, and other remote access connections.
-
Review service contracts to identify all remote connections used for third-party services.
The NSA and CISA recommend the following resources for help in understanding and evaluating cyber risk on “as-operated” OT assets:
-
Vendor-specific cybersecurity and technical advisories (Examples for technology and services.)
-
DHS – CISA Advisories. (Available at https://us-cert.cisa.gov/ics/advisories)
-
MITRE5 Common Vulnerabilities and Exposures (CVE8) for both IT and OT devices and for system software. (Available at https://cve.mitre.org)
-
National Institute of Standards and Technology – National Vulnerability Database. (Available at https://nvd.nist.gov)
With this baseline of risk information in hand, organizations should perform the following tasks:
-
Implement mitigations for each relevant known vulnerability, whenever possible, such as patches and offsetting security controls.
-
Audit and identify all OT network services that are being used.
-
Use vendor-provided programming and/or diagnostic tools and procedures.
-
Implement a system monitoring program to enable system anomaly detection.
-
-
Log and review all authorized external access connections for misuse or unusual activity.
-
Monitor for any unauthorized controller change attempts.
-
Implement integrity checks of controller process logic against a known good baseline.
-
Where possible, disable remote program mode for process controllers while in operation.
-
Lock or limit set points in control processes.
-
Conclusions
The good news for critical manufacturers is that there is a large and growing set of resources designed to improve cybersecurity in this sector. Manufacturers globally should expect more cybersecurity oversight as Industry 4.0 technologies increasingly become commonplace and expand traditional attack surfaces. It is critical that manufacturers remain engaged with public and private organizations that are driving cybersecurity regulation and determining best practices in this sector. The expectation should be that additional regulation is coming, but it is likely to continue to be applied piecemeal, particularly in the United States.
Manufacturers should be focusing on creating a specific OT cybersecurity plan, be integrating OT and IT cybersecurity efforts as much as possible, and looking to bundle OT cybersecurity more fully into broader enterprise risk management strategies. Business considerations are driving a wholesale revolution in manufacturing technology deployment, and OT cybersecurity strategy needs to be viewed as a foundational core competency within manufacturing organizations.
Resources
- Critical Manufacturing Sector Cybersecurity Framework Implementation Guide
https://us-cert.cisa.gov/sites/default/files/c3vp/framework_guidance/critical-manufacturing-framework-implementation-guide-2015-508.pdf - Critical Manufacturing Sector Security Guide
https://www.cisa.gov/sites/default/files/publications/Critical_Manufacturing_Sector_Security_Guide_07012020.pdf - Critical Infrastructure Vulnerability Assessments
https://www.cisa.gov/critical-infrastructure-vulnerability-assessments - EU Cybersecurity Certification Framework
https://ec.europa.eu/digital-single-market/en/eu-cybersecurity-certification-framework - ENISA Good Practices for Security of Internet of Things in the context of Smart Manufacturing
https://www.enisa.europa.eu/publications/good-practices-for-security-of-iot - ENISA Industry 4.0 Cybersecurity: Challenges & Recommendations
https://www.enisa.europa.eu/publications/industry-4-0-cybersecurity-challenges-and-recommendations - Industry 4.0 A New Definition of Manufacturing?
https://www.agcs.allianz.com/content/dam/onemarketing/agcs/agcs/grd/AGCS-GRD-1-2016-EN.pdf - NIST Cybersecurity Framework
https://www.nist.gov/cyberframework - NIST Integrating Cybersecurity and Enterprise Risk Management (ERM)
https://www.nist.gov/publications/integrating-cybersecurity-and-enterprise-risk-management-erm - NIST Manufacturing Profile
https://www.nist.gov/publications/cybersecurity-framework-manufacturing-profile-0 - NIST MEP Cybersecurity Self-Assessment Handbook
https://nvlpubs.nist.gov/nistpubs/hb/2017/nist.hb.162.pdf - NIST MEP Manufacturers Guide to Cybersecurity for Small and Medium-Sized Manufacturers
https://www.nist.gov/system/files/documents/2019/11/14/mepnn_cybersecurity_guide_10919-508.pdf - NSA and CISA Cybersecurity Advisory Reduce Exposure Across all Operational Technologies and Control Systems
https://media.defense.gov/2020/Jul/23/2002462846/-1/-1/1/OT_ADVISORY-DUAL-OFFICIAL-20200722.PDF - Managing a Cyber Attack on Critical Infrastructure
https://www.insaonline.org/wp-content/uploads/2018/08/INSA-Managing-Cyber-Attack-Critical-Infrastructure.pdf - Reference Architecture Model for Industry 4.0 (RAMI4.0)
https://www.zvei.org/fileadmin/user_upload/Presse_und_Medien/Publikationen/2015/april/Das_Referenzarchitekturmodell_Industrie_4.0__RAMI_4.0_/ZVEI-Industrie-40-RAMI-40-English.pdf - U.S. Critical Manufacturing Sector-Specific Plan – 2015
https://www.cisa.gov/publication/nipp-ssp-critical-manufacturing-2015 - U.S. DoD Maturity Model
https://www.acq.osd.mil/cmmc/docs/CMMC_Model_Main_20200203.pdf
https://www.acq.osd.mil/cmmc/docs/CMMC_Model_Appendices_20200203.pdf - U.S. Federal Communications Commission (FCC) Cybersecurity Guide
https://www.cisa.gov/sites/default/files/publications/FCC%20Cybersecurity%20Planning%20Guide.pdf - U.S. Nuclear Regulatory Commission Template for Cybersecurity Plan Implementation Schedule
https://www.nrc.gov/docs/ML1100/ML110060097.pdf

